Everything there is to find on tag: Cloud Security.

Everything there is to find on tag: Cloud Security.


Today, AWS is launching a revamped Security Hub, with SentinelOne as a launch partner. The new collaboration ...

1Password has signed a strategic collaboration agreement (SCA) with AWS to simplify access for cloud customer...

Zscaler is introducing a series of new solutions to bring Zero Trust to more locations. The new features focu...

A large number of IT companies presented their quarterly figures this week. Below is a selection of the surpr...

Sysdig has donated Stratoshark, an open source tool for cloud forensics, to the Wireshark Foundation. The don...

Cato Networks introduces Cato Autonomous Policies, a new AI feature within the Cato SASE Cloud Platform. It o...

From now on, Wiz will also run natively on AWS. With this "Deployed on AWS" status, integration with the worl...

Upwind's first acquisition is now complete. Nyx, which specializes in real-time threat detection within appli...
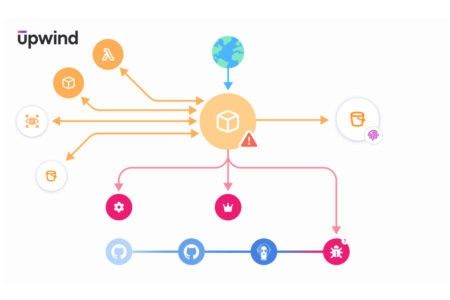
Upwind adds real-time API security to the Cloud Application Detection and Response (CADR) framework. This sho...