Cybercriminal IntelBroker claims to have obtained sensitive data from Zscaler and recently put it up for sale. The zero trust specialist has not confirmed any breach, but is investigating a possible incident regarding misappropriated data. Whether the two messages are related remains unclear for now.
Known cybercriminal IntelBroker recently put up for sale a dataset on the hacker forum BreachForums for ‘trusted members’. This set allegedly contained sensitive information from a well-known cybersecurity company.
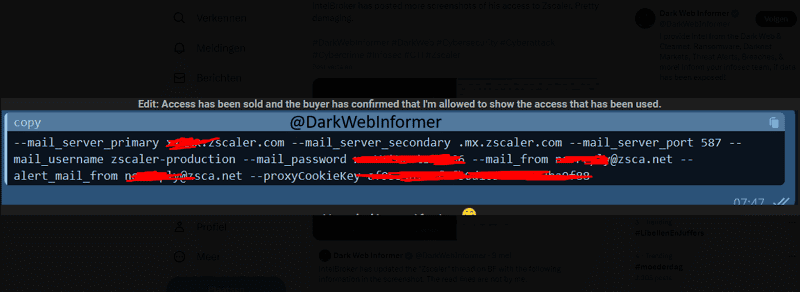
The data for sale apparently consists of confidential and highly critical logs full of login information. The latter would include such data as SMTP Access, HAuth Pointer Auth Access, SSL Passkeys, and SSL Certificates.
Zscaler denies hack
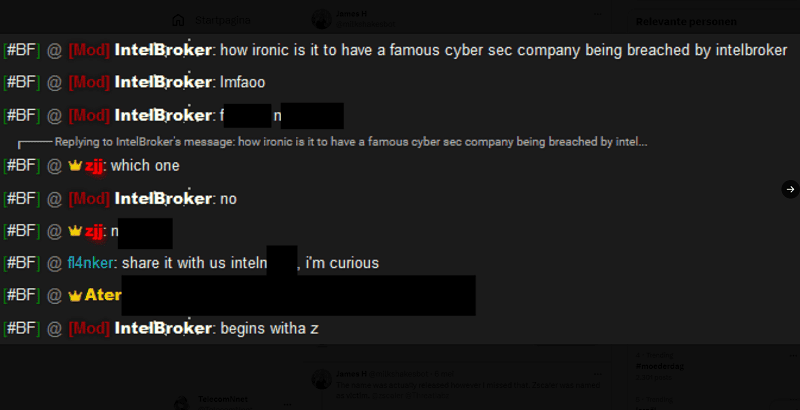
Although the cybercriminal did not disclose the name of the affected security company, experts suspect it may be Zscaler. These rumours were further fueled by the hacker teasing that the name of the affected company begins with a ‘Z’. Zscaler itself disclosed it was investigating an unspecified security incident.
According to Zscaler, this investigation led to the preliminary conclusion that no hack of its systems had taken place and that no data had been stolen. However, an isolated test environment on a single server was found to have an open connection to the Internet. This server contained no customer data and was also not connected to the zero trust specialist’s infrastructure and other systems.
Breach claimed anyway
Nevertheless, IntelBroker later claimed that Zscaler was indeed involved. At the request of the data buyer, the disclosure of the hack victim allegedly being Zscaler was withheld for some time.
IntelBroker accompanied its claim with screenshots and also stated that this was not data from the test environment discovered by Zscaler.
Zscaler itself has stopped responding to these latest allegations. In its latest statement, the company indicated only that there is no impact on its own customer and production environments and that the investigation into the test environment is continuing with the help of outside experts.
Screenshots in this post taken from @milkshakesbot on X.
Also read: Zscaler attracts micro-segmentation platform with acquisition of Airgap