Intel introduced a new chip security technology at the Black Hat conference. Tunable Replica Circuit (TRC) should prevent cyberattacks on hardware systems. The technology was added to its Alder Lake server processors.
Intel developed the technology to improve hardware security against cyberattacks. In addition to software vulnerabilities, hackers increasingly seek vulnerabilities in hardware such as servers. When found, hardware components can be controlled and abused to access data.
TRC Technology
According to Intel, the Tunable Replica Circuit (TRC) technology automatically detects various attack types on hardware systems, including attacks that target the ‘clock pins’ of processors. These small wires control the clock speed of processors.
The technology detects attacks that cause processor errors using electromagnetic waves and changes in the processor’s power supply. TRC technology monitors the clock generator, which coordinates the operation of transistors by manipulating current. This clock generator is built-in throughout the processor and optimizes all computational operations.
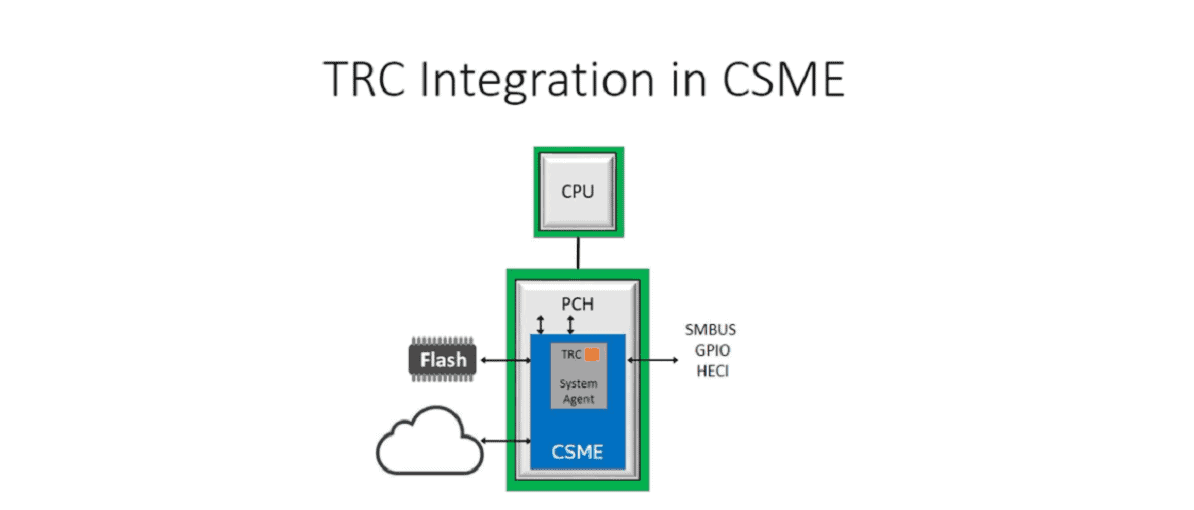
TRC ultimately detects small changes in a processor’s timing. These changes can indicate a cyberattack. The technology was added to the Intel Converged Security and Management Engine (CSME).
Tricky development process
TRC was originally developed by Intel Labs to detect general technical problems in processors. The technology was recently repurposed to detect hardware attacks.
According to the chip manufacturer, the development process has been challenging. TRC’s accuracy proved hard to guarantee. Its developers had to avoid detecting general processor errors and delivering too many false negatives.
Added to Alder Lake processors
Intel added TRC to its new Alder Lake processors. The technology wasn’t built directly into the processors, but delivered through an external component: the Plaftorm Controller Hub (PCH). The PCH is a chipset installed in hardware systems alongside Intel processors to perform various security tasks like firmware scans. Other Intel processor security technology includes SGX, which stores data in isolated processor areas (enclaves) to detect cyberattacks targeting firmware.