The hacker collective LockBit already has thousands of victims to its name. Drawing this much attention causes police departments to get eager to stop the criminal organization. Steps have recently been taken to that end, with a joint operation by Europol, the FBI and the British security services taking over LockBit’s website. Europol added that several arrests have been made for this operation, and a decryption tool for the ransomware is available.
This text was updated at 2:10 PM based on the most recent information from Europol.
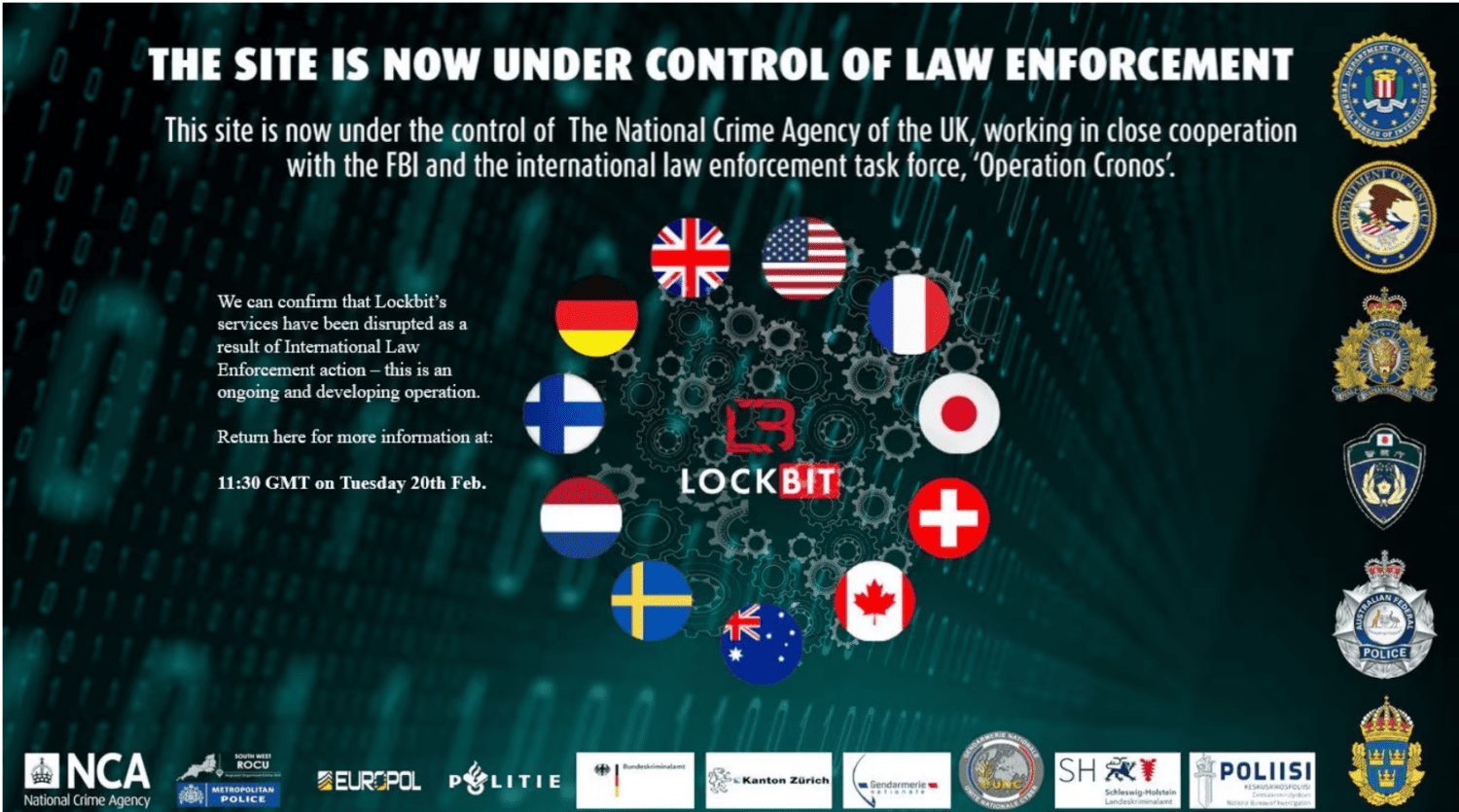
“This site is now under the control of the National Crime Agency of the UK.” This message was posted on the morning of 20 February on the website LockBit, previously used to post the names of their victims with the remaining time they have to pay the requested ransom. If the victim refused to pay, LockBit proceeded to publish the stolen, usually sensitive, data.
Source: Reuters. The article will continue below the image.
