North Korean hackers from Lazarus have launched two new sophisticated attacks. Their methods rely on open-source tools and frameworks to install malware, Cisco research has shown.
According to the researchers, the hackers from the Lazarus group, known for the notorious WannaCry ransomware attacks in 2017 and other cyber incidents, are doing quite a bit to use new advanced attack capabilities. This time, the hackers are mostly abusing open-source tools and frameworks to set up their attacks in the initial phase.
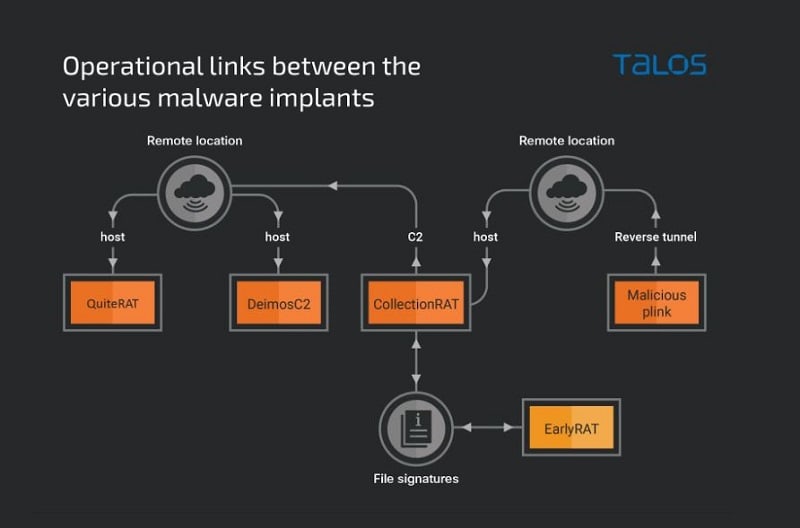
DeimosC2
The experts at Cisco, as well as Trend Micro, found that the Lazarus hackers are now heavily abusing the open-source framework DeimosC2 for initial and persistent access. The implant used was a Linux ELF binary used primarily to access Linux servers.
DeimosC2 is an open-source GoLang-based C2 framework and provides support for various RAT capabilities. As a result, the open-source framework offers roughly the same functionality as popular C2 frameworks CobaltStrike and Silver.
The implant used does still show many default settings, which should suggest that North Korean hackers are still learning how to use the framework.
Another abused open-source tool is the reverse tunneling tool PuTTY Link (Plink).
CollectionRAT
The open-source tools and frameworks are primarily used to spread new remote access Trojan malware. In particular, this involves the CollectionRAT trojan, which the hackers have already used.
This malware is part of a family of malware, which also includes the trojans QuiteRAT and the older MagicRAT. Among other things, this malware targets Zoho’s ManageEngine SaaS solutions and, more specifically, a vulnerability in the app ServiceDesk. This would have been patched back in November of 2022, but there are still many other unpatched systems.
Tip: Malvertising is becoming an increasingly dangerous form of cybercrime