
Security

Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.
Timeline

Security company Wiz wants to make code more secure with acquisition of Dazz
Wiz has recently purchased Dazz. With the acquisition, the cloud security specialist primarily wants to furth...

50,000 industrial control systems are vulnerable within Europe
Hackers have it easy

SentinelOne’s AI-SPM shines a light on AI threats lurking in the shadows
SentinelOne is applying Security Posture Management (SPM) to AI. While organizations can quickly adopt GenAI,...
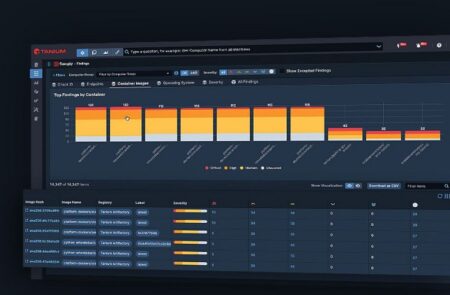
Tanium Cloud Workloads keeps containerized environments secure
Tanium is further extending its endpoint management platform with enhanced visibility and protection capabili...

HP Wolf Security applies deep security layer to enterprise PCs
HP Enterprise Security Edition is now available. In addition to protecting against malicious software, this s...

Five members of cyber gang Scattered Spider indicted in U.S.
The US Department of Justice (DoJ) has named five suspects as responsible for stealing millions of dollars in...

Lenovo launches ThinkShield Firmware Assurance: security at the deepest level
The suite of protections from Lenovo ThinkShield is expanding. Firmware Assurance claims to deliver observabi...

New Windows 11 tool fixes booting issues
Microsoft is working on the Quick Machine Recovery tool that allows administrators to fix non-starting Window...

Previously patched vCenter vulnerabilities actively exploited
Broadcom once again released patches

Admin Portal Microsoft 365 abused for sending sextortion messages
Criminals are sending sextortion emails by abusing Microsoft 365's Admin Portal. Because such messages use a ...