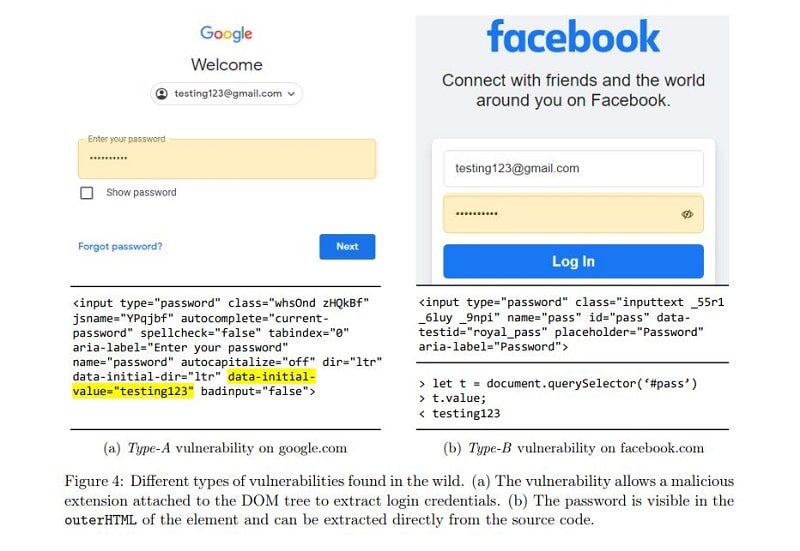
Researchers have succeeded in using a self-developed extension for Chrome to steal passwords from the source code of websites in plain text. Many extensions also turned out to be dangerous and websites are prone to data leaks due to the extension.
University of Wisconsin-Madison researchers managed to upload the Chrome extension to the Chrome Web Store. The extension makes it possible to steal passwords stored by the browser in plain text in the source code.
Access to HTML DOM
The researchers focused on the practice of browser extensions to allow unrestricted access to the DOM tree of the Web sites they load. This potentially gives them access to sensitive elements such as user input fields.
The extension thus gains access to all the data visible in the source code and allows it to be extracted. Moreover, according to the researchers, the extension can abuse the DOM API to directly extract the value of inputs at the time users enter them. This circumvents the masking of these sensitive inputs to protect them.
Manifesto V3 not enough
Google Chrome did implement the Manifest V3 protocol against this. This protocol should prevent API abuse and prohibits extensions from retrieving remote code that can bypass detection. Furthermore, the protocol prohibits the use of “eval statements” that should prevent the running of arbitrary code.
According to the researchers, however, this does not make much sense. This is because Manifest does not introduce a security boundary between extensions and Web pages. This leaves the problem with content scripts.
Extension as GPT assistant
To test their claims, the University of Wisconsin-Madison specialists therefore developed a Chrome extension capable of performing password-grabbing attacks. The extension was offered as a GPT-based assistant with the Chrome Web Store and contained no malicious code. With this, the extension managed to pass the review process and was included in the Web Store.
Dangerous extensions and ‘leaky’ websites
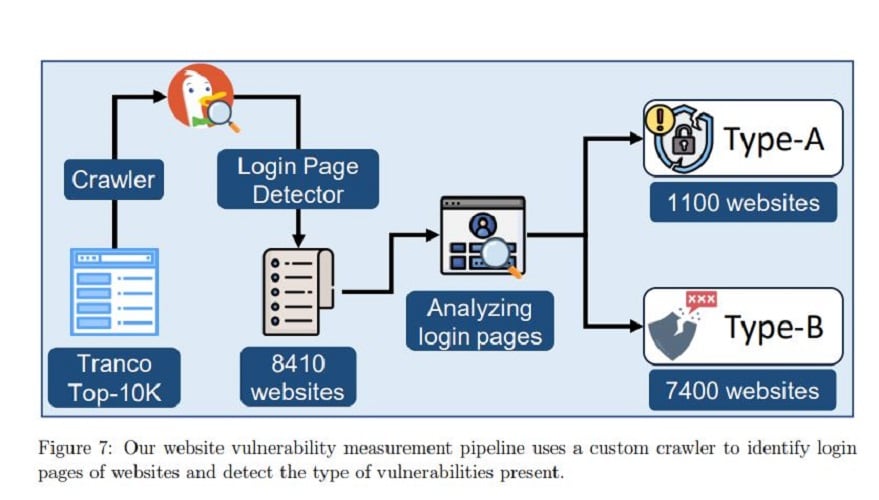
Further research revealed that of the 10,000 most frequently used Web sites, 1,100 store passwords in plain text in the HTML DOM. In addition, another 7,300 websites were vulnerable to DOM API access and to directly extracting input values from end users.
In addition, 17,300 extensions in the Chrome Web Store, 12.5 percent of the total, were found to allow conditions for extracting sensitive information from Web sites. These include popular ad blockers and shopping extensions.
Finally, the researchers discovered a list of popular Web sites that do not have protection against stealing passwords and other sensitive data. These include gmail.com, cloudflare.com, facebook.com, citibank.com, irs.gov, capitalone.com, usenix.org and amazon.com.
Tip: Chrome can now take down malware masquerading as an extension