After a severe remote code execution vulnerability was found in the popular NPM code library called Pac-Resolver, an update was released to patch it up. Developers who have used the package in their applications should make sure they update their dependencies to eliminate the bug.
They should also provide the necessary update to users to secure them. Essentially, any app using the vulnerable code to handle internet proxies could end up executing malicious code if it has booby-trapped proxy configuration information, which could have multiple sources.
The developer who found the flaw explains
Tim Perry, who makes a developer tool called HTTP Toolkit, explained how he discovered the flaw, which was disclosed and tracked a week ago as CVE-2021-23406 when adding proxy support to his software.
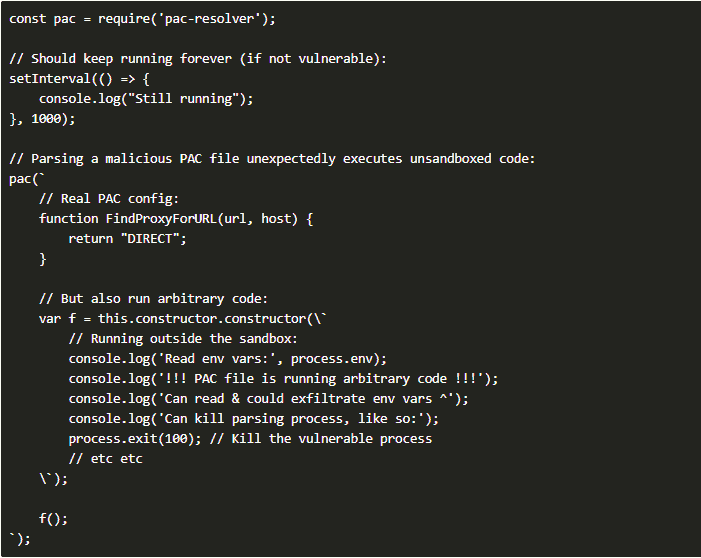
Pac-Resolver, downloaded more than three million times a week, providing support for PAC (proxy Auto-Config) files to instructHTTP clients which proxy to use for a particular hostname.
Perry explains that PAC files enable the distribution of complex proxy rules as one file that maps various URLs to their appropriate proxies. They see wide usage in enterprise environments and often need support in any software that may run in an enterprise environment.
Always check your dependencies
The file may distribute from a local network server, over HTTPS, or a remote server (a common method with its own standard called WPAD (Web Proxy Auto-Discovery Protocol)) to automate PAC file discovery.
Observing PAC files dates back to Netscape Navigator 2.0 in 1996, according to Perry’s explanation.
Anyone using a version of Pac-Resolver, Pac-Proxy-Agent, or Proxy-Agent before version 5.0 is potentially vulnerable to loading malware via the PAC file. Users must always review code dependencies to ensure mistakes like this don’t get through.