The so-called Chameleon malware is not new, but it has worrying new capabilities. Android users can download an otherwise normally functioning app without ever realizing that Chameleon is running in the background.
Discovered in April, Chameleon is known as a “banking trojan,” an umbrella term for malware that attempts to steal login credentials and other sensitive data. It initially targeted Australian and Polish users in particular. Government and banking apps were fitted with malware via the so-called Zombinder service. For the user, there is no evidence of having installed malware. The APKs carrying Chameleon disguise themselves as Google Chrome.
Larger scope, more trustworthy appearance
The original version of Chameleon already pulled off many malicious actions. For example, it asked the victim to be allowed to use Accessibility tools, after which it appropriated additional permissions for a so-called DTO (Device Takeover) attack, disabled Google Play Protect and prevented itself from being uninstalled. It then stole all kinds of sensitive data, which made MFA mostly already circumventable.
Now BleepingComputer reports that a new version has emerged. ThreatFabric researchers have been tracking the malware for some time and reported this week that Chameleon has expanded in scope. For example, it now also targets Android users in the United Kingdom and Italy, again disguising itself as a Chrome app.
By exploiting HTML code, Chameleon manages to deploy accessibility options within Android 13, including “Restricted Settings.” According to ThreatFabric, this has made the malware even more powerful. It starts with the same request towards the Android user to turn on the Accessibility tools. The way the malware now asks for access looks more trustworthy than before:
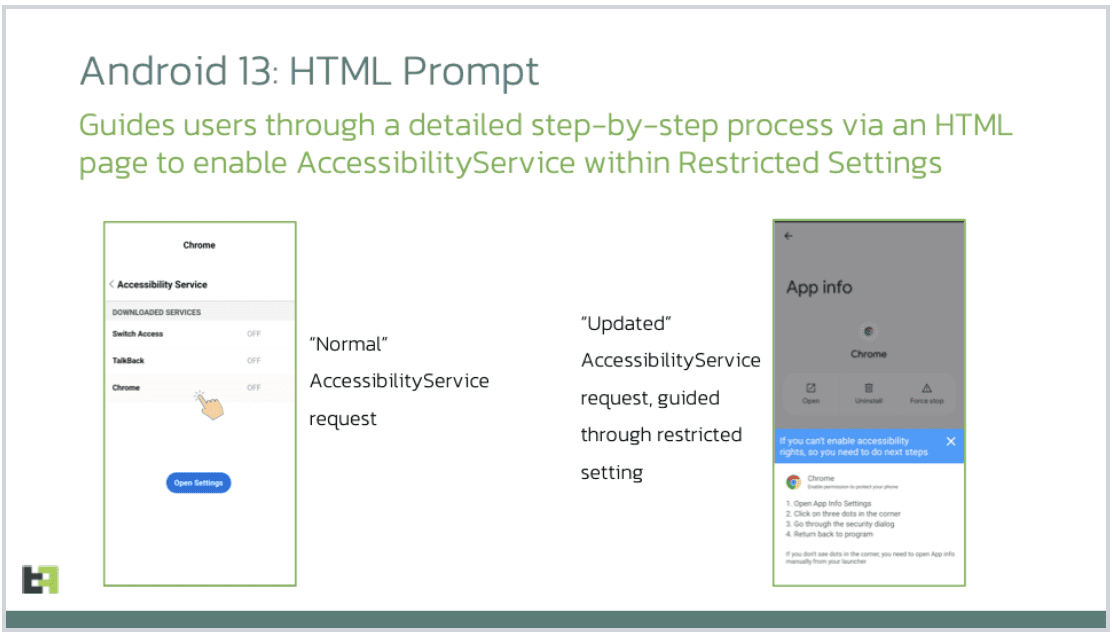
Biometric check bypassed
The biggest difference from the previous Chameleon variant is the fact that the malware can now bypass the biometric check. It does this with the command “interrupt_biometric” and forces the so-called AccessibilityEvent action. Specifically, this involves asking the user to open the phone with the PIN. As the application monitors the inputs, it recognizes which code is in use. After that, it is possible for the attackers to schedule tasks and steal sensitive data.
Since it’s better to never face the issue in the first place, Android users should ideally limit themselves to installing apps from official sources. Also, Play Protect should be on at all times.
Also read: Millions of phones already infected by malware out-of-the-box
