When you say Wiz, you’re actually saying Security Graph. The graph database on which the entire company is built has undoubtedly been the most distinctive part of the company from the outset. During a visit to the first edition of Wizdom London, the EMEA version of the company’s own conference, we heard how fundamental the graph is to the company and what we can expect from Wiz in the future. One thing is clear, it has a lot of ambition and plans.
Wiz is a rather special player in the security field. On the one hand, it is very young (founded in 2020). On the other, it is also already hugely successful. Wiz has risen like a comet in recent years. It raised nearly $1.8 billion in multiple investment rounds. Wiz caught the eye of Alphabet, the parent company of Google. Alphabet bid $23 billion in the Summer of 2024, but Wiz did not want to sell. In early 2025, it had another go at it and bid $32 billion. That was enough to acquire Wiz. If the proposed acquisition is approved, Wiz will become part of Google Cloud sometime in 2026.
The reason for this success? In part, it will have had to do with timing. The founding of Wiz more or less coincided with the start of the coronavirus pandemic. Many companies then had to move to the cloud, and Wiz’s CSPM (Cloud Security Posture Management) offering could help them do so in the most secure way possible.
Timing is certainly important, but it does not explain everything. Performance also plays an important role. In that regard, we have been hearing many positive things about Wiz for years. The consensus so far: Wiz is not cheap, but it is very good. The main reason for this, and thus the real reason for Wiz’s success, is the Security Graph.
Graph database is the foundation
A graph database is a special type of database. Data in such a database is not organized in tables, columns, and rows, as is the case with a relational database. A graph database models data in such a way that the relationship between the individual data points is clear. You could think of it as a kind of topology, as you may be familiar with from network environments. The big advantage of this is that security teams and organizations as a whole can gain much more insight from such a database. For example, you no longer need to perform complicated joins. In principle, everything is clear just by looking at the data in the database.
This is basically what Wiz’s Security Graph enables for multiple security profiles within organizations. With Wiz Lens, announced earlier this year, it is possible to see only the information that you are allowed to see in the context of your role.
Wiz is “maniacal” about the Security Graph
Wiz builds everything it does on this graph database. It is very fundamental in this regard. “Maniacal” even, in the words of Jiong Liu, VP of Product Marketing at Wiz, whom we spoke to during Wizdom. Wiz takes this to rather extreme levels. “We throw away the entire codebase of companies we acquire as soon as we buy them,” she says. “Everything has to be on the graph,” according to her.
So far, Wiz has done this with Raftt, Dazz, and Gem Security. The first two were fairly small acquisitions, where completely rebuilding the codebase was perhaps not such a huge operation. Gem Security, however, was already quite advanced in terms of codebase, we hear from Arie Zilberstein. He should know, because he was one of the founders of Gem Security and became part of Wiz through the acquisition.
According to Zilberstein, this approach is important for Wiz. He talks about parts of the Wiz platform “expanding into each other.” He believes that this can only really happen if the codebase of the various components is identical: “Wiz is a platform; we don’t just tie different products together.”
Wiz is about much more than CSPM
As mentioned, it started with CSPM, which provided security context in the cloud. The company then also applied it to developing applications in the cloud with Wiz Code. This provides insights into where code comes from and where any vulnerabilities may lie. Following the shift left of Wiz Code, there is now also a shift right.
With the new Attack Surface Management (ASM), the Wiz platform can help security teams detect routes that attackers can choose. It focuses primarily on routes that attackers can actually us, not just hypothetical attack routes. These are the most critical and deserve the most attention. This is reminiscent of the story of Pingsafe, which was acquired by SentinelOne in early 2024. It is important to note that ASM not only works in combination with cloud environments, but also works on-premises.
Wiz Defend: a security cornerstone
The Wiz platform now also offers observability and security in runtime, i.e., with telemetry handled in real time. With this, Wiz is taking steps that are important for the SecOps department of organizations.
Wiz Defend is an important, relatively new product in this regard, according to Arie Zilberstein. He is one of the founders of Gem Security. Wiz converted this into Wiz Defend. This is a Cloud Detection and Response (CDR) addition to the Wiz platform. Interestingly, it is an agentless solution and is therefore a nice addition to the agent-based part of Wiz’s portfolio.
According to Zilberstein, Defend is “more than a product, it’s a new approach to connecting teams.” Traditional SecOps tools such as EDR and SIEM simply cannot cope with modern cloud environments, he says. Defend, built on the Wiz graph, puts only the context that matters onto the graph. The idea is that this allows Defend to offer added value for multiple teams.
