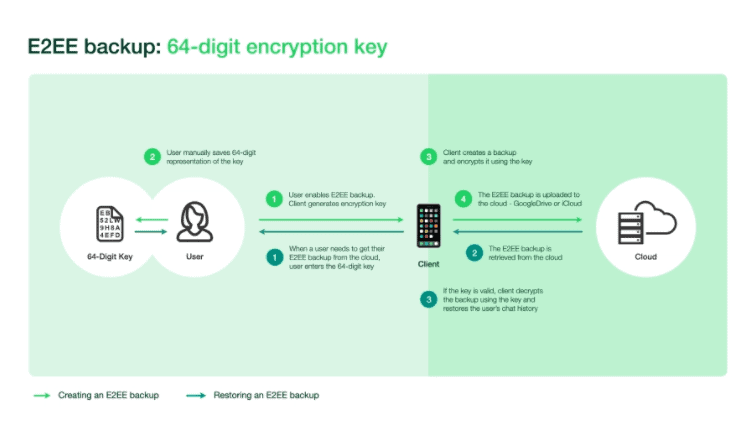
WhatsApp announced it will offer its users end-to-end encrypted backups later this year. Users will be able to choose how the encryption key is stored. The simplest storage form is for users to store the random 64-digit key themselves just like how Signal handles backups.
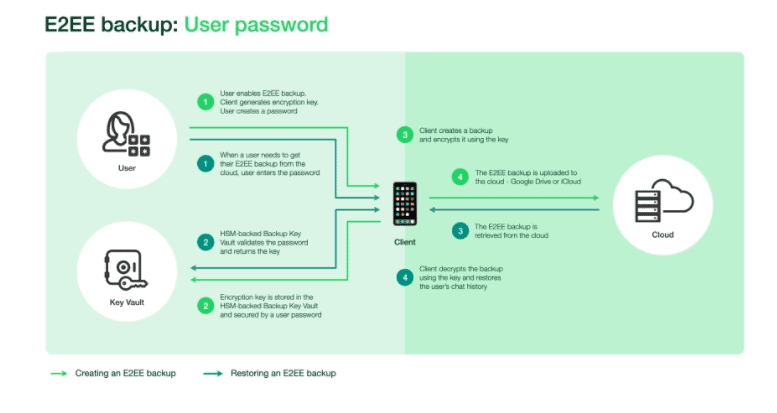
The users would need to enter this key when restoring backups. The other option is for the random key to be stored in WhatsApp’s infrastructure, called the hardware security module-based (HSM) Backup Key Vault, accessible through a user-created password.
How the keys are secured
According to a white paper by the company, the password would be unknown to WhatsApp, the user’s mobile device cloud partners, and other third parties. The HSM Backup Key Vault is responsible for enforcing password verification attempts and making the key permanently inaccessible after a certain number of incorrect login attempts.
The security measures, the white paper continues, provide the protection needed to stop brute force attempts to retrieve a key. For redundancy, the key will be distributed through several data centres run on a consensus model. WhatsApp said that it would know a key exists in the vault but would not know the key itself.
Source: WhatsApp
The sole owner of your backup
The backups store text messages, photos, and videos according to the user’s preferences. The backups are generated on the client as data files, then encrypted using symmetric encryption with a locally generated key.
After the backup is encrypted, it is stored in third-party storage like Google Drive or iCloud. Since the backups are encrypted with a key Google or Apple does not have, they are not capable of seeing your private data.
WhatsApp delayed an update (which was mandatory) to its privacy terms earlier this year to May.
