Despite quantum computers not being in existence yet, there is an increasing demand for quantum-safe communications. Apple says iMessage will guarantee this with PQ3 in the near future. What does this look like?
Apple announced this week that it will provide iMessage with PQ3 encryption. This method, one of several “quantum-proof” encryptions, has already been implemented in preview versions of Apple’s operating systems; iOS 17.4, iPadOS 17.4, macOS 14.4 and watchOS 10.4 will eventually receive support for it as well.
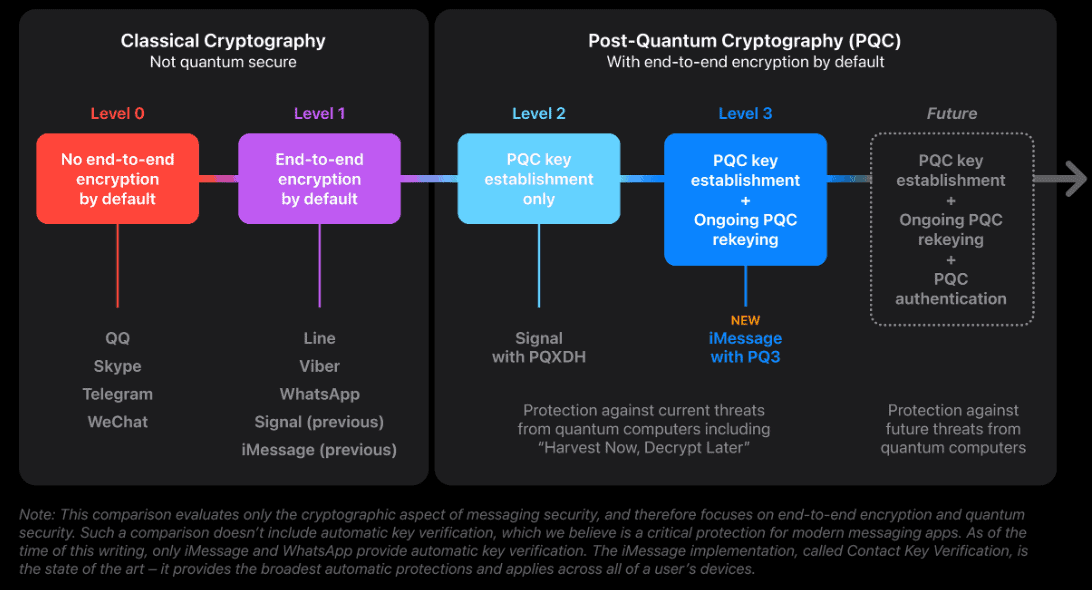
iMessage debuted with end-to-end encryption in 2011, similar to implementations in WhatsApp and Signal. Apple cites that Signal is already one step ahead of that with a PQXDH update. However, Apple doesn’t think that’s enough, because this form of quantum-proof encryption could be cracked by obtaining the keys. That’s why PQ3 revolves around ever-changing keys after messages are sent. A single compromised key shouldn’t ever cause a leak.
Decrypt Later problem requires urgency
When we spoke to Eurofiber about this issue earlier this month, it turned out that proposed post-quantum encryptions can sometimes still be cracked at lightning speed. At the time, Innovation Officer at that company Marc Hulzebos pointed out that we also still don’t know what quantum-secure encryption has to defend against. Quantum computers capable of running Shor’s algorithm do not yet exist, which is the criterion for establishing that all conventional forms of encryption can be cracked rapidly, rendering them fundamentally weakened.
However, it was also pointed out that we already need to move toward quantum-proofing, something Apple confirms. It describes the attack scenario as Harvest Now, Decrypt Later, in which stolen encrypted material is cracked as soon as the technology allows. This could include everything from state secrets to critical IP for advanced devices or private communications with sensitive personal information that must be kept secret for a long time or permanently. For that reason, Apple is moving forward with this iMessage innovation in 2024, and not just when quantum computing is ready to go.
Will others follow?
Although Apple has been providing iMessage with end-to-end encryption since its introduction, there are plenty of alternative apps that aim to promise the most secure communication going forward. WhatsApp and Signal are also innovating with new methods to ensure user privacy, but have not yet announced an ongoing PQC rekeying implementation. It is presumably only a matter of time before they do, given their emphasis on security.
Incidentally, classical cryptography still plays a role in iMessage’s PQ3 encryption. Sender authentication and the key still run on classical methods because, according to Apple, these mechanisms will not be susceptible to quantum computing in a way that harms the actual confidentiality of communications. Only if an attacker is in possession of a quantum computer and manages to intercept the key when a message is sent (Man-in-the-Middle attack), could a message be intercepted. By the time such a system is actually available, Apple may have developed other protection methods.
Also read: Eurofiber to build quantum-encrypted network for Port of Rotterdam