
Security

Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.
Timeline

Microsoft discontinues Autofill extension in Chrome in December
Microsoft is discontinuing the Autofill extension in the Chrome browser as of Dec. 14, 2024. The company says...

Why are simple applications more vulnerable than complex ones?
A surprise find: as it turns out, simpler applications are more likely to contain critical vulnerabilities. H...

Vertex AI vulnerabilities left Google customers exposed
Google's Vertex AI platform had two serious vulnerabilities. These allowed it to access customers' LLMs and r...

Strategy behind Snowflake hackers revealed in court document
Recently, the alleged Snowflake hackers Connor Moucka of Canada and John Bins from Turkey were arrested. Now ...
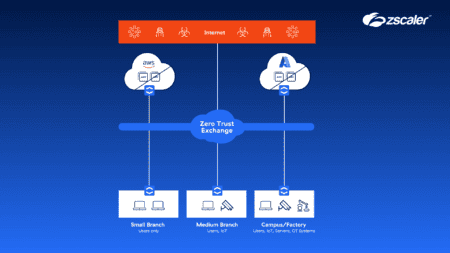
Zscaler brings zero trust segmentation to offices and factories
With its new Zero Trust Segmentation solution, Zscaler aims to help companies securely connect users, devices...

SentinelOne CEO wants to prove that things can (and should) be different in the security industry
What makes SentinelOne different?

Patch Tuesday update for November brings dozens of fixes
Microsoft's Patch Tuesday update for this month includes as many as 91 different fixes for security vulnerabi...

Sysdig unveils Falco Feeds: the latest detections against cloud threats
With Falco Feeds, Sysdig provides customers with the most up-to-date information on cyber threats. Cloud thre...
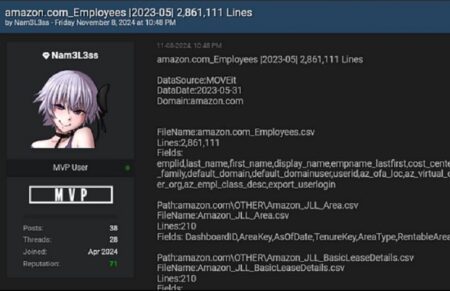
New MOVEit exploit hits Amazon, HP and McDonald’s
Amazon confirms a data breach in which employees' personal data was leaked. This data breach is part of a lar...

Chrome extensions remain a threat even after Google’s Manifest V3
With Manifest V3, Google wants to make Chromium browsers more secure. That's a relative term, because V3-base...