Researchers at Austria’s Graz University of Technology have discovered a new cross-cache attack that directly impacts the Linux kernel. The attack bypasses modern kernel defense methods and creates arbitrary read/write capabilities.
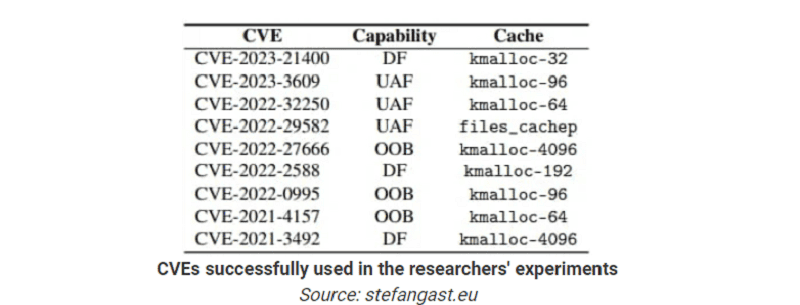
According to the researchers, Linux kernels v5.9 and the latest v6.2 are susceptible to the cross-cache attacks that provide arbitrary read/write capabilities. For this purpose, nine existing CVE vulnerabilities are exploited on both 32-bit and 64-bit VMs.
Worryingly, Graz University of Technology specialists said, the attack could succeed despite actively used modern kernel defense mechanisms such as Supervisor Mode Execution Prevention (SMEP), Supervisor Mode Access Prevention (SMAP) and Kernel Address Space Layout Randomization (KASLR).
The new attack technique uses a limited “heap” vulnerability. This vulnerability allows read/write capability to be applied at will, enabling escalating privileges or “escaping” from containers.
Memory management attack
The attack exploits how Linux manages memory efficiently and securely. The OS does this by allocating and not allocating memory chunks or ‘slabs’ for different types of data structures.
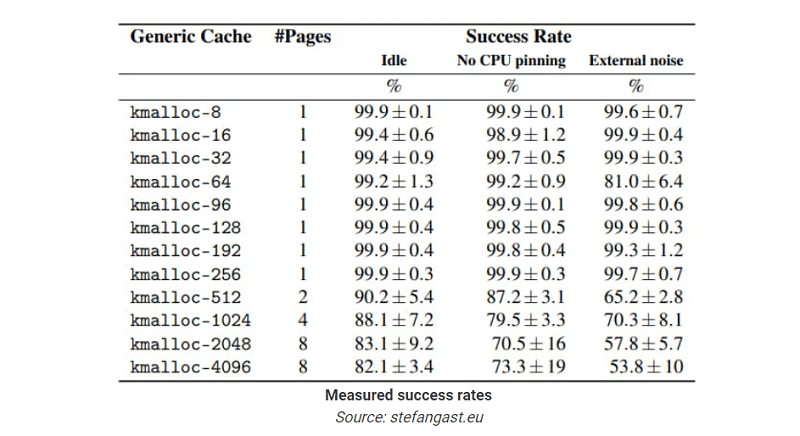
Flaws in this memory management allow attackers to corrupt or manipulate data structures, a type of cross-cache attack. While these are often ineffective, the now-discovered SLUBStick achieves a 99 per cent success rate.
It uses the aforementioned heap vulnerability that modifies the memory allocation process. In addition, the attack method uses a side-channel to determine the exact moment of whether or not to allocate the slab. This allows them to predict and control memory reuse.
The latter makes the 99 per cent success rate possible and using SLUBStick very practical.
Many implications
To perform side-channel attacks, attackers must have local access to a device with code execution capabilities. Also, the attack requires the presence of a heap vulnerability in the Linux kernel being used.
Despite this limitation, attacks can eventually achieve privilege escalation and “container escape” and bypass defense mechanisms. With privilege escalation, attackers can gain root access and therefore perform unlimited actions, among other things.
Through container escape, they can break out of sandbox environments and gain access to the host system. Eventually, in a post-exploitation phase, SLUBStick can modify kernel structures or hooks for persistence. This then makes the malware even more difficult to detect.
Also read: Makers of infamous xz backdoor cleverly managed to cover their tracks, analysis shows