Cybercriminal organizations have the same ambitions of growth as their legitimate counterparts. The Sysdig Threat Research Team (TRT) has spotted one that’s scaling up fast: CrystalRay, which makes grateful use of open-source software to target its victims.
CrystalRay aims to attack victims with all too familiar cybercriminal motivations in mind. In addition to stealing credentials and installing cryptominers, the group sells access to its victims via the dark web. Since the Sysdig team first noticed CrystalRay in February, the group has increased the number of affected organizations tenfold to 1,500 worldwide.
The group operates globally, but organizations in the U.S. (30 percent) and China (18 percent) are the most affected. CrystalRay has also targeted networks in Germany, the United Kingdom, France, the Netherlands, Japan and Russia, among many others.
No packets sent
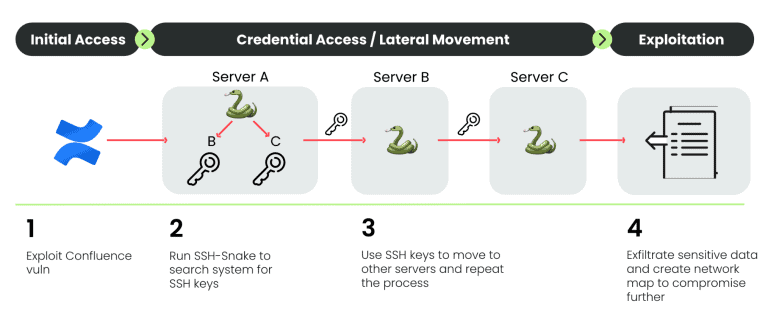
CrystalRay’s attack path is through Atlassian Confluence, a workspace offering which has suffered multiple vulnerabilities in the recent past. To do so, the group uses the penetration testing tool SSH-Snake, which its GitHub maintainer says is “intended for hacking purposes” but can also be deployed by sysadmins to monitor their own infrastructure and network. It is a self-propagating “worm” that can burrow deep into a corporate network, making use of configuration errors and vulnerabilities along the way.
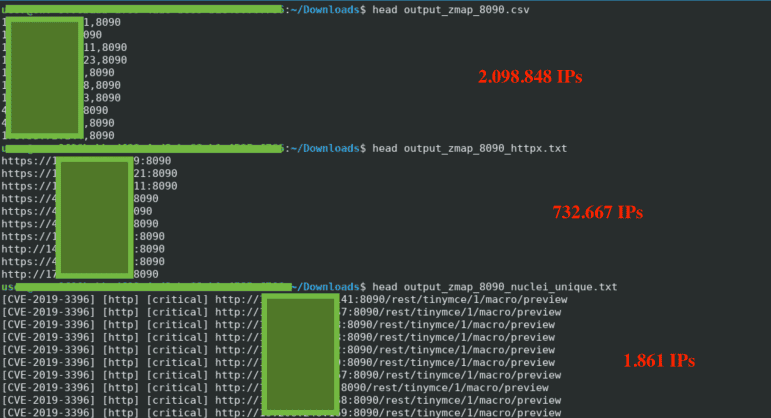
Its targeting of victims is less precise than that of a ransomware attack or whenever a state-sponsored threat actor seeks to infiltrate a target, Sysdig points out. However, the tactic is more precise than a botnet thanks to it picking a specific series of IP addresses depending on the country involved. Once a network is hit, CrystalRay uses ASN, another open-source tool available on GitHub. It makes open-source intelligence (OSINT) simple and human-readable and acts as a command line tool for network data. It queries Shodan for things like URLs, a set of IP addresses or hostnames. With this, CrystalRay finds the necessary vulnerabilities, if any exist. Sysdig highlights that all this takes place without ever sending a packet to the victim.
Best of breed
From the broader choice of open-source tools, it appears that CrystalRay has found the most effective options. For example, it uses zmap that detects specific ports for vulnerable services, which is less likely to raise false alarms than nmap, making it suitable for large-scale scans. The Nuclei scanner also helps attackers find exploitable vulnerabilities inside a given network. In fact, CrystalRay does what organizations themselves would have wanted to do before: detect cyber dangers in detail.
An example of a common CrystalRay payload is Sliver, intended for Red Teaming i.e. security testing. In other words, the group deploys the very tools that legitimate researchers have at their disposal and would ideally use all the time if they do, indeed, have the time available to do so.
Beyond exploitation
As mentioned, CrystalRay makes grateful use of SSH-Snake, an open-source tool available since January. This helps the group exfiltrate sensitive data and move between servers. A handy SSH-Snake overview shows which users, hosts and/or destinations have been detected. Querying old bash commands speeds up this process, thanks in part to the GitHub repositories all-bash-history and linux-smart-enumeration.
However, the impact of these cybercriminals does not stop there. Sysdig TRT saw that CrystalRay was also trying to move to other platforms, including cloud providers. This all happens automatically, after which the group resells the credentials it has obtained. The transactions happen not only through the dark web but also through Telegram.
In addition, CrystalRay earns some extra money on the back of their victims in the form of crypto coin mining. This isn’t that much of a financial boon, at least: thanks to two different mining programs, the group brings in about $200 a month. It does automatically remove other cryptominers that may already be on the corporate network, so rival cybercriminals are out of luck.
Test before you get caught
Sysdig notes that it is often necessary for applications to be connected to the Internet. Also, vulnerabilities are simply a common occurance. So in addition to patching, the key is to get ahead of these automated attacks or at least gain visibility into them. It must be possible for organizations to see at any time through camera/runtime detection whether they have been compromised.
In addition, the obvious thing to do (where possible) is to follow CrystalRay’s “good example”: testing one’s own environments via open-source tools. The same configuration errors and vulnerabilities that this group exploits can be detected with tools available online and fixed before trouble appears.
Also read: Gigantic DDoS attack of 840 Mpps mitigated