Researchers from security specialist Worldfence discovered millions of attacks on outdated versions of WordPress plugin Tatsu. Attackers are dropping malware with ease.
The newly found attacks target a remote code execution vulnerability in the WordPress plugin Tatsu. Tatsu is a no-code page builder that allows users to build WordPress websites. Hackers can install so-called droppers on vulnerable websites. Droppers are software packages that, in this case, install malicious scripts in folders with random names.
High attack volume
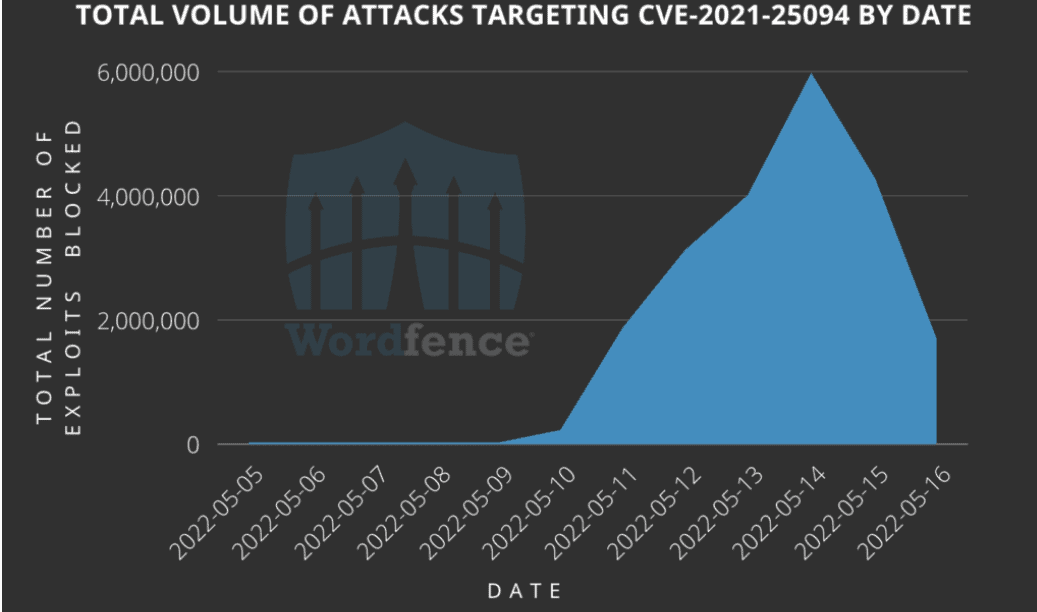
Worldfence researchers indicate that millions of attacks have been carried out since the vulnerable WordPress plugin’s discovery. On 14 May, the attack volume hit a peak of 5.9 million attacks against 1.4 million websites.
Patch in version 3.3.13
Tatsu already patched the vulnerability in version 3.3.13 of the plugin. An earlier version (3.3.12) tried to address the problem found, but failed to completely disable the vulnerability. Users are therefore urged to upgrade to the latest version. The exact amount of websites running unpatched versions is unknown. Estimates go as high as 50.000.
Tip: Vulnerability in popular WordPress plugin affects millions of websites