For the KNVB, it did not proceed to publication. The Dutch Football Association chose to pay up the requested ransom. This action was supported by experts because there would be sufficient certainty that LockBit would abide by agreements and not publish the stolen 305GB. According to security researchers, the move, in turn, posed a huge risk to other companies within the Netherlands because it signals that the Dutch government is not quick to intervene in such incidents, and there is a willingness to pay.
Also read: Last week in ransomware: Caesars and KNVB pay, MGM struggles on
RaaS market leader
LockBit is active in ransomware practices. Those practices include developing and selling software to encrypt and steal corporate data. In the latter case, the group provides the tools to carry out the attack and a website to publicly extort the victim. That practice is also known as Ransomware-as-a-Service.
The RaaS business is doing tremendously well for LockBit, even making the group the market leader among RaaS providers. That was the finding of research by Arctic Wolf. They counted the used ransomware on leak sites and counted LockBit’s ransomware four times more often than the software from biggest competitor Alphv/BlackCat. The software encrypts data at a tremendously fast rate and can spread further throughout a corporate network completely automatically. That explains LockBit’s popularity.
The group has several members and is said to have a link to Russia. It is not clear how strong that link is, but at least Russian and Moscow-affiliated companies do not get attacked. The largest number of victims would come from the US. There, the number of victims already reached 1,700 companies and organizations by May 2023. Furthermore, the software was discovered in 2020 at Russian-speaking cybercrime forums. In the meantime, the activities are said to have moved to the Netherlands. At least that was evident from posts on websites on the dark web, which have since become inactive.
Arrests and takeover of infrastructure
Being a market leader in RaaS automatically puts you in the crosshairs of police forces. A joint operation by Europol, the security services of the UK and the US and several national police forces, including that of the Netherlands, has now managed to take the leak website offline. Since the website served to leak victims’ names, the operation ensures that LockBit’s access to the outside world is blocked.
According to vx-underground, a website on which cybersecurity research is published, not all of LockBit’s servers have been taken offline. On Tox, a secure messaging app, the hacker collective would specifically claim that servers running on PHP programming language were involved in the international action, but other servers ”have not been affected.”
That euphoria may have come too soon. On the afternoon of February 20, Europol clarified the full extent of ‘Operation Cronos’. A spokesman for the U.S. Department of Justice told Reuters in the morning that the operation is still “ongoing and developing.” That message received proof the same day.
During Operation Cronos, 34 servers were taken down, spread across mainly European countries, including the Netherlands, Germany, Finland, France, Switzerland and the UK. 13 of the 34 servers tackled were located in the Netherlands, according to a message from the East Brabant and Zeeland-West Brabant police. Many servers were taken down in the Netherlands, which can be explained by the fact that LockBit previously indicated that it had moved its activities to the Netherlands to operate from there.
Two members of the group were further arrested. The arrests took place in Poland and Ukraine. “Three international arrest warrants and five indictments have also been issued by the French and US judicial authorities,” meaning the operation could continue.
The criminal organization’s infrastructure appears to have been further affected by the freezing of more than 200 crypto accounts that had a link to LockBit. All of the ransomware gang’s infrastructure is therefore under the control of the UK’s National Crime Agency, Europol said.
Source: Europol. The article will continue below the image.

Decryption tool
The technical expertise of the various services was used during the international operation. Together, they have created a decryption tool that is available on the ‘No More Ransom’ portal.
Companies can use this tool to try to recover encrypted data. It has no control over the stolen data, and, in other words, the hackers can still make stolen, sensitive data public.
End of LockBit?
Given the pending arrest warrants, LockBit has not yet been completely broken up. Europol has not ruled out future operations to further limit the hacking collective: “At present, a vast amount of data gathered throughout the investigation is now in the possession of law enforcement. This data will be used to support ongoing international operational activities focused on targeting the leaders of this group, as well as developers, affiliates, infrastructure and criminal assets linked to these criminal activities.”
This means police departments also know that this successful operation did not yet bring LockBit to an end. In any case, the battle between the ransomware group and the police departments has begun; who will ultimately prevail remains to be seen. At least in the meantime, companies and organizations are not yet rid of this ransomware gang.
European companies are also taking the threat more seriously. Research by ZeroFox cited only a few months ago that Europe is still an attractive target for LockBit 3.0. Thirty percent of attacks by this ransomware in early 2023 affected European businesses and organizations. There was a small drop toward the end of the year, but this was only one to two percent. That’s because the number of politically inspired attacks is said to have decreased, but LockBit’s financial motives always had the upper hand and continue to do so.
Also read: LockBit 3.0, the market leader in ransomware
