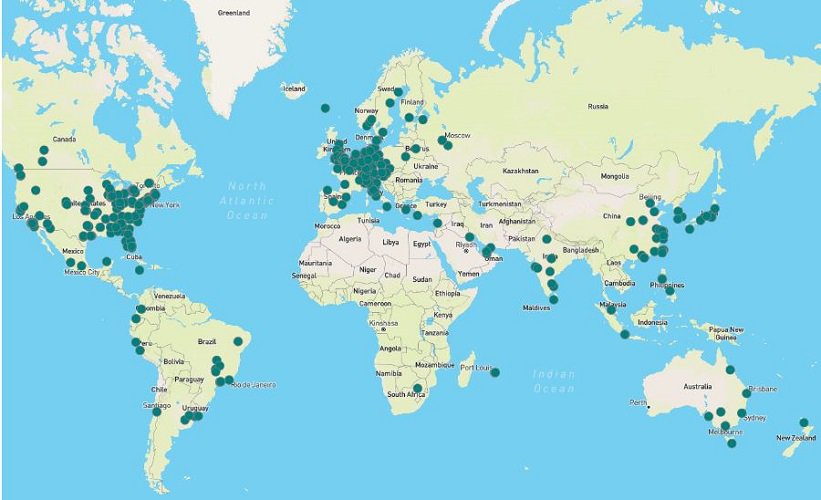
The CVE-2023-3519 vulnerability in Citrix NetScaler gateways discovered in September is currently being exploited by hackers on a massive scale.
So say researchers at IBM X-Force. Currently, around 600 unique IP addresses are said to have been detected, indicating that hackers are taking advantage of the vulnerability. Widespread detections have occurred in the U.S. and Europe.
The vulnerability, discovered as a zero-day in July, primarily affects Citrix NetScaler ADC and NetScaler Gateway devices. Apparently, there are still enough unpatched devices visible on the Internet to allow the infection to propagate.
The vulnerability is used by hackers to perform RCE attacks to steal login credentials. This includes injecting a malicious JavaScript for stealing login credentials into the index.html login page of an affected Citrix NetScaler device.
Also read: Citrix servers have backdoors everywhere, leading to a false sense of security
New breach indicator found
IBM X-Force researchers have not yet managed to find out who is responsible for the continuing attack. However, they did manage to find a new “artifact” that can be used to detect that a CVE-2023-3519 attack is taking place.
This artifact is located in the Citrix NetScaler application crash logs associated with the NetScaler Packet Processing Engine (NSPPE). In these, the security experts found certain timestamps that showed similarities to the file system timestamps of the PHP web shells used in the exploits.
This meant that the IBM X-Force security experts were able to see the commands sent to the web shells as part of malicious activity following an exploit.
IBM X-Force is strongly urging that unpatched Citrix NetScaler gateways be patched as soon as possible.