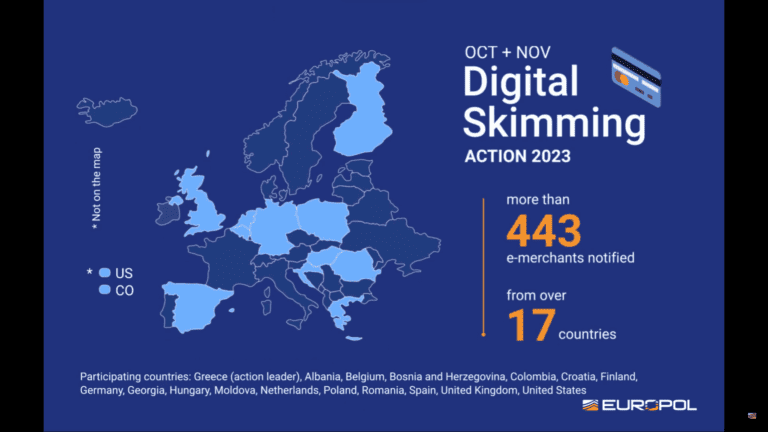
Europol announces that credit card data from 443 online stores from 17 countries has been stolen. Seventeen countries, a specialized EU unit and private security companies are working together to crack down on “digital skimming.”
The investigation was conducted over a period of two months by Europol and its partners, including security parties Group-IB and Sansec. From Brussels, the European Union Agency for Cyber Security (ENISA) contributed to the work.
It’s unknown which online stores have been hit. Needless to say, that makes it difficult for potential victims to know if they have been compromised, so until further notice, there’s nothing to do but check credit card data carefully provided it has been used in an online store.
Greece took the lead on the investigation, while the EMPACT program from the EU is targeting the criminals behind the fraud. Last month, a massive operation to bust a Ukrainian ransomware gang took place under the same program.
Digital skimming
Digital skimming has the same objective as physical skimming: to steal payment and transaction data from unsuspecting victims. Instead of a criminal looking over the shoulder of an ATM user, they deploy malware on the site of the online store in question. By exploiting software vulnerabilities, an attacker first infiltrates the digital infrastructure behind the website. Then, malware is placed somewhere in the payment chain, which allows the criminal in question to steal credit card information. Such an action usually goes unnoticed, especially since the site itself will otherwise be functioning properly.
Websites can take several actions to secure their systems, Europol points out. For example, it recommends the use of monitoring and detection software. In addition, employees and users should only gain access to website resources through multi-factor authentication. Access to the editing of payment systems should only be possible through a small group of IP addresses, while careful Content Security Policy (CSP) and Subresource Integrity (SRI) measures should be taken. Europol additionally recommends an external audit so that a security party can assess whether there are vulnerabilities to exploit.
Finally, Europol suggests training employees to recognize phishing and not to click on suspicious links.
Also read: Qakbot malware returns with phishing attack on hospitality industry