Everything there is to find on tag: cybersecurity.
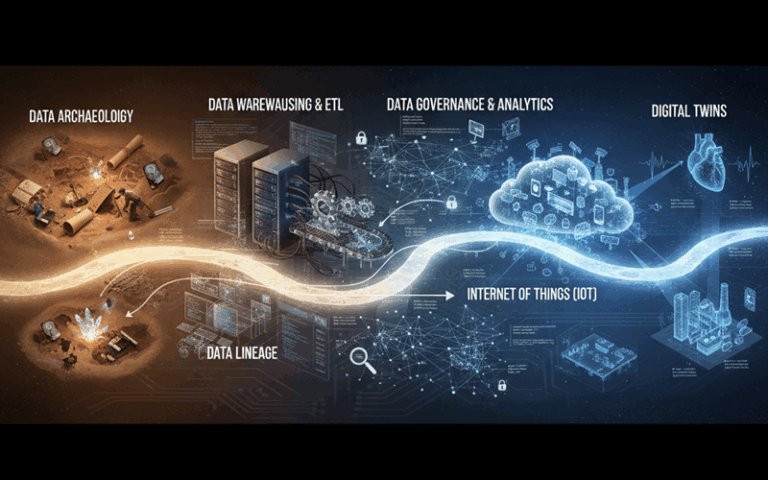
Tracking data lineage from data archaeology to digital twins
Data management must now grow and evolve a new arm that extends to data lineage control. As data streams flow...
Everything there is to find on tag: cybersecurity.

Data management must now grow and evolve a new arm that extends to data lineage control. As data streams flow...

Dutch security researcher Dirk-jan Mollema discovered a critical vulnerability in Microsoft Entra ID that all...

Wiz introduces a new service for organizations affected by security incidents. Wiz Incident Response (IR) com...

Check Point acquires Lakera to build an end-to-end AI security stack. The acquisition aims to help organizati...

API attacks reached a record high in the first half of 2025, with more than 40,000 incidents recorded. Cyberc...

CrowdStrike and Meta are jointly introducing CyberSOCEval, a new suite of open source benchmarks to evaluate ...

DDoS detection tool FastNetMon detected a DDoS attack of 1.5 billion packets per second. The target: a Europe...

Mitsubishi Electric plans to acquire cybersecurity company Nozomi Networks. This follows an earlier investmen...

The acquisition focuses on real-time data pipelines designed to eliminate existing bottlenecks in security op...

Ethical hackers BobDaHacker and BobTheShoplifter discovered serious security vulnerabilities at Restaurant Br...