Traditional EPP is no longer enough to protect endpoints. Organizations should all move towards EDR. Fortinet has an interesting proposition with FortiEDR. This EDR solution has a few extras that you won’t find elsewhere, or hardly at all.
Malware is becoming increasingly advanced and aggressive. It is also becoming increasingly complex in terms of its construction and execution. Attackers are using much more cunning ways to get in these days. The SolarWinds and Kaseya attacks are good examples of this. In these cases, attackers used vulnerabilities in those systems to get into customers environments. This no longer involves entering via a file or executable, but via general vulnerabilities and systems within the supply chain.
According to Stef Luijken, Manager of Systems Engineering and subject matter expert on FortiEDR at Fortinet, this modern way of attacking has a fundamental impact on how to approach endpoint security. Traditional EPP is no longer sufficient to protect systems properly, he argues. With traditional EPP Luijken refers to the ‘old-fashioned’ antivirus programs that run on systems and check on the basis of signatures whether everything is in order. That doesn’t stop modern threats. They can also be found in legitimate systems, as we saw with SolarWinds and Kaseya. However, a threat can also come from a legitimate application such as Adobe Reader. This makes relying on signatures obsolete.
Not signatures, but behavior
If signatures are no longer sufficient in protecting endpoints, what is? That is where EDR comes in, Luijken indicates. With it you can monitor and map out the behavior of malware. That is, with this you don’t look so much at what something is, but what it does. With FortiEDR you can actually see all the behavior on and from your endpoints. This includes not only the actions of endpoints, but also the applications on the endpoints, the versions, the patches and so on. Based on that insight, Fortinet gives a security score to the various components. You can then base very fine-grained policies on that.
The description above is in a nutshell what EDR does for the endpoints within organizations. Many readers will already be familiar with this, as there are quite a few EDR providers on the market at the moment. Still, it is good to outline the necessity of EDR in daily practice. If you are still using traditional antivirus, you would do well to take a closer look at EDR. EDR is not going to offer 100 percent security either, there’s no such thing in principle, but it’s going to come a lot closer to it than traditional EPP.
Why Fortinet FortiEDR?
As already indicated, there are many EDR providers on the market right now. Within these offerings, what makes Fortinet’s FortiEDR unique? That is the main question we want to answer in this article. When we ask Luijken this question, the first thing he points out is Fortinet’s Security Fabric. Like all the other fabrics in the market that we have come across so far, the Fortinet Security Fabric is also about something conceptual, not an actual product. That is, the Security Fabric is an invisible layer that Fortinet is placing over its own portfolio (and that of third parties).
The purpose of the Security Fabric is to allow the various (security) products within organizations to work together optimally. This immediately makes every point solution much more widely deployable than it would be without this integration. For example, from FortiEDR you can immediately send commands to Fortinet’s FortiGate firewalls. If it detects suspicious behavior of an application, making contact with a server that attackers use, for example, then the FortiGate can immediately close the relevant ports.
The Fortinet Security Fabric is, as far as we know, the most advanced security fabric on the market. Fortinet has been working on it steadily for a decade. That also means it’s very widely supported. Fortinet has components from some 450 fabric partners in the Security Fabric in addition to its 50 or so proprietary components. So it’s no exaggeration to say that with FortiEDR you’re buying more than an EDR. We will publish a comprehensive article about the Fortinet Security Fabric soon. So keep an eye on the site if you want to know more about it.
Pro-active monitoring
With the integration into the Fortinet Security Fabric we have mentioned an interesting feature of FortiEDR, but not really a unique one. Rather, this integration is a unique feature of Fortinet as a whole. A pretty important feature, but it doesn’t have that much to do with the operation of FortiEDR itself at its base. A Fabric partner’s EDR solution (we see SentinelOne listed among the partners, for example) could theoretically have the same impact on an organization. In other words, FortiEDR must also be technically distinctive to be of interest to organizations.
According to Luijken, this is certainly the case. He specifically mentions pro-active monitoring as a component that makes FortiEDR different from other solutions in the market. It’s all about making the attack surface as small as possible. It does this by means of vulnerability assessments and actively searching for devices on the network.
This makes it possible to detect rogue devices proactively. These types of devices are not managed and may also be unprotected and thus pose a risk to the organization as a whole. You can also gain insight into IoT devices with this, as this is also a fairly popular attack route. Besides detecting equipment, proactive monitoring also means that you can continuously keep an eye on the status of applications, patches and so forth. Based on all this monitoring, you can proactively deploy policies, based on a risk analysis. Think of isolating equipment whose level of vulnerabilities is too high or whose reputation score is too low. That should already make the attack surface a lot smaller at the end of the day.
