Companies are seeing their IT systems grow ever larger. This is mainly due to the use of more and more environments, which we call multicloud for the sake of convenience. They want to simplify tasks at all levels with all these different environments. However, reality teaches us that this simplification also poses complex challenges. After all, how do you ensure that, for example, all security is in order? We decided to discuss this with Stefaan Hinderyckx, who is responsible for cybersecurity within Dimension Data Europe. He calls multicloud a major problem for companies because of its complex security. This is mainly due to the fact that many steps have to be taken, there is actually a kind of spider’s web. In this article, we explain step by step how he came to his findings.
In general, cloud providers already face a considerable challenge when it comes to explaining how security works. Several companies assume that security is arranged by cloud providers. After all, nothing should go wrong with AWS, Azure and Google Cloud, since errors that can be attributed to the providers will spread like wildfire. As a result, the hyperscalers will run out of steam.
In reality, the security of the cloud is a shared responsibility. In the contract with the cloud provider, this so-called shared responsibility model is signed, which can be found in the general terms and conditions. In concrete terms, the cloud providers take care of a number of security matters, while the user also has to secure a number of things himself.
If we look purely at how the security of digital environments is traditionally carried out, it is only logical that the cloud providers apply the shared responsibility model. Traditionally, users have had to take care of everything themselves. Take Windows, for example, where Microsoft has built-in security options as standard. If you really want to secure your endpoint, then you also need extras such as antivirus packages.
Six parts
Even for a truly secure multicold, several extras are needed. Ideally, according to Hinderyckx, the user takes into account six things: a security gateway, a cloud access security broker (CASB), microservices security, encryption and key management, cloud DNS and multicloud visibility. A mix of known and less known security components, with which, according to Hinderyckx, you can achieve a security level of 90 percent. Of course, there is no such thing as 100 percent security; malicious parties are constantly looking for new ways to get in anyway.
Much more important to Hinderyckx’s statement are the real challenges he sees: visibility, data protection, compliance and behavior, detecting and preventing existing and new threats, and the attack surface. Prior to our conversation, he shared the following slide, which shows which solutions address the challenges.
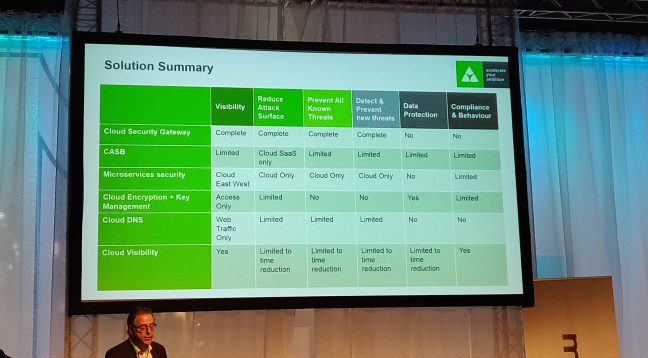
Basic security of the cloud is quite good
One element that is not featured in the image prominently, but can help address the challenges, is the basic security of the cloud. After all, there are already quite a few security features as standard, which makes the cloud fundamentally safer than traditional environments. From Amazon-CTO Werner Vogels, for example, we have already learned that they secure much more at an operational level than most companies. The tools that the cloud provider has at its disposal are unfeasible for many companies. And Azure and Google Cloud also have all kinds of useful protection components at their disposal.
If we take a more specific look at basic security, it’s best to give an example. AWS offers the Amazon Inspector, a service for the automatic execution of security assessments. In this way, the user ensures that the security policies set up within the business environment continue to be complied with. This is an improvement on the traditional way of working, where manual control applies. Normally, a security team formulates a number of requirements and may not check for one hundred days whether the conditions are actually met.
Keeping this kind of standard security feature in mind, we can actually see that most of the dreaded cloud breakdowns can already be prevented with the standard security options. The majority of cloud leaks are caused by incorrect configuration. Hinderyckx also recognizes this problem; the security of the cloud is sometimes open by default. What’s more: multicloud means that the configuration of each platform is different. The manager of Dimension Data sees a correct configuration of all of these environments as a way of tackling the challenge of ‘the attack surface’.
However, Hinderyckx believes that native cloud security also leaves a lot to be desired in terms of visibility. To use his words, details and context about data are lacking, which means that the user can’t actually monitor and protect his data. This insight can be obtained with multiple solutions from the image, as you can see.
Adapting solutions
We used the fact that visibility can be obtained with multiple solutions during our conversation as a parenthesis to talk a bit more about the products. Hinderyckx sees that certain solutions adapt themselves to multicloud. This applies to security gateways and CASBs, two solutions that are converging, according to Hinderyckx. We wanted to hear from him about how he sees these combined solutions.
First of all, there are the security gateways, or rather the next-gen firewalls, where the multi-client character can be seen in the management interface. Often, the firewalls can be deployed within the large three cloud platforms, but because of the management interface, you can set up a rule to allow them to work directly in multiple environments. Because of this automated form of policy enforcement, not everything needs to be arranged manually for different environments.
However, Hinderyckx states that security gateways increasingly resemble CASBs, or vice versa. With CASBs, users adjust which traffic from SaaS applications is allowed, which resembles certain functionalities of gateways. After all, both can be used to comply with rules.
If we take a closer look at the two products, however, we see that both are expanding their functionalities. For example, McAfee recently told us that it wants to expand its CASB capabilities considerably by providing a fully cloud-based platform that also covers other usage applications. In other words, McAfee strives for a solution that achieves Data Loss Prevention (DLP) for every environment, which is typical for multicloud.
Further challenges
It is clear that security vendors also adapt to the security of multiple environments. This will only help to tackle the challenges mentioned by Dimension Data’s security expert. In addition to the challenges discussed earlier, the attack surface and visibility, he sees the following challenges:
- Preventing existing threats – Within companies, employees are constantly sending content to the cloud and connecting their devices to it. The process must be carried out securely. Antivirus can already block most malware.
- Detect and prevent new threats – Malicious people are developing new attacks that bypass traditional antivirus. Hinderyckx, therefore, recommends sandboxing, in which additional tests provide information about the intention of a foreign file.
- Data Protection – Hinderyckx recommends encrypting all confidential data, as multiple copies are often stored in the cloud, increasing the risk of loss. Ideally, you should also think about key management. Hinderyckx questions the key management that cloud providers promise, by pointing to the US Patriot Act (the government can collect a lot of information that way), among other things.
- Compliance and behavior – In addition to GDPR being an important guideline, user behavior and shadow IT also need to be under control. There are various applicable measures for the GDPR, and user behaviour could be mapped with AI and machine learning. Behavioural changes can in this way be detected, for example.
In the end, we find that the six challenges, as coined by Hinderyckx, are a nice reflection of what several multicloud users encounter. It is no secret that the relatively secure cloud platforms leave some things to the users themselves. Of course, they don’t shout that from the rooftops. A spider web of security arises, which provides a complex answer to a complex story.
