Microsoft warned of malicious OAuth applications attacking cloud users by hijacking Exchange servers. The cybercriminals aim to spread large amounts of spam.
According to Microsoft, cybercriminals have launched credential-stuffing attacks against users with Exchange accounts that lack multi-factor authentication (MFA). The users attacked reportedly failed to adequately secure their management accounts, which allowed the cybercriminals to gain initial access.
After gaining access, the attackers created malicious OAuth applications. This application added an inbound connector to the email server. As a result, the cybercriminals were able to send large amounts of spam from the domain of the attacked account.
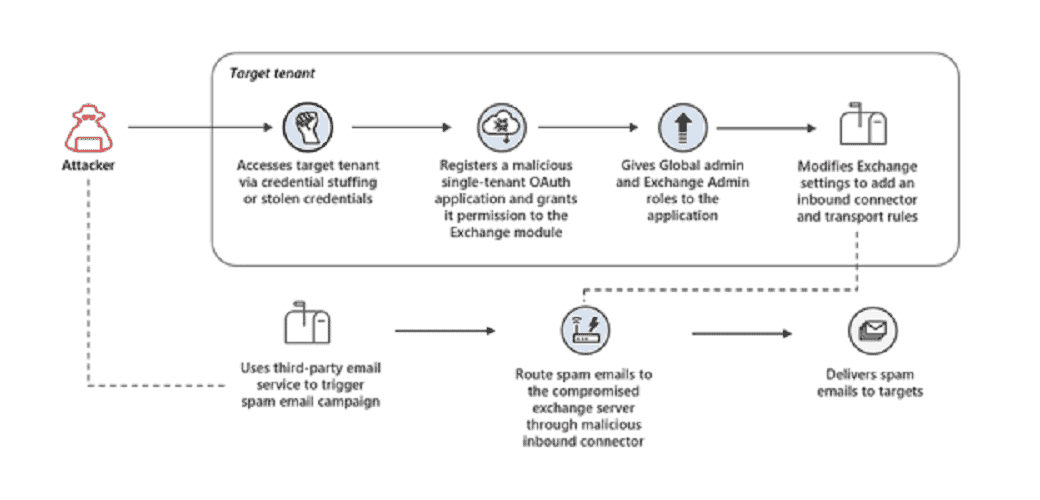
The cybercriminals mostly sent phishing emails, attempting to trick victims into paying recurring subscriptions for lotteries. After the hack was discovered, all relevant applications were removed, customers were informed and remedies were implemented.
OAuth application attacks
According to Microsoft researchers, the incident shows that cybercriminals are increasingly abusing OAuth applications for consent phishing. Victims are tricked into permitting malicious OAuth applications to access cloud services. In other cases, state-sponsored cybercriminals abused OAuth applications for backdoors, phishing and malicious redirects.
Mitigation
Microsoft advises Exchange server users to implement MFA on all accounts and at all times. In addition, users are advised to implement conditional access requirements and continuously monitor access to (cloud-based) Exchange environments.
Furthermore, companies can implement default security settings in both Exchange and Azure AD. These measures should further protect the identity platform with preconfigured settings like MFA and privileged access.
