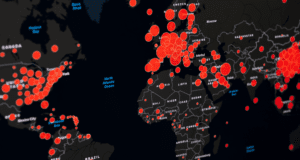
Log4j update: 60 variations of Log4Shell, hundreds of thousands of attacks
The severity of the vulnerability in Log4j is anything but theoretical. Cybercriminals are scanning ports wor...

The severity of the vulnerability in Log4j is anything but theoretical. Cybercriminals are scanning ports wor...

A mediocre security posture is often not the result of unwillingness, but of human error. With Security Advis...
Apple is about to face an investigation in Poland over whether its new rules on privacy and personal data pro...
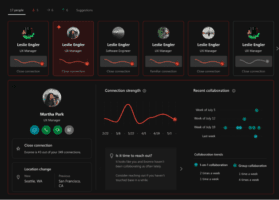
If you have ever wondered how much time you spend in meetings, talking to coworkers, or on the phone, you can...

Adobe introduces the Creative Cloud Express mobile app, adding a new tool to its various cloud-based solution...

Red Hat recently launched a beta version of its managed Image Builder service. This allows developers to bett...
Intel is having a tough time in the processor market --- and things aren't looking up for semiconductors eith...

Microsoft is moving towards the acquisition of Nuance communication and is awaiting European Antitrust agency...
The new release offers easier and safer refactoring and improves the CLI for Terraform Cloud and Enterprise. ...

Iron Mountain acquires ITrenew, giving it an edge in the refurbishing, marketing and sales of data center har...