For many companies, a data privacy strategy is a fundamental means of supporting customer relations and avoiding huge fines. If handled properly, it can even be a competitive advantage. How do you implement and maintain the right data privacy strategy? We talked to Tapan Kumar, Pre-Sales Engineer Data Security at CyberRes, a Micro Focus line of business.
Data privacy has become an increasingly important issue within companies in recent years. Whereas a few years ago, it was still seen as something for which money had to be invested, the urgency is now much more significant. If you do not protect your data at every level of your organisation, there is a good chance that you will become one of the now-familiar examples of cybercrime victims.
In addition, legislation for the protection of data has become stricter. In Europe, we have to deal with the GDPR. Multinationals must also comply with local legislation. A user from the Netherlands must be treated differently from someone from the United States. Even between the American states, there are significant differences in legislation. Therefore, large companies are faced with a great deal of chaos when it comes to the bill to be followed.
CyberRes has also noticed the increased interest of organisations in organising data privacy. CyberRes is a business unit of Micro Focus and has invested heavily in expanding its Voltage platform for data privacy in recent years. Privacy must now be addressed as thoroughly as possible – from discovery, to finding insights to protection of sensitive data. Your company will find out what data it has, what the risks are, and how to protect the data.
Know what data you have
According to Kumar, things often go wrong at the first discovery step. He regularly encounters companies which do not know precisely what data they have. However, it is crucial to know what data a company has. In the end, you can only protect when you know what you have.
Kumar sees companies sending out questionnaires to business departments in the first phase of privacy. In these, they ask which type of data the department has and whether the database is used. This inventory gives a rough idea of what is happening in the organisation. “When I talk to customers involved in protection, they are concerned about encrypting all Personally Identifiable Information data. However, when they ask the business if they have any PII data, they always reply that they do not. Then they use a discovery tool and find out that 90 per cent of the data is PII data,” says Kumar.
He sees most employees making a wrong assumption about the data within the company. This is while there are enough tools on the market to analyse a data landscape and discover what is there.
Getting to the bottom of it
To give organisations a better idea of where they stand with their privacy strategy, CyberRes offers the option of getting a sort of risk score. It considers things that not everyone in an organisation thinks of immediately, such as data flows or the extent to which the data is critical. “We don’t just look at it from a strict privacy perspective, but we also look at it from a data security perspective. So what if SharePoint or a specific user is compromised? What is the financial impact if the company is ever faced with a data breach? We include fines, reputation damage and lost sales,” explains Kumar. The result estimates millions, expressed in percentages of how probable the high damage sum is. In this way, companies are forced to face the facts.
CyberRes maps out the risks that a company runs and the corresponding value with the financial risks calculator, with calculations based on data of the Ponemon Institute. The calculation is made based on information that a company provides. This includes data flows within a company, how critical the data is, and whether it is employee or customer data. All the information is fed into an algorithm created by a third party investigating many data breaches in recent years. This ensures that it is not looked at with a CyberRes hat on but that an independent judgement follows.
Starting, refreshing and maintaining a strategy
A hybrid solution is essential if a company embraces a modern data privacy strategy. This is due to the fact that organisations increasingly rely on hybrid environments. As a result, data is also foud across different cloud applications and cloud environments. It makes it useful to know where the data is within these complex environments. CyberRes responds to this with a service based cloud solution that allows a company to start data discovery very quickly.
The discovery tool takes different types of data into account as far as possible. Data from text is apparent, but the tool can also handle media files. It uses optical character recognition for this. There is also the option to scan for ROT data, which stands for redundant, outdated and trivial. This type of data adds possibly little or nothing but is still somewhere on the infrastructure and might contain data that is still sensitive. Ultimately, Voltage has been built to cope with more than 1,000 data formats. This is necessary to be able to deal with how applications and databases write.
Protection offers extra security
In addition to arranging and maintaining the discovery part, a privacy strategy goes hand in hand with arranging the protection part. Protecting data means preventing hacking attempts from succeeding as much as possible. At the same time, there is no guarantee that attacks will be kept at bay altogether. In the unlikely event of a hack occurring, the hackers must not be able to do anything with the information.
To make this possible, there is technology that prevents data from being linked to identity. Encryption and tokenisation are suitable for this. Data is thus encrypted, and the original information is linked to unique tokens. For the employee or relation of an organisation, it is still possible to read data, but for the malicious party, the sensitive data is unusable and cannot be viewed.
In addition, drawing up and complying with policies is essential for privacy. For example, a rule prescribes the use of only secure services for sharing information. But also which person has access to the data, what they may do with it, and the associated risks. If you have drawn up such measures and rules, you can link them to related services and frameworks. Examples include integrating your data privacy products with identity and access management technology NetIQ.
