Hacker collective LightBasin used a new Unix rootkit to steal financial data from ATMs in order to carry out fraudulent transactions.
The activity was discovered by security expert Mandiant. According to the researchers, the LightBasin hackers targeted customers of banks The collective focused on bank card fraud and compromising important financial systems such as ATMs.
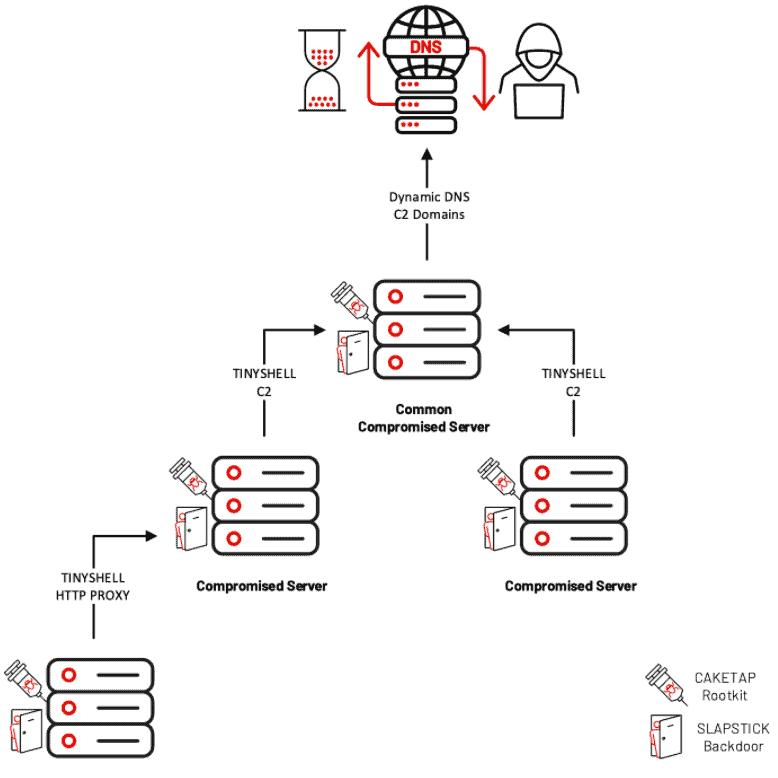
The hackers developed a Unix-based rootkit that affects ATMs, also known as Caketap. The rootkit is primarily deployed on systems running on the Oracle Solaris operating system.
Caketap
Caketap malware hides various network connections, processes and files while it installs hooks into the system functions of an affected ATM. It allows ATMs to receive remote commands and configurations.
Once the hackers control the ATM, they can intercept data from bank cards and associated PINs. Stolen data is used for malicious and fraudulent transactions.
Hiding presence
In addition to stealing the financial data, Caketap malware causes valid messages from non-fraudulent Primary Account Numbers (PANs) to be stored internally. Messages are sent to the HSM to avoid impeding routine customer transactions, thereby remaining undetected. At this time, there’s no known solution to ATM attacks based on the malware.