Two WordPress plugins have received updates to fix vulnerabilities. The security-focused Jetpack plugin is managed by Automattic, the company behind WordPress. In that instance, the company opted for a force install: 5 million websites are said to have already been patched.
Another plugin, Gravity Forms, requires users to update of their own accord in order to avoid being susceptible to a cyber attack. Gravity Forms is a form plugin for WordPress websites. Users can deploy it to create registration, payment and upload forms, for example. Gravity Forms mentions that major parties such as Unicef, Airbnb and NASA use it. In total, 930,000 websites make use of the plugin, Bleepingcomputer reports.
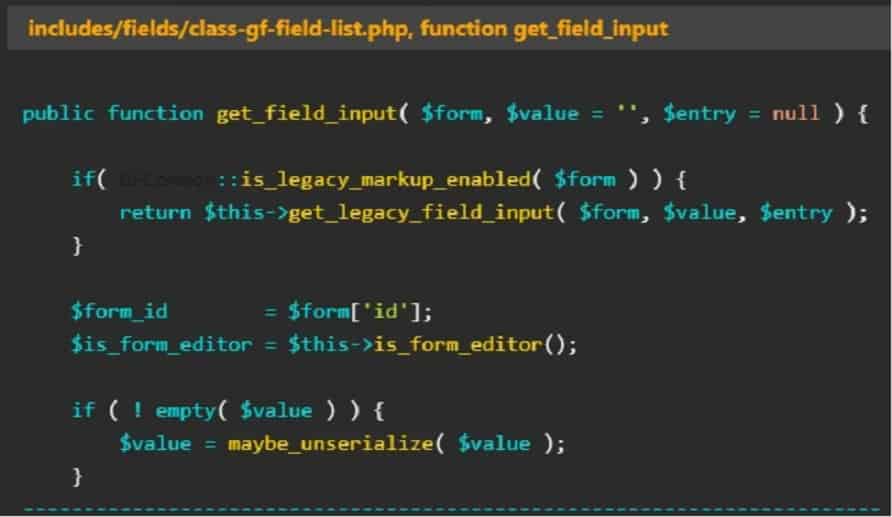
In the case of Gravity Forms, the vulnerability allowed a so-called PHP Object Injection, which, after several additional steps, allowed files to be changed or for data leaks to occur. PHP Object Injection can be used for a variety of purposes, such as code or SQL injections or Application Denial of Service. It was discovered on March 27 and patched with version 2.7.4 on April 11. The vulnerability could be triggered by a specific data entry in a Gravity Forms form (see image below).
WordPress itself
The Gravity Forms vulnerability must be actively patched by a user. WordPress itself uses a more resolute policy with the Jetpack plugin: 5 million websites received the update automatically.
This plugin offers free security options, performance info and website management improvements, Bleepingcomputer summarizes. Among these are backups, brute-force attack protection, secure logins, malware scanning and more.
An internal security audit reportedly detected an API vulnerability that had existed since version 2.0 (from 2012) of Jetpack. With version 12.1.1, this security hole has finally been closed, although there are no signs that malicious actors have actually exploited this vulnerability. That can’t ultimately be ruled out, of course.
A few months ago, we saw a similar action from WordPress: thousands of websites received a security update in March if they used WooCommerce Payments. Regardless, it is common that service plugins can be susceptible to attacks, as the recent Elementor Pro example illustrates.
