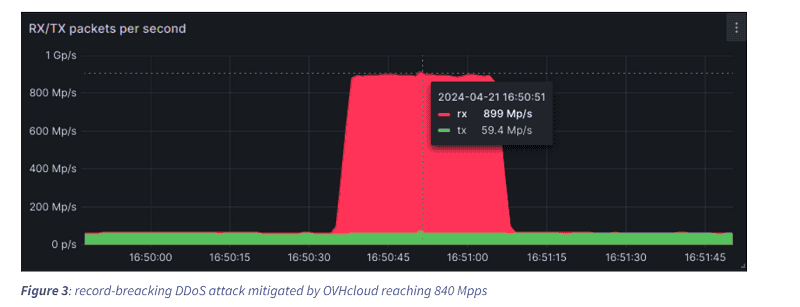
OVHcloud managed to mitigate a DDoS attack totalling 2.5 Tbps on its systems in May this year. It peaked at 840 million packets per second (Mpps). Interestingly, most of the attacks took place via botnets from compromised core MikroTik routers.
According to the French cloud and hosting provider, DDoS attacks with 1 Tbps of malicious data traffic peaks are the rule rather than the exception these days. Recently, OVHcloud even suffered a record DDoS attack of 840 Mpps, totalling 2.5 Tbps of data traffic. This was the highest bit rate the company has faced in the past year and a half.
The malicious traffic originated from five thousand source IP addresses. Two-thirds of the packets sent were routed through only four Points of Presence (PoPs), all located in the United States, three of which were on the West Coast. Who was behind the DDoS attack is not known.
According to the researchers, sending a large amount of malicious traffic through a limited bandwidth of internet infrastructure makes these particular DDoS attacks more powerful and more difficult to counter.
Routers from MikroTik
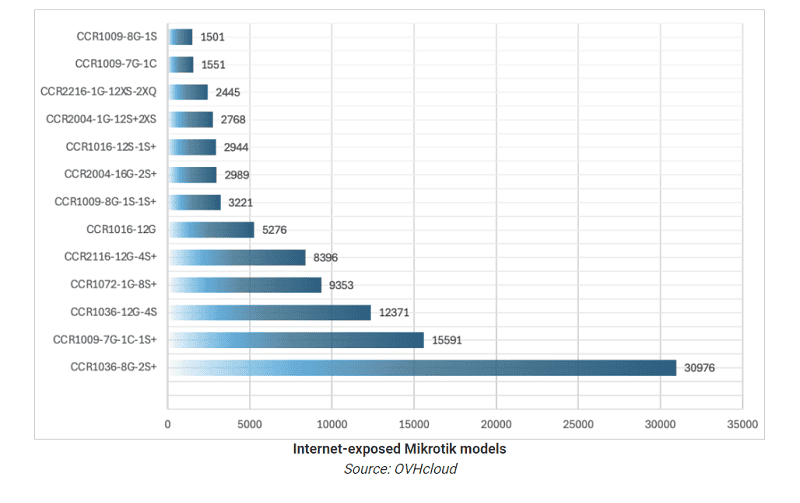
The investigation further reveals that botnets of compromised core routers from MikroTik were used for the massive DDoS attack. These Cloud Core Router (CCR) devices are designed for high-performance networking.
This involved the MikroTik models CCR1036-8G-2S+ and CCR1072-1G-8S+, which are often deployed as smaller to medium-sized network cores.
Vulnerable due to old firmware
The abused core routers found often had an online visible interface, were running on outdated firmware, and were thus susceptible to known vulnerabilities. OVHcloud suspects that the hackers abused the MikroTik RouterOS’s “Bandwidth Test” feature. This feature is designed to perform stress-testing of the network throughput of the affected core routers and thus generate high volumes of packets.
In total, as many as 100,000 vulnerable MikroTik core routers were found to be susceptible to being abused by hackers for DDoS attacks. These routers have 36 core CPUs on board by default, allowing them to create giant malicious botnets capable of sending billions of packets per second.
Calculations by OVHcloud show that if just 1 per cent of the nearly 100,000 vulnerable MikroTik core routers were used in a botnet, this botnet would be capable of sending 2.28 billion packets per second (Gpps).
Not first time
This is not the first time MikroTik devices have been the source of a malicious botnet. It was previously the case with the Mēris botnet. So despite advice from the hardware specialist to update its core routers with, for example, the latest firmware versions, this has not happened often.
OVHcloud has notified MikroTik of its findings but has not yet received a response.
Also read: DDoS attacks are getting easier and more complex at the same time