Microsoft recently published details about the hyper-aggressive Octo Tempest hackers. This hacker gang carries out its attacks through various methods and demands a ransom for stolen data through threats.
According to Microsoft, Octo Tempest is one of the most aggressive hacker gangs it has encountered recently. Instead of the hackers stealing or encrypting data through ransomware attacks, Octo Tempest primarily pressures companies to pay up. Their threat is thus dissimilar to that of the many ransomware gangs: those who don’t pay up will see their data become public.
In putting pressure on affected companies, the hackers do not hesitate to threaten violence.
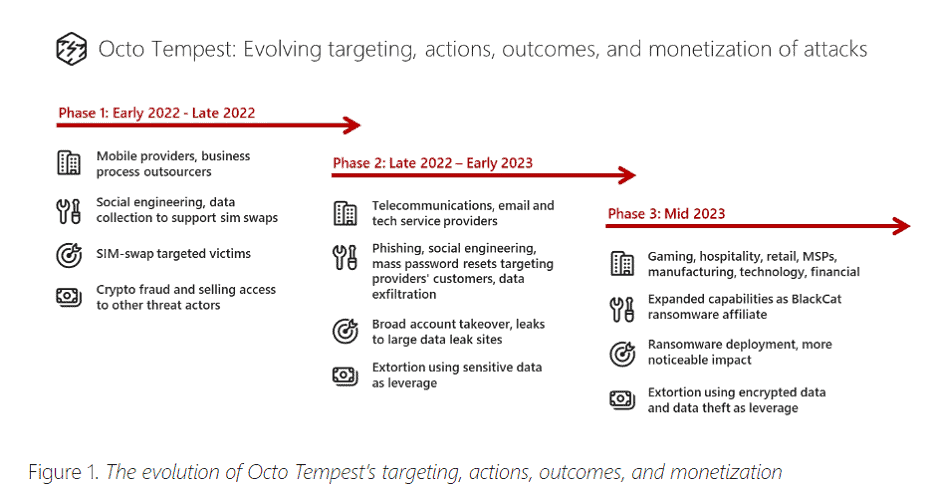
The hackers have been carrying out their attacks since 2022, the tech giant indicates. In doing so, the hackers use a variety of attack methods, including tactics that are rarely found in other known hacker groups. Examples include so-called adversary-in-the-middle (AiTM) techniques, advanced social engineering, SMS phishing and SIM swapping.
Long time active and increasingly sophisticated
Microsoft notes in the investigation that the hacker gang has become increasingly sophisticated over the course of its existence. From late 2022 to early this year, Octo Tempest also began attacking cable telecom, email and tech companies. In addition, it started demanding ransoms from this point on.
Halfway through this year, Octo Tempest became an affiliate of the ransomware-as-service (RaaS) gang ALPHV/BlackCat and the hackers started using the ALPHV/BlackCat payloads from extorting VMware ESXi servers that turned out to be vulnerable. Naturally, this also allowed them to reach more victims from many new sectors.
In the most recent campaigns, Microsoft security specialists discovered, different attack methods were used to attack mainly hybrid environments, steal data from them or encrypt them.
Technical employees targeted
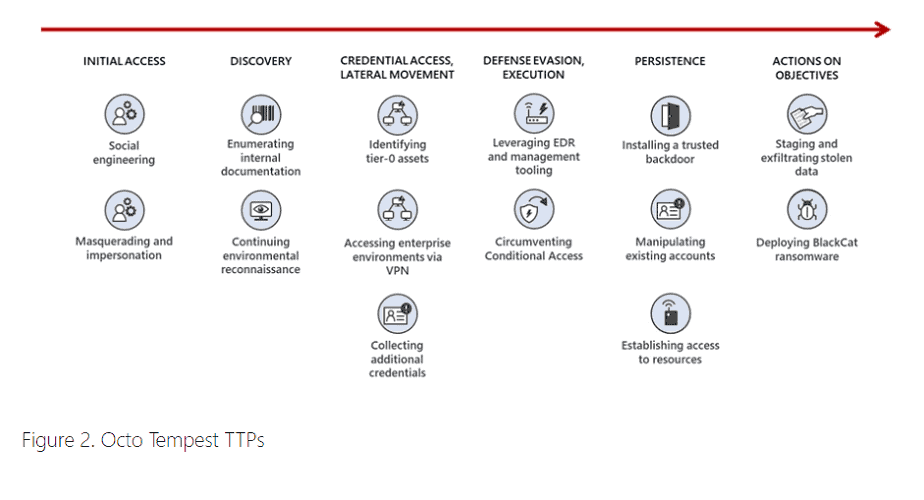
The attacks in question primarily target technical administrators, such as through social engineering attacks. Examples include the targeting of support and help desk employees who often have sufficient access rights, ultimately allowing the hackers to gain access to underlying systems.
In their attacks, Octo Tempest’s hackers employ various techniques to hide their presence. They also pursue persistence in the affected systems and environments for attacks at a later time, Microsoft indicates.
Combat methods
Octo Tempest hackers often use well-known communication platforms such as Slack, Zoom, and also Microsoft Teams to attack and threaten their victims. Microsoft is therefore urging companies to use mainly so-called out-of-band communication channels that should give them more security.
Other possible measures companies can take to secure themselves against Octo Tempest activities best include equalizing privileges in Microsoft Entra ID and Azure, segmenting Azure landing zones, implementing conditional access policies and authentication methods, such as FIDO-compliant MFA, and creating and sustaining awareness about this threat among (internal) employees.
Also read: Ransomware gang Ransomed.vc abuses GDPR to receive ransom money