The Chinese hackers who broke into Barracuda’s Email Security Gateway (ESG) devices appeared to be primarily interested in devices belonging to politically important targets. The hackers spared no expense to maintain a presence in these devices after a patch was released. Barracuda eventually decided to get all affected devices replaced.
Mandiant further investigated the zero-day in Barracuda’s ESG devices. Tts published report states hackers deliberately sought out devices belonging to key individuals and provides insight into the global distribution of affected devices.
Espionage
On May 19, 2023, a zero-day was found in Barracuda’s e-mail security products. The vulnerability enabled a command injection attack. This is a type of cyber attack in which hackers direct an infiltrated operating system to execute arbitrary commands. Hackers did not need physical access to the devices to launch an attack. The hackers also did not have physical access to these devices, since Chinese hackers were behind the exploitation of the zero-day. This was done for espionage purposes since October 2022. Researchers made this observation earlier, and detailed the event in their latest report.
The espionage purposes are evident from the campaign’s targets. The main focus appeared to be on governments, with national government agencies being the biggest target and local government agencies appearing to be the third most important target. In between are companies that deal in high-tech and information technology. Overall, about a third of the attacks targeted public institutions. Here, investigators came across shell scripts targeting e-mail domains of public institutions, but the hackers would also seek out targets involved in diplomatic negotiations with foreign countries.
When a patch was released a few days after the vulnerability was found, the hackers appeared to target government and high-tech institutions even more extensively. The hackers did not simply allow themselves to be driven out of the broken-in devices but maintained a presence with high-level victims via previously devised tooling. “These factors support the assessment that the campaign had an espionage motive,” Mandiant wrote in the report.
A summary of the events, can be found here: Barracuda wants customers to replace vulnerable ESG devices
European targets: Belgium, Germany and Poland
Originally an American company, Barracuda Networks has built its customer base primarily in this region. As with many products from U.S. vendors, there is also a solid European customer base. In most European countries, the zero-day has affected government and industry. But mainly ESG devices in companies from Belgium, Germany and Poland were highly targeted for exploitation.
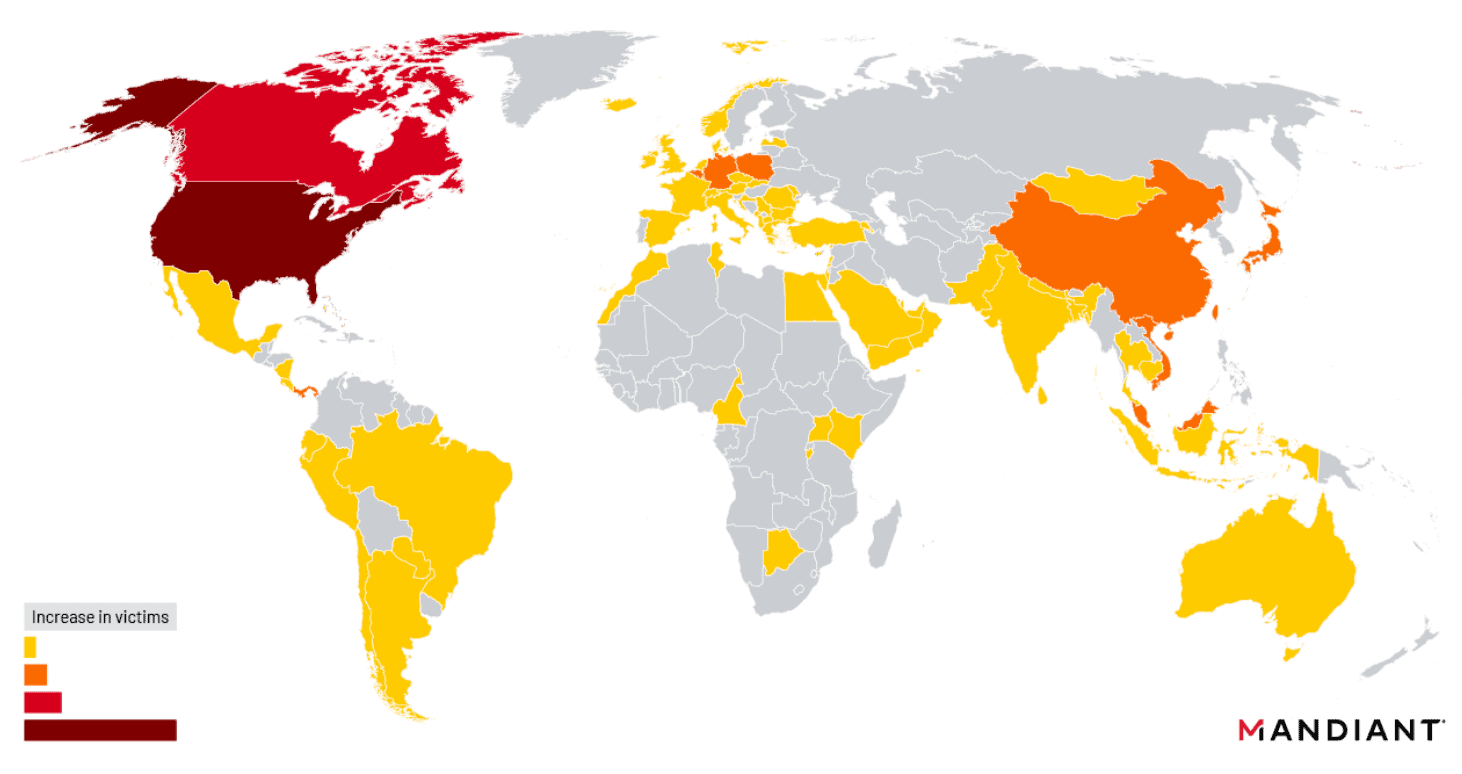
According to Mandiant’s report, hackers obtained access to five percent of all ESG devices in use worldwide. That is a small number, but because of the specific sorting out of government agencies and essential companies for a country’s infrastructure, the consequences cannot be seen lightly. Through the spying, sensitive and important information about ongoing negotiations or new technologies will have ended up in China’s hands. Moreover, the hackers stayed under the radar for quite a long time, making it an interesting technique for espionage. Consequently, the researchers suspect that more similar stories will emerge: “It is likely that we will continue to observe Chinese cyber espionage operations targeting edge infrastructure with zero-day vulnerabilities and the deployment of malware adapted to specific ecosystem ecosystems.”
Further, it is also no longer an option for Barracuda to patch the zero-day after the hackers showed that they could quickly modify the malware to bypass patches. Since June 6, the company has been calling for affected devices to be completely replaced. At issue are versions 5.1.3.001-9.2.0.006.
Now that it is known that the devices will not receive a patch for an open vulnerability, they are attracting the attention of hackers. A new backdoor malware named “Whirlpool” already surfaced.
