Salesforce customers became the target of the ‘PhishForce’ phishing campaign. The emails were set up in a way to slip past detection tools.
Cybersecurity researchers at Guardio Labs are on the trail of a new phishing technique. The attack is named PhishForce, a subtle reference to its target: Salesforce customers.
Detection tools mislead
Salesforce’s email service lets this phishing emails land in the inbox. Detection tools fail because hackers make the e-mail appear to be from a trusted sender.
Salesforce’s domain name is misused for this purpose. This domain name is only used in combination with the sender ‘Meta Platforms’. The combination is illogical and should be the first sign of the true sender of the email.
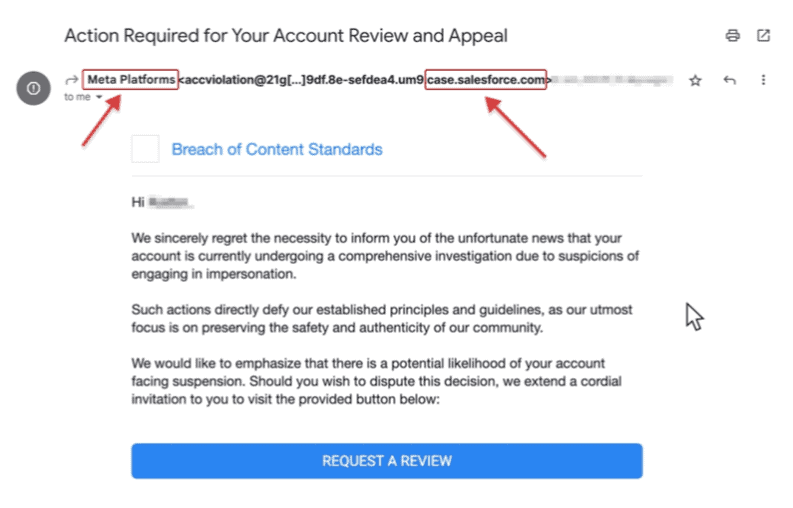
Source: Guardio Labs
Collecting login data
Hackers hoped to use the phishing campaign to extract Facebook login credentials. The email contains a link to a Facebook page where users are promised an online game. The page itself contains only completely different content.
By hiding the phishing website on a Facebook page, hackers are playing it smart. Facebook pages are another element that detection tools do not mark as potentially dangerous.
Companies already got time to find a solution
Guardio Labs is disclosing the details of the phishing campaign now that the problem is no longer an issue. In late June, Salesforce was notified of PhishForce and addressed the problem within the month. The Facebook pages have also been taken offline in the meantime.
Inside your mailbox, though, you should still be cautious. Placing a legitimate link in a phishing message to bypass detection tools is a common trick hackers use. Currently, the Google Accelerated Mobile Pages (AMP) URL is being abused to get phishing messages into businesses’ mailboxes.
