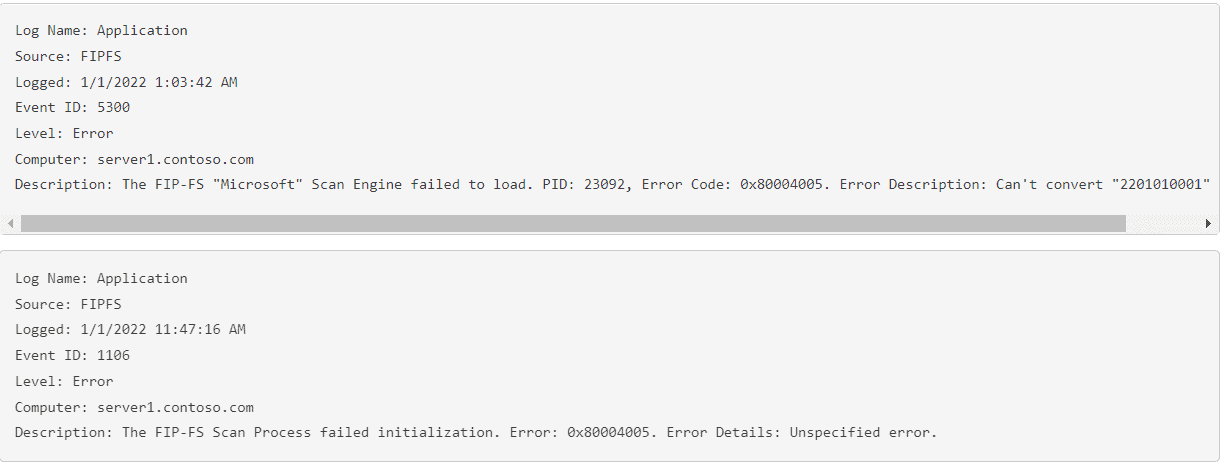
Microsoft released a quick patch for a Microsoft Exchange server bug that occurred on January 1 of this year. The bug prevented on-premises Exchange servers from sending emails.
The problem was caused by date checks after the year change. The bug caused Exchange Server 2016 and Exchange Server 2019 to fail to process the new date when checking email against a signature file. There is a maximum number of variables for this, and the variable for January 1, 2022 0:00 AM proved one too many. This caused the internal malware engine to crash and emails to get stuck in the queues.
Quick patch with automated script
Microsoft responded quickly as the issue affected all Exchange 2016 and -2019 versions worldwide. Administrators can automatically fix the problem using an automated script released by the tech giant.
Before rolling out the script, administrators must change the execution policy for PowerShell scripts by running ‘Set-ExecutionPolicy -ExecutionPolicy RemoteSigned’. Then, The Microsoft script must run on every Exchange mailbox server that uses an upgraded Exchange Management Shell to pull in anti-malware updates. Finally, the Exchange server must be restarted for the patch to work.
Administrators can also fix the problem manually, but that’s a long process. Microsoft plans to release an easier fix for the issue soon. The long-term fix should come in the form of an update for Exchange Server 2016 and 2019
Tip: Microsoft Exchange Server hacked – what are the consequences?