Fortinet is again warning of a critical vulnerability, this time in FortiOS SSL VPN. The vulnerability enables a remote execution code attack and is reportedly already being actively exploited.
Fortinet found another vulnerability in one of its products. This time it is in FortiOS SSL VPN. The vulnerability CVE-2024-21762 / FG-IR-24-015 has been defined as highly critical and allows hackers to launch an RCE attack via malicious requests.
The vulnerability is reportedly already being exploited, but the security and networking specialist does not disclose any details.
Solution with updates
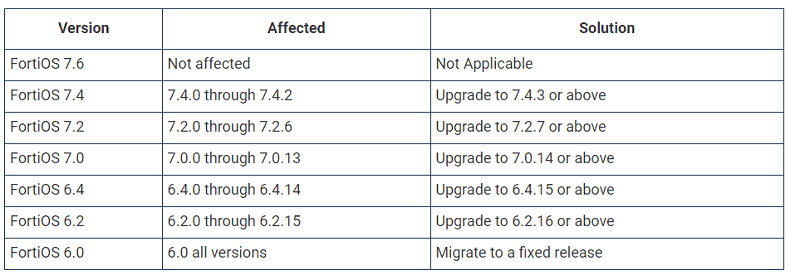
An overview of affected versions of FortiOS and the desired update recommendations are clearly provided by Fortinet:
To users who cannot upgrade immediately, the security and network specialist advises disabling the SSL VPN feature on FortiOS devices.
In addition to this vulnerability, Fortinet also discovered one other critical vulnerability, CVE-2024-23113, and two medium vulnerabilities CVE-2023-44487 and CVE-2023-47537. These three are not actively exploited at this time.
Other reports of vulnerabilities
Fortinet has been dealing with many vulnerabilities in its products lately. Recently, two extremely critical vulnerabilities in the FortiSIEM solution were detected that could potentially have a major impact.
In addition, the MIVD discovered that Fortinet’s software was also actively abused by Chinese state hackers to penetrate a network of the Dutch Ministry of Defense. The security and network specialist has since confirmed the attack. Volt Typhoon was behind the attack. Through the attack, the so-called COATHANGER malware for FortiGate devices was allegedly rolled out.
Also read: How Chinese cyber spies targeted the Dutch Ministry of Defense