
KnowBe4 evolves from security training to human risk management
Security awareness training has come a long way from its origins as a compliance checkbox. Today, it’s evol...

Security awareness training has come a long way from its origins as a compliance checkbox. Today, it’s evol...
Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.

The personal data of tens of thousands of Eindhoven University of Technology students and employees were capt...

A misconfigured Azure Blob Storage endpoint caused unauthorized access to large amounts of Microsoft customer...

Sophos unveiled new third-party integrations with its managed detection and response (MDR) service to improve...

Security researchers from SentinelOne have discovered a new malware cluster dubbed WIP19. The malware variant...

FortiSASE integrates cloud-delivered SD-WAN connectivity with cloud-delivered security (SSE). This week F...
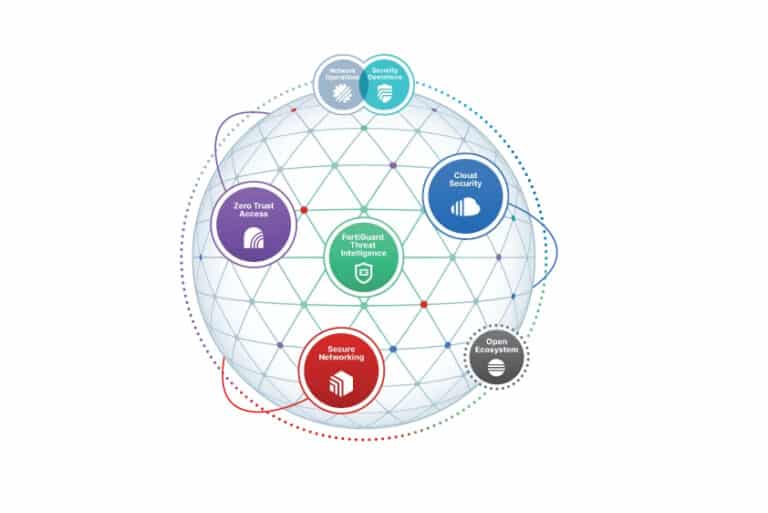
Increasing complexity of organizations' environments poses questions that a security mesh architecture can an...

Exabeam introduced New-Scale SIEM, a cloud-based SIEM environment. According to the vendor, the solution "det...

Data loss prevention is often ineffective. Researchers from security firm Zscaler warn that organizations' da...

Researchers warn of a vulnerability in Microsoft's Office 365 Message Encryption feature. Cybercriminals can ...

A 2.5 Tbps distributed denial-of-service (DDoS) attack recently hit Wynncraft, a popular Minecraft server. Ac...