SASE is without a doubt one of the dominant trends in (enterprise) infrastructure conversations at the moment. You hear it everywhere and everyone seems to be offering it these days. But what is it really and can anyone just call themselves a SASE vendor?
Gartner is a pretty powerful platform. Almost all organizations look at the ranking of potential vendors before they purchase anything. Gartner also regularly ‘invents’ new terms, which it then often presents in their famous hype cycle as well. In 2019, they coined the term SASE, which stands for Secure Access Service Edge. SASE has taken off in recent years. Basically, it is nothing more than a network model that merges multiple, existing components. It is specifically about merging the management of the WAN (SD-WAN) and securing it. The security component deals with things like CASB, ZTNA and FWaaS. The whole experience or solution must be delivered from the cloud. That is, setting it up, implementing it and managing it happens in and from the cloud.
When Gartner comes up with such a new term, you can be sure that it will become important to organizations in the market. This naturally means that more and more suppliers are throwing themselves into SASE. That is what has been happening in the past years, Boaz Avigad of Cato Networks tells us. There are more than 30 suppliers who claim to have it in their offering. These include large and already relatively old vendors like Cisco and VMware, but also smaller and more recent ones like Netskope and Zscaler.
Furthermore, there is also a distinction between vendors that have had a cloud-native approach from the beginning and ones for which an on-prem appliance served as the basis or still does. Palo Alto Networks is an example of an originally on-prem approach.
SASE comes in many shapes and sizes
The above five names indicate that the SASE landscape is quite diverse. On the one hand, you have the infrastructure providers who have gone in the direction of SD-WAN and thus end up with SASE. On the other hand, you have the (cloud-native) security players who originally approached it from the CASB or ZTNA angle, for example.
Cato Networks (founded in 2015) is an exception to the vendors listed above. It was founded as a SASE company, says Avigad. They didn’t happen to ‘stumble onto it’, as is the case with other vendors. That makes them unique in the market. “We are the only true SASE supplier that can deliver everything,” he indicates. Now, that’s an interesting statement. Obviously, we wanted to hear more about this.
Cloud as the foundation
One of the reasons Avigad calls Cato Networks’ offering unique is that it offers SASE as a single cloud-native service. That’s not just a prerequisite for meeting the definitions Gartner has come up with for SASE, by the way. It also ensures that you can route traffic optimally.
If you are still using old VPN solutions or SDP/ZTNA solutions that are not yet delivered from the cloud, then you do not have what a single cloud-native SASE service can offer. In legacy environments, using a SaaS application as a remote worker, for example, would mean that you must first go through the cloud to on-prem and then be routed to the cloud. That is far from efficient and also not desirable in terms of performance.
But even if the cloud does serve as the basis for remote access, this does not mean that everything is well integrated. Avigad cites the example of Zscaler. That vendor has a cloud-based ZTNA service called ZPA, but that exists basically separate from their cloud security solution, ZIA. That makes the overall picture (which we’ll come back to below) less unified than you might expect from SASE.
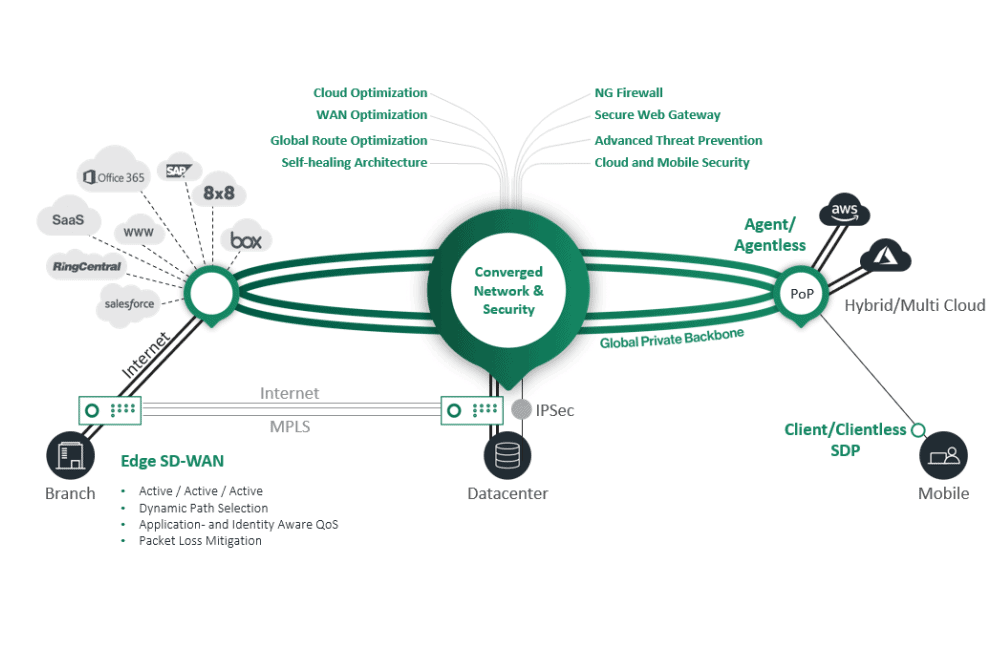
Points-of-Presence
To provide its service, Cato Networks uses so-called PoPs, or Points-of-Presence in the cloud. It currently deploys the service using about 70 of these PoPs. Each quarter, Cato Networks adds about 3 to 4 of these ‘stepping stones’ for the Cato Cloud for customers. By the way, Cato Networks only deploys public PoPs, you can’t have one in a private cloud or on-premises. However, you can put an SD-WAN appliance in your environment that then connects to the nearest PoP in the cloud.
