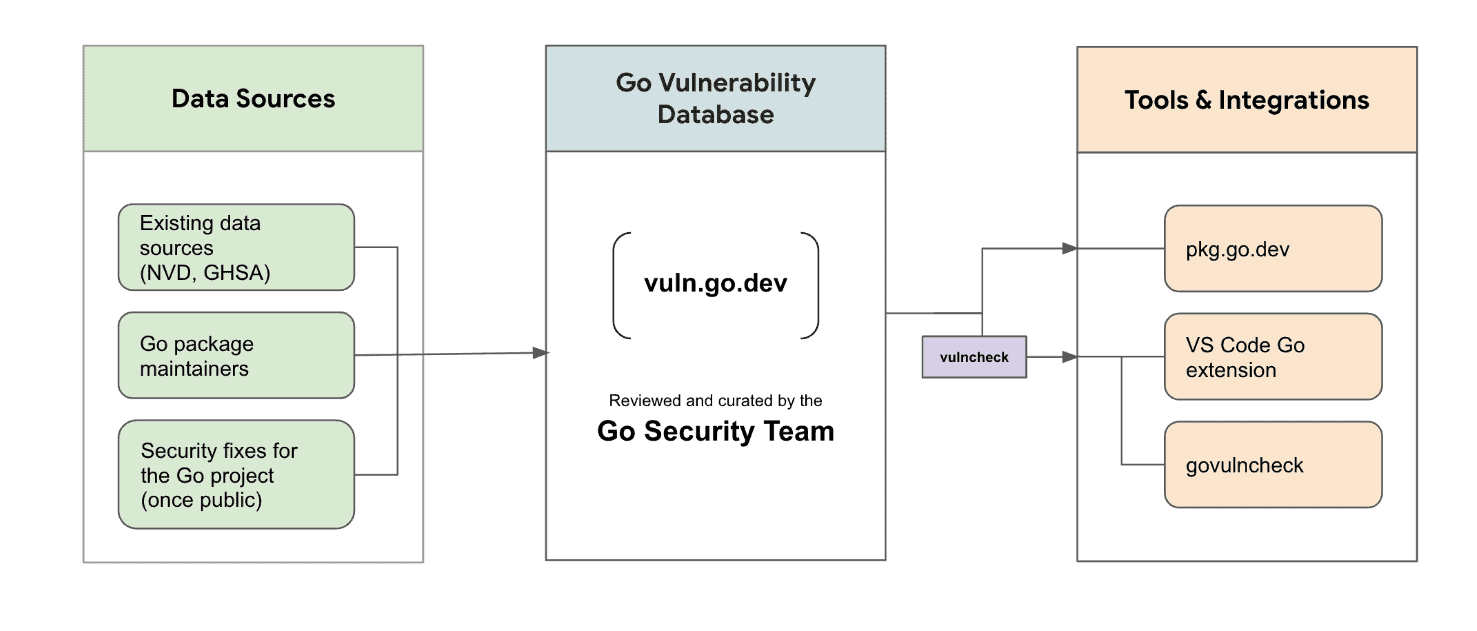
Go, Google’s open-source programming language, has a new tool for discovering vulnerabilities. The ‘govulncheck’ command allows developers to scan for vulnerabilities in code through an online database.
The Go development team says the command contacts the database at vuln.go.dev. The vulnerabilities stored on this site are managed by the Go security team and based on CVEs, GitHub Security Advisories and alerts from Go’s maintainers.
The tool is also available through a vulncheck package, which exports the functionality as a Go API. This helps integrate the functionality with third-party security tools.
Govulncheck
Once the tool has contacted the database, it analyzes the codebase of the project. The tool only reveals vulnerabilities that are relevant to the project. The tool reads the code’s functions to determine relevant risks.
The tool produces a static analysis of source code or the symbol table of a binary to restrict reports to vulnerabilities that could affect the application.
Fewer false positives
Ultimately, the workflow should produce fewer false positives. Nevertheless, the developers indicate that false positives cannot be avoided entirely, and will pop up from time to time. The tool is available immediately.
Tip: Google’s bug bounty rewards program now covers third parties