He calls Defend “SIEM’s best friend,” precisely because it can filter out all the noise from the signal and only pass on the most important threats. According to him, Defend has become the “cornerstone” of the security strategy for customers who already use it.
Expansion from graph to SaaS
The cloud is, of course, more than just IaaS and PaaS. It also runs a lot of applications. These must also be properly secured. Wiz already had integrations with Okta, OpenAI, Github, and Snowflake, among others, but now it is adding an appealing solution: Microsoft 365. The integration with Microsoft 365 now allows organizations to uncover issues such as misconfigurations and overly broad access privileges. In addition, it can identify sensitive data in OneDrive and SharePoint and flag risky links and permissions as such. Of course, everything runs on top of the Wiz Security Graph to provide context.

Building such an integration is no easy feat, we hear from Liu. She says that the integration with Microsoft 365 is fundamentally different from the others mentioned above. Those were mainly about scanning code. So those integrations are aimed at developers. The integration with Microsoft 365 is much more in the SecOps domain. In order to build these types of integrations and add value through the Security Graph, Wiz needs to gain a “deep understanding of the workloads,” says Liu. Identity, in particular, adds a lot of complexity. “When building the connectors for Github and Snowflake, we spent about 50 percent of our time on identity,” she says.
AI for security and security for AI
A final component of the Wiz platform that we would like to highlight here has to do with AI. This involves the use of AI to better secure organizations, but also to secure AI itself. For the latter, Wiz has released AI Security Posture Management (AI-SPM). This allows organizations to now also secure things like AI agents and MCP servers, on top of protecting and securing the deployment of the models they use. Detecting Shadow AI is also an important component of AI-SPM.
In addition, Wiz has recently released several of its own agents: the SecOps Agent and the Issues Agent. One of the founders of Wiz mentioned the SecOps Agent on stage during Wizdom, but the Issues Agent seemed to have changed its name to the Remediation Agent. The SecOps Agent should enable security teams to investigate threats more quickly and respond to them. The Issues/Remediation Agent focuses more on proactively resolving issues within organizations.
Can the graph hold back Wiz in the future?
It is clear that Wiz is using the graph’s capabilities for more and more things. This raises the question of where the limits of the graph lie. After all, Wiz has not made things easy for itself by being so maniacal about the graph. Could the graph become so large that it eventually loses its power? And has Wiz taken on too much work, especially towards future expansions, by focusing so obsessively on the graph? And won’t it all become prohibitively expensive for customers if the graph covers an increasingly large area?
We ask Liu and Zilberstein the above questions. When asked whether the graph might become too large at some point, she indicates that Wiz has optimized it to the extreme. At the moment, there is no reason to believe that they will reach their limits anytime soon. And they already have 100 billion so-called relationships in Amazon Neptune, the graph database that Wiz uses. This also makes Wiz one of Amazon/AWS’s largest customers for the database, but that’s beside the point.
When we ask whether always reducing everything back to the basics, i.e., the graph, could hinder Wiz’s growth, we don’t really get a clear answer. “If we were to find ourselves in the hypothetical situation of acquiring a SaaS security company, everything would have to be on the graph,” Liu replies, in line with the stance Wiz has taken so far.
In the event of larger acquisitions than Gem Security, should they occur, this would obviously mean a lot of extra work. After the acquisition, Gem Security was taken offline for three months, during which Gem Security’s customers were migrated to Wiz. Wiz did this so that the product could be completely rebuilt from the graph. If Wiz ever acquires a much larger company, something that is not at all inconceivable with Google’s financial support, the question is how long that product will be offline. Although by that time, Wiz will undoubtedly have more developers who can work on it, so perhaps it will not be as bad as it seems. However, we do not see Wiz consistently making a few acquisitions per month anytime soon.
Towards a horizontal security model
Finally, there is the question of cost. Graph databases are very powerful, but also very expensive. The high price that Wiz has to pay Amazon will ultimately be passed on to customers. According to Zilberstein, Wiz is well aware of this. The idea is that Wiz will also replace other security tools. That will reduce costs.
