The recently discovered Linux backdoor GTPDOOR allows cybercriminals to access their core networks through components in the network environments of mobile telecom operators.
Research by security expert HaxRob has uncovered a previously unknown Linux backdoor, GTPDOOR. The backdoor is said to be exploited by the hackers of the LightBasin gang. This gang mainly carries out attacks on telecom operators worldwide to gather intelligence.
Systems affected
Two versions of GTPDOOR have been found. They primarily affect older Linux versions, specifically older Red Hat Linux versions. Both versions were uploaded to VirusTotal late last year, bypassing antivirus engines.
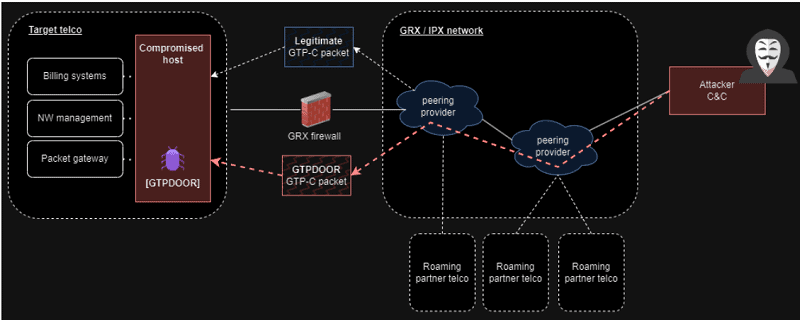
The malware targets systems near the GPRS Roaming Exchange (GRX) mobile network component for data roaming. These include the Serving GPRS Support Node (SGSN), Gateway GPRS Support Node (GGSN) and P-GW (Packet Data Network Gateway (for 4G LTE)) systems.
These systems are responsible for routing and forwarding “signaling” for roaming and user plane traffic, and are more open to the public internet. According to HaxRob, this makes them an easier target for access to mobile carriers’ core network.
Attack path
The backdoor abuses the GPRS Tunnelling Protocol Control Plane (GTP-C) to perform hidden Command & Control (C2) communications.
Through the GTP-C, it is possible for the backdoor to “mix” with legitimate network traffic. This way, it uses permitted ports not controlled by security applications. To disguise itself more, GTPDOOR can also change its process name to match legitimate system processes.
In doing so, the malware “listens” for specific GTP-C “echo requests” or “magic packets” to “wake up” and execute a particular command on the host. The results of this are sent back to the operators.
Furthermore, these ‘magic packets’ are authenticated and encrypted with a simple XOR key. With this, LightBasin’s hackers ensure only authorized operators can control the malware.
Features versions
Otherwise, the two separate versions of GTPDOOR each have their features. Version 1 installs a new encryption key for C2 communication. It then writes arbitrary data to a local ‘system.conf’ file, executes arbitrary shell commands, and returns the output.
Among other things, GTPDOOR v2 specifies IP addresses or subnets that allow communication with the affected host via an Access Control List (ACL) mechanism. It retrieves an ACL list to allow dynamic adjustments to the backdoor’s network permissions, and cleans up the ACL to reset the malware.
Fight
Telecom operators can defend against the GTPDOOR backdoor by monitoring the network for unusual raw socket activity, unexpected process names and specific malware indicators such as duplicated syslog processes.
According to HaxRob, measures such as GTP firewalls with strict rules according to GSMA security guidelines 1 and 2, among others, are also very useful. This is to filter out malicious packets and connections.