SentinelOne recently discovered a supply chain attack that uses components of the Rust programming language. The attack involves a malicious ‘crate’ in the Rust dependency community repository.
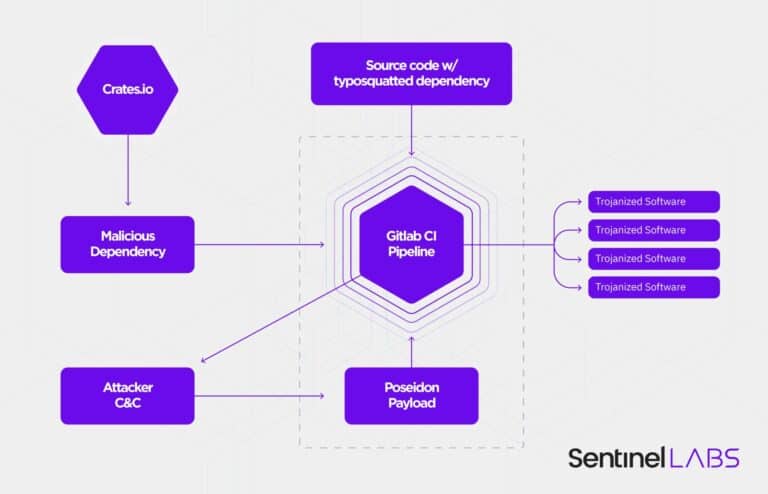
According to SentinelOne, hackers used a so-called CrateDepression attack to introduce a malicious crate in cartes.io, the Rust dependency community repository. The crate is disguised as ‘rust_decimal’, a dependency used for financial calculations. As many as 15 versions of the malicious crate were discovered.
GitLab CI pipelines vulnerable
The attack introduced typosquats that allow infected machines to be inspected for the GITLAB_CI environment variable. This variable is needed to identify the GitLab CI pipelines, which are abused in a later stage.
After identifying the pipelines, the hackers extract a payload. The payload is written in Go and related to ‘Poseidon’, an agent. The agent allows hackers to attack macOS and Linux systems.
Supply chain attacks
According to SentinelOne, the attack allows large-scale supply chain attacks to take place at a later date. Attacks on cloud software generally indicate supply chain attacks, which aim to affect as many victims as possible.
Tip: How do you interpret the results of MITRE ATT&CK evaluations?
