NIST will release an updated Cybersecurity Framework in the spring of 2024. It is making a draft available now so companies can provide feedback.
NIST’s Cybersecurity Framework (CSF) does not impose obligations on U.S. or European companies, but it does serve as a tool for many organizations as they plot their cybersecurity strategy. According to figures from the institute, the framework has been downloaded more than two billion times by companies from more than 185 countries.
The framework has been around since 2014 when it was presented as a “living document” so that it could always make adjustments based on new circumstances.
Serving wider audiences
After ten years, the National Institute of Standards and Technology (NIST) believes it is time to update the framework. The main purpose of the update is to expand the audience that can use the framework. Currently, the focus is on organizations occupied with the critical infrastructure of a country. However, since cybersecurity is important to all organizations, the CSF should prove useful to organizations large and small. The CSF will become the new and more inclusive designation, as the previous model was actually called “Framework for Improving Critical Infrastructure Cybersecurity.
Furthermore, it adds a sixth action. The identify, protect, detect, respond and recover actions are supplemented by the ‘governance function’. “Which describes how an organization can make and implement its own internal decisions to support its cybersecurity strategy,” the announcement indicates.
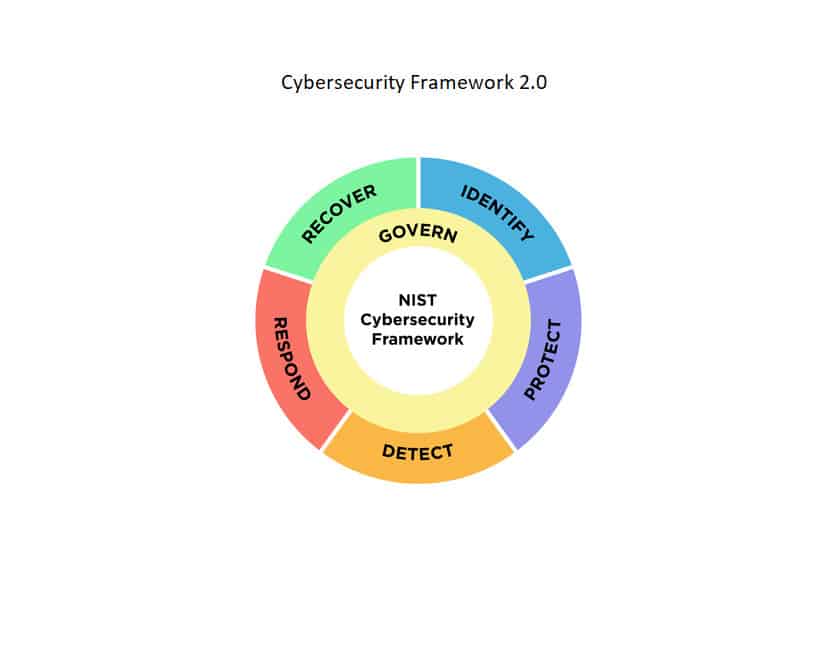
Source: NIST
For and by organizations
The updated framework will be proposed in the spring of 2024. Currently, only a draft is available. The idea behind this is to give companies some time to provide feedback and critiques on this version so that a final framework can be created for the industry and with the industry. “With this update, we are trying to reflect the current use of the Cybersecurity Framework and also anticipate future use,” said Cherilyn Pascoe, the lead developer of the framework at NIST. Feedback will be collected until Nov. 4, 2023.
“Many responses said we should retain and build on the key features of the CSF, including its flexible and voluntary nature,” Pascoe said. “At the same time, many asked for more guidance on implementing the CSF and ensuring that it could address emerging cybersecurity issues, such as supply chain risks and the widespread threat of ransomware. Because these problems affect many organizations, including small businesses, we realized we needed to step up a gear.”
The proposal, therefore, includes use cases to help mainly smaller companies use the framework.
NIS in Europe
The framework, however, is not to be confused with the NIS in Europe. This is a European directive that lays out which cybersecurity measures European companies are required to take. Earlier this year, this directive was updated, and NIS 2 will apply in all EU member states by Oct. 17, 2024, at the latest.
However, the obligations do not apply to small organizations, with fewer than 50 employees and an annual turnover below 10 million euros. However, it will become mandatory for a bigger group of large organizations due to an expansion of sectors in NIS 2.
For smaller organizations, however, cybersecurity measures are still recommended. Mainly because SMEs do not seem to recover as easily from an attack. The European Directive or the NIST’s Cybersecurity Framework can then be a useful guide.
In any case, the NIST can be used, for example, to prioritize cybersecurity activities and address potential risks. A current picture of the state of cybersecurity can be created and a future picture that projects what the organization hopes to achieve. Based on the framework, IT teams can then clarify to other departments and management what measures are still essential for the organization’s protection.
Also read: Ransomware fatal for SMBs: security increasingly taken seriously
