CISA and ACSC shared an overview of the 11 most common malware variants of 2021. Most variants have been active for years.
The list includes ransomware, remote access trojans (RATs), banking trojans and information stealers. Most variants have been active for more than five years. Cybercriminals constantly update the malware to exploit new systems and avoid detection.
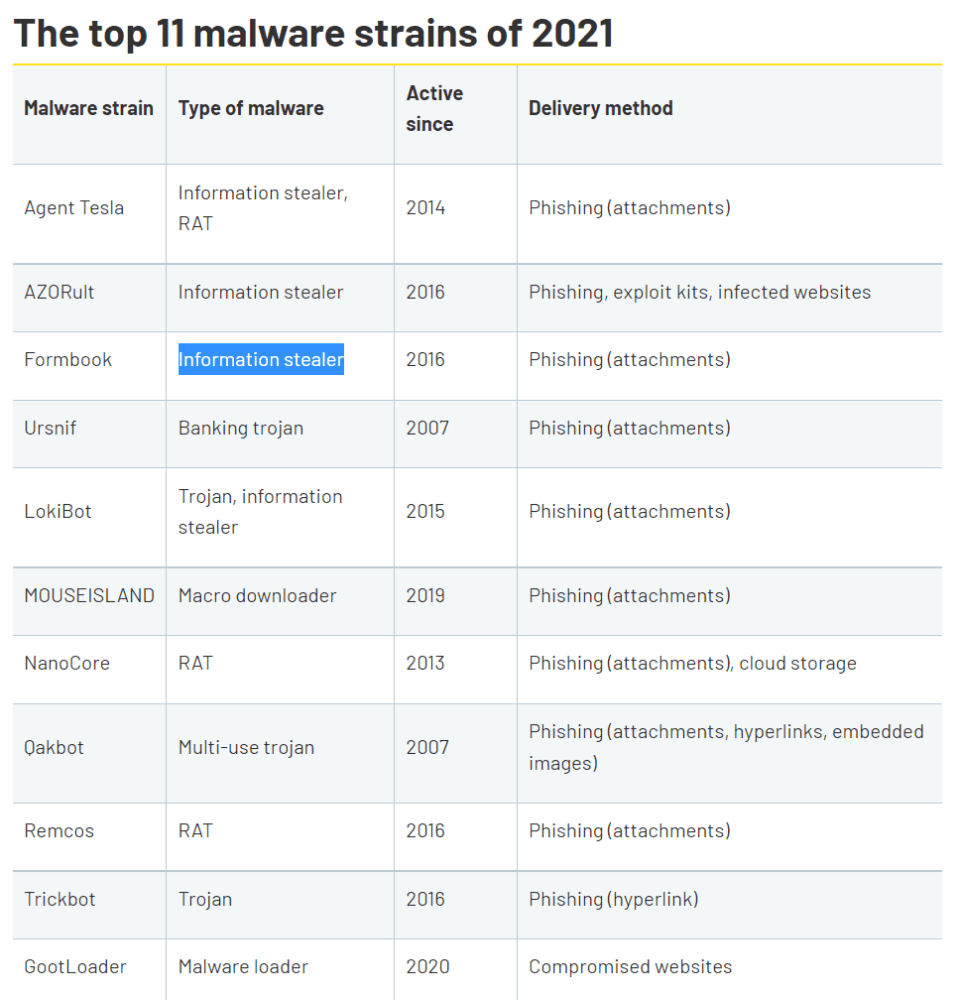
Qakbot (Qbot) and Ursnif have the longest history. Ursnif was first discovered in 2007. Cybercriminals primarily spread the banking trojan through email attachments. Qakbot popped up in 2007 as well. Cybercriminals spread the trojan with attachments, hyperlinks and embedded images. Devices infected with Qakbot regularly end up in bots. According to CISA, Russian cybercriminals use the botnets for ransomware attacks.
GootLoader and MOUSEISLAND
The latest variants are GootLoader (2020) and MOUSEISLAND (2019). Over the past two years, GootLoader grew to become a multi-payload malware platform. Cybercriminals use the platform to gain initial access to various environments. Early payloads are typically spread through search engine poisoning. The method involves faking a popular website and advertising the URL through Google’s search results.
MOUSEISLAND is a macro downloader used to abuse VBA macros in Microsoft Office, among other things. We expect the malware to disappear from the list next year. Microsoft recently disabled VBA macros in Office by default, reducing MOUSEISLAND’s attack surface.
Security measures
The list was issued by CISA and ACSC. CISA is the national security authority of the United States. The ACSC plays a similar role in Australia. The CISA and ACSC published a joint security advisory with security measures against the malware variants.
