Security researchers from SentinelOne have discovered a new malware cluster dubbed WIP19. The malware variant is likely used by Chinese cybercriminals and primarily targets IT service providers and telecom companies.
According to the security researchers, the malware variant recently surfaced among IT service providers and telecom operators in Asia and the Middle East. This may indicate that the variant focusses on espionage activities instead of disrupting operations.
Compromised digital certificate
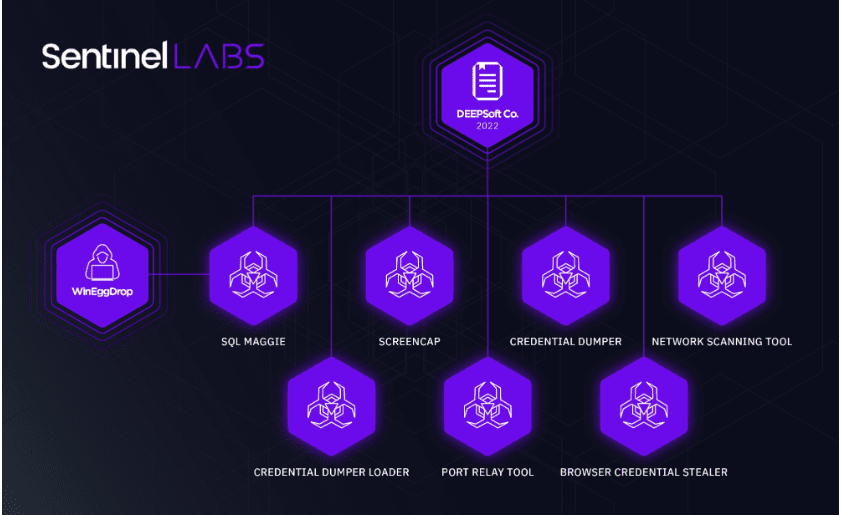
The WIP19 malware uses a compromised digital certificate as a backdoor. The certificate originates from Deepsoft, a South Korea-based firm. A modified version of the certificate is used to give various malware components access to affected networks. Components include a password dumper, a downloader and an uploader, a key logger and a screen recorder.
Possible Chinese actors
The investigation suggests that the attackers are of Chinese origin. The researchers base their claim on the use of WinEggDrop components that originate from a known Chinese threat actor.
SentinelOne also sees links between WIP19 and Operation ShadowForce, another Chinese malware operator. According to the researchers, WIP19’s toolset has overlap with the toolset of Operation ShadowForce. It’s uncertain whether this WIP19 is a new variant of the latter malware or a new threat that uses the same tactics and procedures.
Furthermore, SentinelOne discovered that WIP19 uses SQLMaggie, a malware implant that appears to be actively maintained. In addition, the researchers identified various other malware used by the cybercriminals behind WIP19.
Tip: Maggie malware gained backdoor access to hundreds of Microsoft SQL servers
