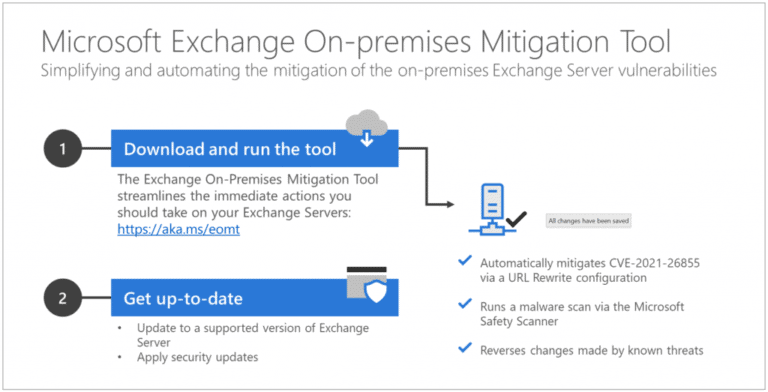
To assist administrators in resolving Exchange vulnerabilities, Microsoft has released a new tool. With this tool, administrators can install the most necessary patches in one click.
Microsoft has announced the so-called one-click mitigation tool in a blog post. The company says that on the basis of contact with support teams and partners it came to the conclusion that there was a need for a simple automated solution to close the vulnerabilities.
The tool consists of several components. The most important is a patch for vulnerability CVE-2021-26855, which attackers used to gain access to vulnerable Exchange servers. Furthermore, the latest version of Microsoft Safety Scanner is also included in the tool, which can remove malware resulting from the vulnerability if necessary. Any further changes made by the attackers are also reversed.
Temporary solution
Microsoft emphasises that the tool is not a definitive solution to the problems but describes it more as an interim solution for users who have not yet had the chance to address the issues properly. For example, the tool only closes the vulnerability that the attackers use to get in, not the three other vulnerabilities that allow them to spread further across the network.
Furthermore, Microsoft naturally tries to remove all possible hacks with Safety Scanner, but the company can hardly be sure that it has actually identified all malware. Therefore the company recommends keeping the tool running so that it can update itself with information about possible new attack techniques.
Vulnerabilities affect tens of thousands of organisations
Earlier this month, Microsoft released a patch for Exchange Server outside the normal update cycle. The company turned out to have found a gigantic leak, with which attackers could penetrate the servers and take over. Malicious parties had also already discovered the vulnerability and were eager to exploit it. Thousands of Microsoft Exchange users have already fallen victim to ransomware attacks. Microsoft is now wondering whether the attackers possibly found the vulnerabilities through a leak at Microsoft or a partner.
Tip: Microsoft Exchange Server hacked, what are the consequences?