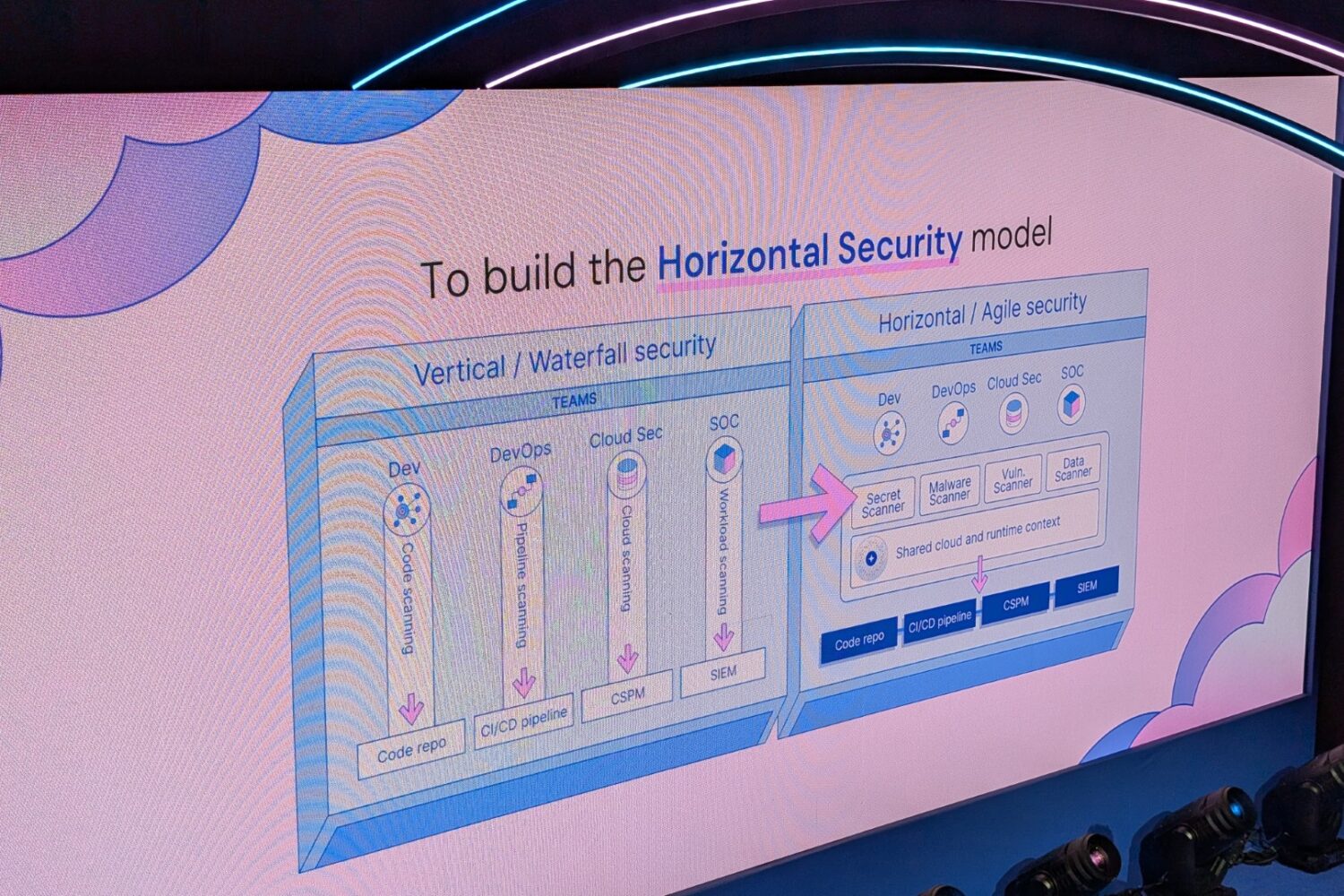
We wonder whether this will actually work in practice. In our experience, the security bill for organizations has not really gone down yet. On the other hand, the focus on the underlying graph could well lead to more consolidation. This would make it possible to build the horizontal model or platform that Wiz is talking about.
Where many other security models are vertically oriented, with a silo per security segment, which then may or may not be integrated with each other in a collection of smaller platforms, the horizontal architecture of the Wiz model is fundamentally different. This inevitably means a more prescriptive and opinionated approach and less openness. There are partnerships with more than 200 other (security) vendors. However, simply ingesting everything from everywhere into a platform does not seem to be Wiz’s approach. This results in a slightly more closed platform than you see with the vertical approach. However, crucially, the resulting horizontal platform should perform better.
We conclude with one of the last things Jiong Liu told us, starting with a quote she attributes to Jen Easterly, former head of CISA: “We don’t have a security problem, but a code quality problem.” That can mean a lot of things, but Liu highlights the impact of the quote on what Wiz wants to achieve: “We are also looking at applying the graph outside of security. It is so powerful that it can also help platform engineers, among others.” There is no doubt that there is a lot more to come from Wiz. One thing is certain: the graph will continue to play the leading role.
