There was a time when an enormous data breach would concern people. People were afraid when someone stole their credentials. That feeling seems to have disappeared. Data breaches are as ordinary as DDOS attacks. People don’t seem to care anymore. It also means that it has become harder for cybercriminals to make money on stolen personal data. Their favorite target has shifted from consumers to businesses because they lack cyber resilience and can pay a lot more money.
The cybersecurity industry is booming. Every year we see an increase in security companies. They all try to specialize in different fields. As an enterprise organization, you can choose from hundreds of vendors that offer different types of security. Large corporations easily run 60 different security solutions.
Having many different security solutions doesn’t automatically mean you are better protected. Today a huge part of security is moving towards more automation. We talked to Ramsés Gallego, the International CTO of CyberRes, which is part of Micro Focus. We asked him what his views are on the cybersecurity industry, especially compared to the nature of today’s attacks.
Gallego tells us there are a few easy predictions to be made. One is that the biggest data breach until now will happen in 2022. Every year the amount of data people and companies gather increases. Many companies have terabytes or even petabytes of data stored in many different silos, making the attack surface even bigger. It’s probably fair to say that the record of the biggest breach is bound to be broken every year.
“The biggest data breach will happen in 2022”
Another trend is that more and more attacks are entirely automated. The security industry has adopted machine learning and artificial intelligence (AI) in recent years to improve its security measures. On the other hand, machine learning and AI have become more democratized. That means these technologies have become available for everyone, including cybercriminals. It’s no surprise, then, that there are examples of malware that use these technologies to decide which vulnerability is the most successful in exploiting a machine or device. So, it will be a machine-versus-machine battle that can exploit hundreds of vulnerabilities, instead of cybercriminals manually trying to hack a system with a couple of different vulnerabilities.
Gallego has seen examples where two algorithms were fighting each other. One algorithm was scanning the system to find a vulnerability it could use to exploit the system, while another algorithm was closing ports, adding security measures, raising flags and notifying administrators to keep the system secure. Gallego says he loves that from a technology perspective but hates it from a business perspective.
We can conclude that we are entering the age of automated cyber warfare. Autonomous malware bots will find ways to spread themselves across the internet and use machine learning and AI to hack and exploit systems in many different ways.
We are entering the age of automated cyber warfare
WannaCry needed 7 minutes to spread from one machine to another. The question remains if the next WannaCry will need more or less time to spread. Gallego thinks it will need more time because the industry has created many advanced security solutions after WannaCry. There has been a lot of innovation. The fact is that we don’t know how much time it will take. We know that the only way to slow it down is with good cyber resilience. Companies need to be well secured. Without cybersecurity solutions, the next WannaCry can probably spread even faster. So we need companies to take cybersecurity more seriously.
Reputation damage and customer loss after data leak is very limited
When a company gets hacked the consequences can be enormous. A hacker can take a company down completely. The secondary damage like reputation damage and the loss of customers seems to be getting smaller. It doesn’t hurt or impact the company as much as it used to do. Usually, the stock price drops for a couple of weeks to months, depending on the severity of the breach. But that’s about it.
Gallego says that we need to hold companies accountable for data breaches to ensure their cyber resilience is up to par. There are laws related to data breaches, but companies usually get away with it. Governments take forever to investigate data breaches and rarely hand out fines. When they do sanction companies using fines, they are relatively small.
What is equally important in the attitude towards breaches by companies, is that customers and suppliers of the company don’t hold it responsible either. That’s not right. If one of your suppliers is attacked and has a massive data breach, hold them accountable and ask what they did to secure their systems and question their cyber resilience. Make sure they invest in IT resiliency to be better protected against cyberattacks in the future.
We need to hold companies accountable for data breaches to make sure their cyber resilience is up to par
Future of SOC is changing to automation and threat intelligence
Most IT professionals see a SOC as a room full of people staring at many monitors to analyze incoming data to find new vulnerabilities and active malware. That part of the SOC won’t be around for much longer. The speed at which malware develops, changes, and operates makes it increasingly more difficult to analyze and detect malware by hand. The SOC needs to be automated for the most part. Gallego thinks that 80 percent of the SOC will be automated. Most of the detection and prevention will be automated. It’s much faster to analyze with machine learning and do super correlation. However, a SOC without any humans at all is not possible. You still need people to take action on a higher level.
The SOC can be the single source of truth where all threat intelligence comes together. That is important because most companies use dozens of security solutions, and monitoring those by hand is impossible. The SOC needs to bring the output of all these security solutions together into a data lake. AI and machine learning can use the data lake to correlate, detect anomalies and act as the first line of defense.