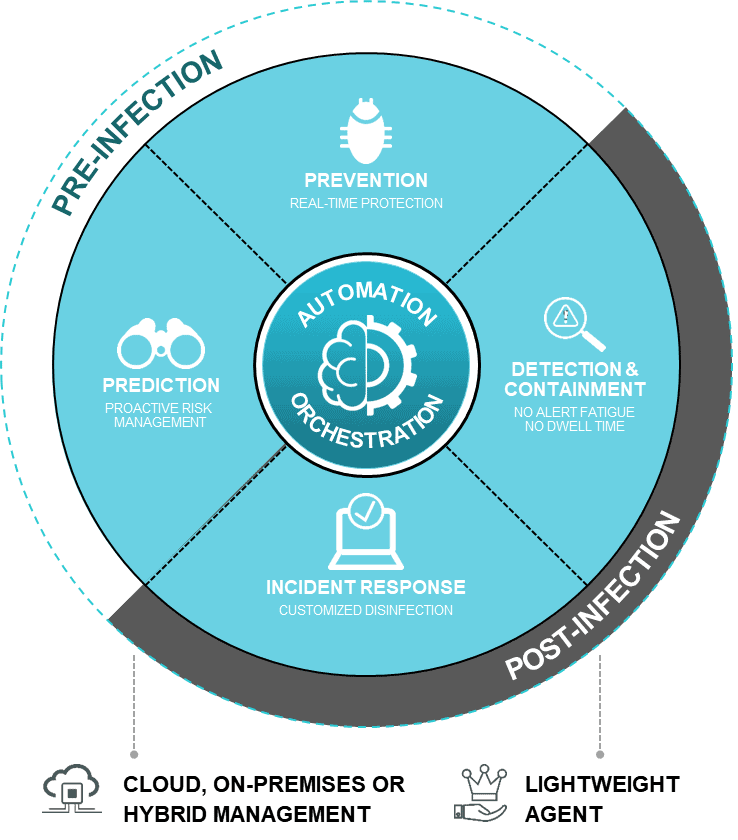
Focus on prevention
Detection has been an important focus for many vendors, because the mantra is that “it’s not a question of if but when you become a victim”. That may be true, but prevention is still better than cure. Fortunately, the last few years we have seen more focus on prevention, especially in the more modern solutions that us ML. FortiEDR is certainly one of them. Thanks to a well-trained ML model that is continuously updated, attacks can be stopped before they can be executed. This is possible because the models can quickly detect the behavior of malware and take action accordingly.
Mind you, the ML model does not do all this without help. It also uses real-time feeds with threat intelligence. These come from a database in the cloud (Fortinet Cloud Services) that Fortinet continuously updates. Also, FortiEDR still works preventively even if the network connection is lost. This is not intended as a specific use case, by the way. For optimal protection with automatic response, you obviously need to continue to have access to Fortinet Cloud Services. But it is still nice to know that in an emergency, as a fallback, it will continue to work.
If you think that all these features and possibilities of the FortiEDR agent are a heavy burden on the systems, Luijken has good news. Because FortiEDR does not use signatures (which a solution has to download regularly), you need very little disk space. Also the load on RAM and the CPU is almost negligible. So in principle you can run the agent on any device you can install something on.
Detection and defusing
So far we’ve talked exclusively about proactive and preventive features of FortiEDR. Within Fortinet, they call this the pre-infection part of the solution. However, stopping everything is impossible. This means that FortiEDR must also be able to stand its ground in the field of detection and response (post-infection). Ultimately, this part is actually the core of what we call EDR. That stands for Endpoint Detection and Response for a reason.
Within the detection part of FortiEDR, what Fortinet itself calls detect and defuse, the emphasis again is on the fact that this happens in real time. As soon as it detects suspicious behavior, in other words a potential breach, FortiEDR shoots into action and disarms the malware. Among other things, it does this by immediately blocking the relevant communication to the outside world from such a process. This removes a large part of the danger from the malware. You take the wind out of the sails of malware. Things like command and control communication, data exfiltration and the activation of ransomware (by downloading a binary) are theoretically impossible, or at least a lot more difficult.
One component of FortiEDR’s detection capabilities that we should not underestimate according to Luijken, is that it uses the same ML models. That is, pre- and post-infection use the same tools and Fortinet Cloud Services in this area. So that also means that the two components can learn from each other. If something initially gets past the prevention phase, but does not get past the detection phase, then the ML model knows the next time already in the prevention phase that it needs to catch this process. In other words, the two sides train each other.
To find out what Fortinet means by real-time detection of malware and making it harmless, Luijken cites what FortiEDR does with ransomware. In the event of such an attack, it is obviously crucial to prevent (part of) a disk from being encrypted. Fortinet can offer that with FortiEDR, according to him. The solution doesn’t need to use a volume shadow copy service for this. That is good news, because volume shadow copy service usually means that is costs extra resources. In addition, you often have to take a system offline. Luijken indicates that FortiEDR can determine whether something is affected by ransomware based on three files, which it caches. If it is, FortiEDR defuses the ransomware in real time. This without having to take anything offline to do so.
Analysis and response
The final step within FortiEDR is how to deal with what it blocked in the previous step. This starts with analysis within Fortinet Cloud Services to give a definitive classification to a specific threat. This is necessary because otherwise it is difficult to determine what the next steps should be. In addition, this analysis is also important to make FortiEDR as a whole more powerful again. After all, ultimately the solution is constantly learning.
Ultimately, the analysis of what FortiEDR detects should naturally result in actions that it should take. In other words, the analysis results in a playbook. A playbook can take many forms, depending on what is needed based on the detection and analysis. A simple example of such a playbook would be set up a link with FortiGate firewalls to ensure that it they respond quickly and decisively. This can be done manually. Ideally, of course, it should be automated as much as possible.
Conclusion: a continuous process
All in all, Fortinet offers a very complete EDR solution with FortiEDR. Partly because of the additional possibilities it offers within FortiEDR, but also certainly because of the integration with the Fortinet Security Fabric. However, the most important thing, according to Luijken, is to see EDR as a continuous process. That starts with visibility, followed by blocking what you know is bad from your organization. Then comes rapid detection and defusing and finally the response. All these parts are connected in many ways, so it is not a purely linear story. This is mainly because of the shared ML models within the different components and the Fortinet Security Services that feed them. Finally, FortiEDR is part of the Fortinet Security Fabric, which allows you to integrate this solution even further into your landscape. This brings it full circle.
