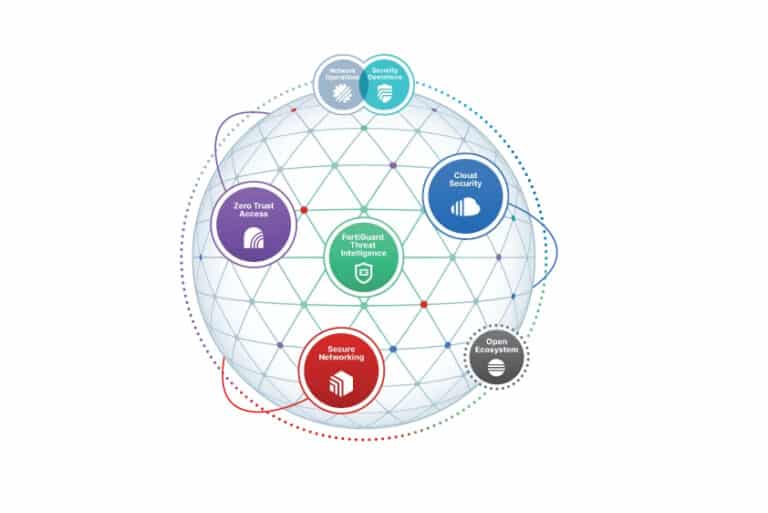
Increasing complexity of organizations’ environments poses questions that a security mesh architecture can answer.
The number of cybersecurity solutions within organizations is constantly increasing. They have to be, because the environments of these organizations are also becoming increasingly complex. Think of the move to the cloud, where not only the applications of organizations but also the infrastructure (partially) moves to the cloud. This in turn results in a hybrid environment that obviously also needs to be as secure as possible. Something similar can be said of Work From Anywhere developments that have gained momentum in recent years. In addition, the number of cybersecurity tools also constantly increases. The addition of EDR and XDR, sometimes on top of existing EPP solutions is one example. Another example is the emergence of API security.
Besides the developments on the “good” side of cybersecurity, the developments on the “bad” side also create the necessary challenges. This is particularly true for the the speed at which the threat landscape changes. This is virtually impossible to keep up with for organizations that have to work with all of the separate solutions they have invested in. Of course, the chronic shortage of personnel who can handle these solutions doesn’t help either. AI/ML can obviously help ease some of the burden on those personnel. However, the attackers also use this, so this will partly cancel each other out.
Time for a cyber security mesh architecture
The above issues are more or less a given, indicates Ton Sips. He is SE Manager at Fortinet in the Netherlands and mainly speaks to very large enterprises, specifically multinationals headquartered in the Netherlands. There, the consequences of the complexity outlined above are clearly visible. Organizationally, these customers also create additional complexity. They often have a rather compartmentalized approach, with a separate silo for firewall, proxy, email and so on.
The big question, of course, is how these types of large enterprises with an average of many dozens of security solutions but also slightly smaller organizations can remain secure. Sips talks about an average of 45 security solutions per organization. It is impossible to deploy and manage them all separately. At least, not in such a way that you get the optimal result out of them. In other words, you are more vulnerable than necessary. In order to get the most out of an organization’s investment into cybersecurity, now more than ever organizations should seriously consider a switch to a new security architecture.
Gartner recently started talking about CSMA, or CyberSecurity Mesh Architecture. The idea behind this is that solutions (and devices) are part of a new architecture. Thanks to the connections and integrations enabled by that architecture, the individual components reinforce each other. At the end of the day, this should ensure that attacks can be repelled faster and better, the attack surface becomes smaller and thus security overall improves.
Fortinet’s foresight
So CSMA is the term used by Gartner. Fortinet calls it Security Fabric and has been working on this for 10 years. The beginning of the Fortinet Security Fabric lies in connecting security and networking, Sips points out. In Fortinet’s view, the network is an extension of the firewall. This makes Fortinet quite special in the market. Traditionally, things like switching and wireless are not seen as part of cybersecurity, he points out. That is now changing, by the way. Most network vendors are also pushing the security angle pretty hard these days. They approach it from the other side, though. Whereas Fortinet was a security vendor that started to integrate networking, it is the other way around for network vendors. No doubt that has repercussions on the end product as well.