CyberRes is working on this new type of SOC with ArcSight. They already process billions of events per day and have data lakes with millions of threats. They also have Galaxy, a threat research program, where data is shared of active threats. You can see which threats are most active or which threats are detected in your region or industry. It also gives CISOs the ability to share their experience with other CISOs, so people can learn from each other. They can share action plans, for example, or how they handled specific threats. That’s valuable information to have when your company falls victim to a data breach or is faced with a particular threat. The Galaxy Threath Research program is available for free for every company.
Start with your cyber resilience today
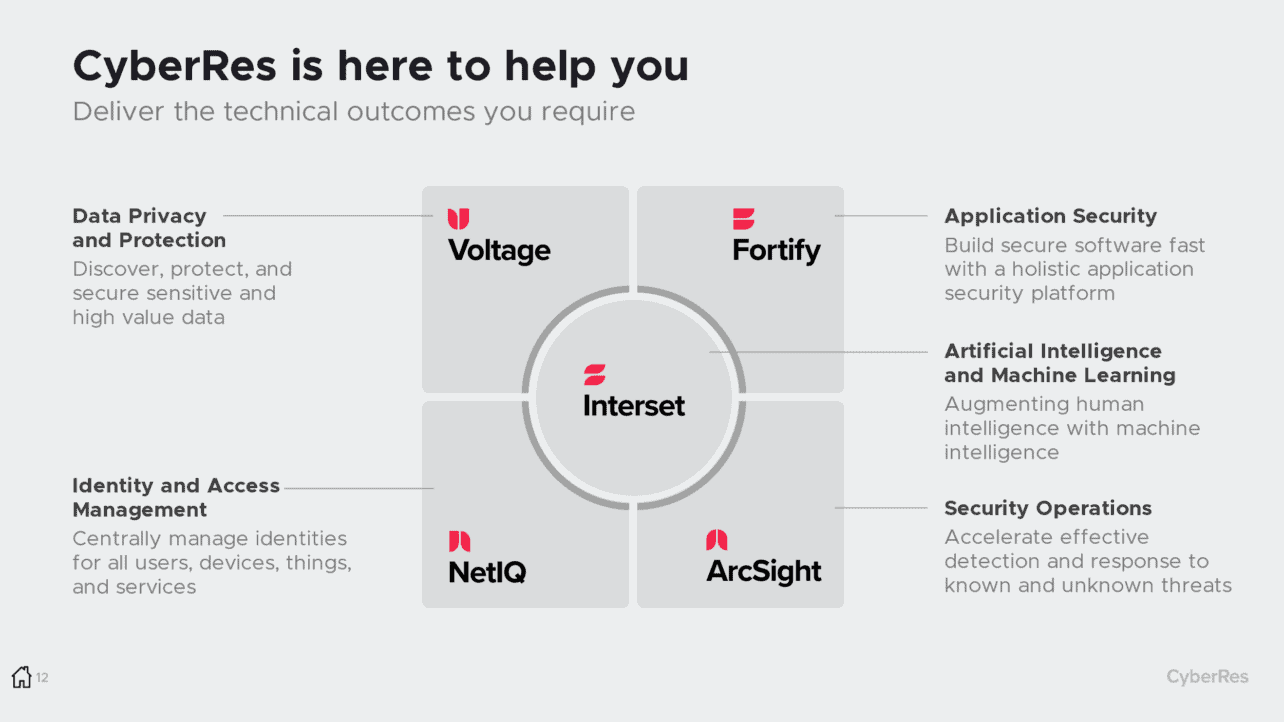
If you haven’t thought about the cyber resilience of your company, it’s never too late to start. At CyberRes, they work with different pillars to offer their cybersecurity solutions. It’s also an excellent way to look at your security and make sure your organisation has cyber resilience in every pillar.
Their first pillar is Data Privacy and Protection. Does your business know where all the company data is located or at least the most critical data? Are there security measures in place to protect high-value data?
The second pillar is Identity and Access Management. How does your company manage access for users, machines, things and services? Is this centrally managed? How fast can you deny access? Is there monitoring in place?
The third pillar is Application Security. If your company is developing software, you need to make sure that development is done securely. That they adopt the proper security principles, that code is checked for vulnerabilities, and much more.
The fourth and last pillar is about Security Operations, ensuring that there is an effective detection and response system to detect known and unknown threats. These four pillars can give you a good start on securing your business.
Last warning, work on your company’s cyber resilience
Do you think you won’t get infected or hacked because you are not an attractive target? Think again, because every business has a bank account and has sensitive data. Since most attacks are fully automated, the attacker doesn’t care who you are. As long as you can pay thousands of euros you are an ideal victim. Improve your company’s cyber resilience, before it’s too late.
Tip: Micro Focus launches CyberRes Galaxy, threat intelligence for CISOs