The PoPs themselves are also interconnected. This takes place redundantly via Tier 1 networks. That is, each PoP connects to two Tier 1 networks. This ensures a very fast, stable connection of high quality, even if, for example, you are connecting a branch office in New York to a data center in London.
Private backbone
Cato Networks doesn’t provide its services over the ‘normal’ internet. It uses its own private backbone. This makes it a modern and more affordable alternative to the expensive MPLS. It also generally has a higher availability than MPLS. That often uses a single connection because it is so expensive. Cato Networks has redundant connections, as indicated above.
The gains you can make by running your traffic through Cato Networks’ PoPs and private backbone can be very significant, Avigad points out. Of course, this depends on the type of application. Voip and video conferencing are very sensitive to latency, jitter and other issues. That’s where you notice the biggest benefits. But also a popular service like Salesforce can become very slow if the connection is not good. The public internet is simply not good enough to meet all the conditions and requirements of business applications, concludes Avigad. The fact that the very expensive MPLS exists in the first place also basically confirms this. You don’t deploy that if you can also do it via the public internet.
A holistic approach
The combination of the PoPs and the private backbone makes Cato Networks’ SASE offering a very complete one. First of all, there is of course SD-WAN for things such as WAN optimization, dynamic routing, packet loss mitigation and cloud optimization. The purpose of this is to ensure that your applications, and therefore your employees, always function optimally. For example, cloud optimization makes it possible for the connection to switch between PoPs depending on the application you are using. PoP and application should run as close together as possible for optimal performance. These and other optimizations of long-distance connections depend for a large part on the private backbone, Avigad points out. “Almost all SD-WAN and SASE vendors don’t have this, it really sets Cato apart from the other players,” he states.
In addition to the networking and routing part, SASE obviously also offers the security component. Cato Networks’ PoPs are equipped with this, of course. All PoPs are identical and offer a firewall, Zero Trust Network Access (ZTNA) or Software-Defined Perimeter (SDP), Intrusion Prevention System (IPS), Cloud Access Security Broker (CASB) and Secure Web Gateway (SWG).
More than the sum of its parts
So all in all, Cato Networks has a very complete SASE story. It has SD-WAN, security and a private backbone, all delivered from the cloud. This makes Cato Networks unique in the market, Avigad reiterates. There are vendors like Zscaler who have the security part perfectly in order, but they don’t have a private backbone with worldwide coverage. For that SD-WAN part of the solution, you’ll have to go with a different one.
Even if a supplier does have all the components (think of NTT, for example), this does not mean that they can deliver it as a single solution to customers, Avigad points out. Cato Networks does. This has some obvious advantages. Everything is managed from a single point and alerts come in from there as well. In this way, you can create a single flow. This is ultimately the main benefit of converging the different SASE components. Since Cato Networks delivers the solution from the cloud, you also don’t have to manage any more appliances. This is still often the case with many other vendors who claim to deliver SASE.
Complexity demands convergence
It should be obvious that Cato Networks sees itself as the only vendor in the market that has SASE truly and comprehensively covered. That is, it follows Gartner’s definitions to the letter. In principle, of course, this doesn’t say very much. The fastest route to an endpoint is not always the only good one. So in theory, it could well be that composite solutions from multiple SASE vendors can also deliver a good end result.
At Cato Networks, they disagree with the above statement. Solutions that have not been converged will never have the level of what Cato Networks offers, according to Avigad. “If you don’t offer a converged solution, you simply can’t offer what Cato can offer,” he states. If, like Cato Networks, you offer everything in a single solution, you can optimize things better. That should provide a better experience for end users. You also have much more control over things like the rollout of updates. Partly because of this, you also remove almost all management from the customers.
Better performance coupled with less hassle certainly sounds like an attractive prospect for customers. However, according to Avigad, it is also simply necessary to do it this way. The distributed nature of today’s IT environments and their continuous expansion makes everything too complex to manage properly on your own. Cato Networks, as the self-proclaimed only true SASE player, is responding to this in a convincing way. How it will all play out in practice, is obviously still up for debate. Will we see more vendors embracing the Cato route, or will they continue to offer SASE only in separate parts? Perhaps a SASE MQ should come from Gartner first before those vendors make a final decision about it.