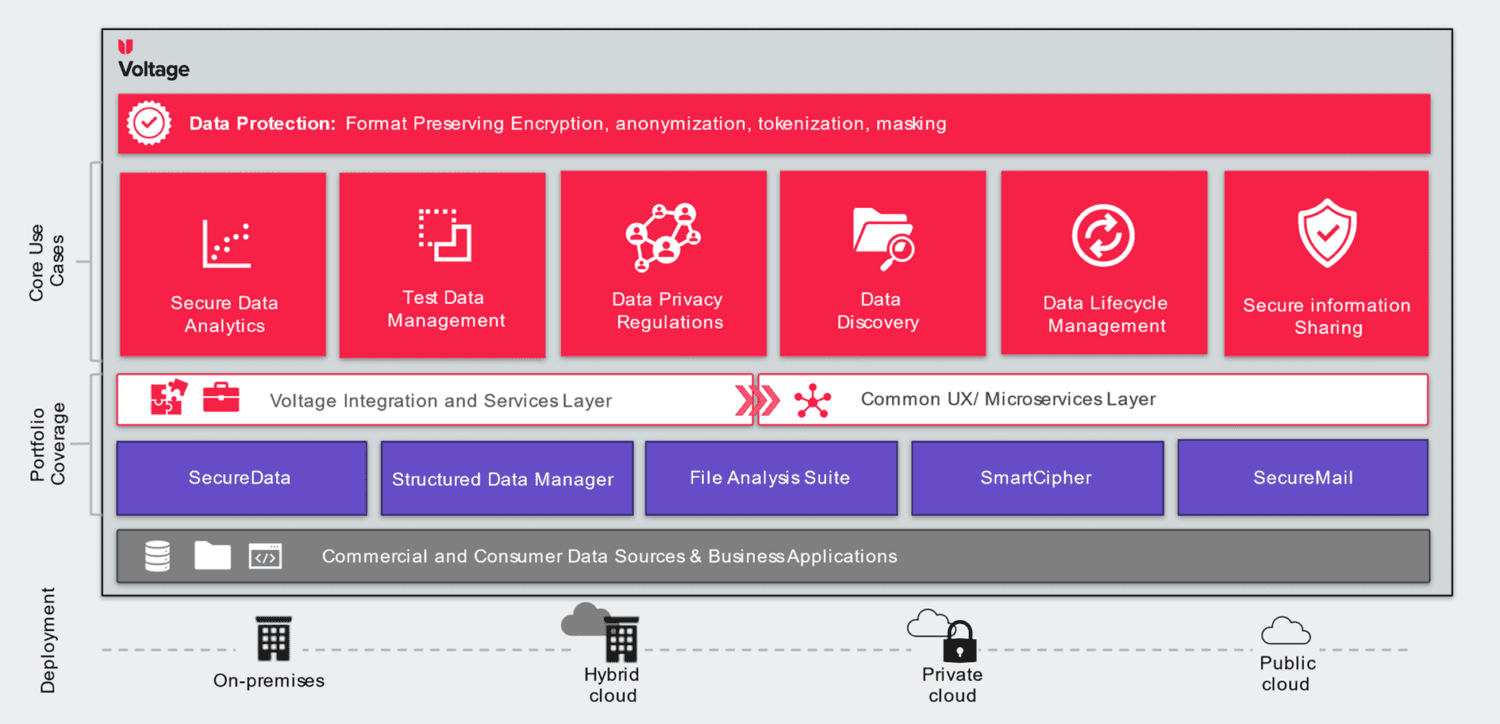
Data privacy thus assumes that a malicious party can get into the corporate network. However, when that happens, the cybercriminal can do very little with the sensitive information because of encryption, tokenisation, and policy enforcement. It makes attacks a lot less attractive. Of course, we also looked at how CyberRes wants to achieve this globally. The image below gives an idea.
Data, identity and access
This picture looks a bit complex for people unfamiliar with the Voltage product. Many things, however, can be linked to discovery, protection, and analytics (for insights on what you have the risks involved, and where to act on), Kumar assures. For the above issues, different products may be necessary, but the aim is to manage as many privacy issues as possible from one platform especially when you consider that many things can ultimately be traced back to data, identity and access.
For example, SecureData, SecureMail and SmartCipher are services within the portfolio that focus heavily on encrypting data. SecureData can, for example, secure PII- or PCI (Payment Card Industry) data. SecureMail, as the name suggests, tackles the securing of information on the mail. SmartCypher encrypts more of the policies linked to files to provide protection everywhere. The Structured Data Manager and File Analyses Suite, in turn, can do more for finding and classifying data, which fits in with the discovery part.
Security gain and competitive advantage
Privacy is a necessary step anyway, given the many rules and regulations and the customer’s demand to be able to hand over data in confidence. Yet not every organisation is aware of what data it possesses. If this is not clear, the correct policies and encryption steps cannot be applied. In the event of a breach, the company may come to a standstill, suffer considerable reputational damage, and expect a hefty fine from the GDPR.
This fact alone should be enough of a stimulus to closely examine your privacy strategy. Yet today, privacy is more than just a security issue. A good strategy also means that employees can work together with confidence, which is essential given the increased use of digital tools. In addition, data is constantly protected, even when it moves between cloud environments. With the desire to move more and more workloads to the cloud, this is a time saver.
We can therefore conclude that a correct data security strategy enables a company to guarantee the privacy of data at any place in the organisation. It doesn’t matter how old the information is. Data security makes it possible for a company to focus on its core activities, such as retail or banking. Concerns about reputation and monetary loss are removed.