The Security Fabric, meanwhile, has long ceased to be limited to connecting security and networking. Over the past decade, Fortinet has added more and more components. As an example of how the Security Fabric can add value, Sips cites the link between the mail solution and the firewall. Because these two components are in contact with each other, the mail solution shares the detection of dangerous content with the firewall. This escalates the detection and resolution of an attack with that content toward the firewall, so to speak. The firewall can label this content as dangerous for the entire environment. Even if an employee accesses the same content via a different route, the firewall detects this and takes action.
Integration makes Security Fabric broadly relevant
Fortinet primarily focuses on three topics when it comes to the Security Fabric: visibility, automation and integration. From the beginning it has been Fortinet’s intention to enable interconnections between as many components as possible, and not to do this (as tradition has it) through a SIEM. This obviously includes the 60 products Fortinet has in its portfolio. But there are also more than 450 so-called Fabric partners. These integrate with the Security Fabric and thus also with Fortinet’s products and solutions. Remarkably, there are also competing vendors among them. That’s a good thing as far as we are concerned, because ultimately that only benefits the customers, who haven’t all standardized on Fortinet.
Incidentally, the degree to which the Fabric partners’ solutions integrate does vary. That’s not for Fortinet alone to determine. For some things, it builds connectors itself, but third parties sometimes do this themselves. Fortinet will help with that if desired, but it is up to that party to determine how deep to integrate. In theory, there is no limit to how deeply a solution can integrate with a Fortinet product via the Security Fabric, Sips points out. Within FortiOS, the operating system of most of Fortinet’s products, every action in the GUI is a call to the API. That means basically everything is available for integration.
Automation the next step
When it comes to automating actions within the Security Fabric, Fortinet has also taken considerable steps forward. About four years ago, it started with so-called automation stitches. These make it possible to take automated action across the Security Fabric. These automation stitches are available for all products in Fortinet’s portfolio.
It is also important to point out that within the Security Fabric the indicators of compromise are shared fully automatically. This obviously benefits the speed of detection and response. Automated removal of users is obviously a lot more difficult. There is still some manual work involved, Sips points out. According to him, it is important for an organization to find the balance between what needs to be done automatically and what still needs to be done manually. He also tells us, however, that the risks of automation for most basic tasks are so low that he would always turn it on.
Sips also realizes that automation doesn’t go down well everywhere. Especially in the OT world, people are sometimes reluctant on this point, he notes. This while, according to him, it is fairly easy to create a security layer in OT because you have a much better overview there than in an IT environment. Still, he currently sees more automation within IT, although OT is catching up.
Who should consider Security Fabric?
Basically, Fortinet Security Fabric is suitable for any organization, Sips argues. All those organizations are modernizing and getting a more distributed landscape. Connecting switching and wireless with the firewall is still a common way to get started with the Security Fabric. But organizations will also get added value from the Security Fabric if it has many employees who work away from the office and need to set up a lot of VPNs. In larger organizations it can sometimes be more difficult to get started with it, though. There you not only see silos within the organizations itself. The distribution of different silos among different system integrators can also present challenges for those larger organizations.
At Fortinet, by the way, they do not consider the Security Fabric to be the initial goal. Sips calls it the dot on the horizon, which organizations can work toward bit by bit. Nor do they have any set reference architectures for the Security Fabric. Fortinet introduces the Security Fabric when it fits a customer’s challenge. That is, there are many inroads into the Security Fabric conversation. That is a big advantage for Fortinet. As far as we can see, it is the broadest security vendor in the market. It has an answer in its broad portfolio for most questions customers ask them. The Security Fabric will then automatically become part of the conversation. Because a Security Fabric is interesting for all organizations and even inevitable in the long term, is the point Fortinet and Sips want to make. In that case, you’d better start soon.
TIP: Some time ago we published an article about FortiEDR, one of Fortinet’s security components with integration into its own Security Fabric. You can read that article via this link.