A phone that only connects to a threat actor: it’s possible in iPhones and other Apple devices running on iOS 16. Researchers at Jamf Threat Labs found a way to trick users into thinking airplane mode is enabled on their cell phone, when in fact the UI has been tampered with.
The team explains that airplane mode is commonly used these days for multiple purposes. Aside from shutting down network connections during a flight, it can also be a privacy tool. Those who do not want to be contacted can be completely isolated from the Internet at the touch of a button. Jamf notes that it is even recommended as a meditation method. Likewise, it’s a convenient way to extend battery life, for example, if an end user is only consuming downloaded content.
However, it is possible to mimic the visual characteristic of airplane mode. However, it is only possible if an attacker has already managed to infiltrate the device, informs Michael Covington, VP of Portfolio Strategy at Jamf. “In practice, this technique could be used to hide an attacker’s activities on the device as part of a more elaborate attack scenario. Before an attacker could take advantage of this, he would have to be able to execute arbitrary code with higher privileges.”
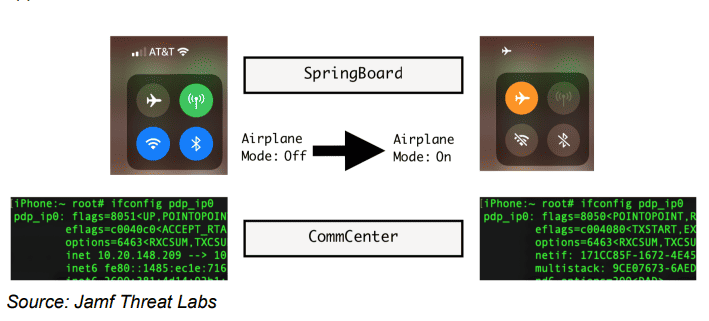
SpringBoard and CommCenter: two separate layers of iOS 16
Anyone who clicks on airplane mode activates two daemons, or background processes. First, SpringBoard causes the user interface to show that there are no more Wi-Fi, BlueTooth or cellular connections. Underneath, CommCenter goes to work disconnecting the actual connections.
By looking into iOS console logs, Jamf was able to find out where the activation of airplane mode occurs within the disassembler, which (as its name suggests) converts machine language into assembly language. By turning this feature off in the disassembler, the visual activation of airplane mode became effectively useless: the device remains open to the Internet with all previously enabled connections still active.
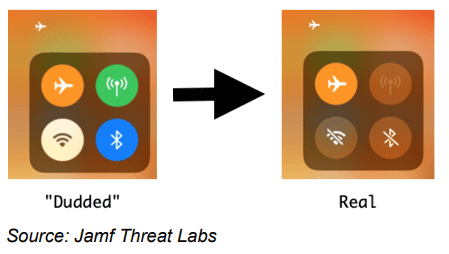
Jamf wasn’t done yet. In fact, there is another pretty clear piece of evidence that shows airplane mode is not working properly: all connections are still shown as active, which makes the edit look like a straightforward bug. To really fool it, Jamf used two Objective-C methods and inserted a piece of code that makes the icons look as the user would expect.
More fake (non-)features
The Jamf researchers then managed to get the Safari browser to join in on the façade as well. The team “hooked” a common Safari notification asking if network data may be used and converted it to the airplane mode notification. They were then able to figure out that CommCenter is told by the kernel when to send a notification.
The CommCenter daemon was also found to manage a file in an SQL database that controls cellular data access. By manipulating “flags,” the researchers were able to ensure that Safari did not get an Internet connection. At the same time, even the notification for the user suggests that airplane mode is on. This ensures that a link can remain with a threat actor, who can perform unwanted activities remotely.
Covington: “Jamf Threat Labs has created a proof of concept video showing how an attacker could use this technique, for example, for a ‘surveillance’ attack. When Fake Airplane mode is active, the attacker can turn on the camera and stream live from the device, without the user realizing it.”
For more details on the exact implementation of each step in setting up this fake airplane mode, check out Jamf Threat Labs’ blog.
More deception: Apple TV
Another way to trick iPhone users took place recently during the Defcon ethical hacking event in Las Vegas. A device worth less than 70 euros was able to spoof an Apple TV and steal passwords with it. Researcher Jae Bochs said he tested this capability with a Bluetooth device that prompted a notification to iOS devices to enter the Apple ID. However, he said he did not record any data, although a malicious person could have done so.
Also read: MacOS malware detection tool proves easy to bypass