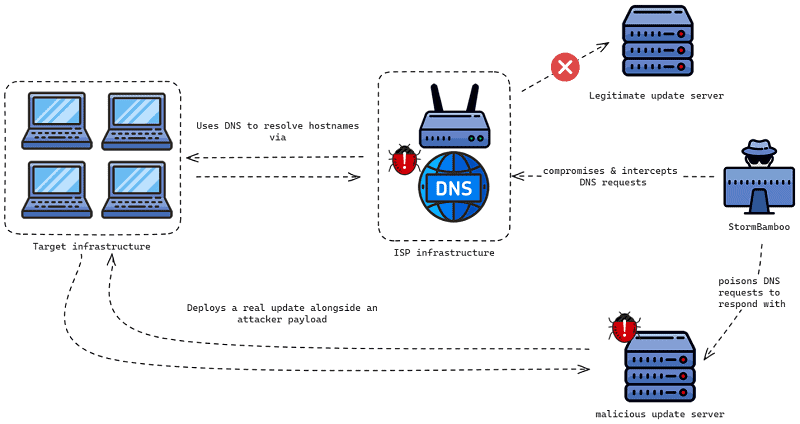
Hackers have succeeded in attacking Windows and Mac systems via software updates distributed through insecure Internet connections from a legitimate Internet provider, using a MiTM attack to take over the infrastructure.
The possibly Chinese hacker gang StormBamboo, also known as Evasive Panda, has been conducting malware attacks on Windows and Mac systems via a legitimate Internet provider since mid-2023, Volexity security experts discovered.
The systems were attacked via software updates for apps delivered over insecure Internet connections from the respective Internet provider. To do this, StormBamboo hacked routers or other infrastructure devices of the provider. This enabled them to use a Man-in-the-Middle (MitM) attack to modify DNS answers for legitimate hostnames.
The affected apps include 5KPlayer, Quick Heal, Rainmeter, Partition Wizard and those from Corel and Sogou.
Infrastructure hijacking
The hackers were able to take over the provider’s infrastructure because the update mechanisms did not use TLS or cryptographic signatures to authenticate the affected connections or the downloaded software.
Through the MitM attack, StormBamboo could redirect the attacked end users to malicious servers instead of those of the affected app developers. These redirects also worked when end users, instead of the ISP’s “normal” DNS server, used non-encrypted public DNS services such as Google’s 8.8.8.8 or Cloudflare’s 1.1.1.1.
According to Volexity’s security experts, this method of attack was very cleverly set up. The only way end users could have fended off the attack was to use DNS over HTTPS or DNS over TLS. This would have assured them that the search results for the DNS answers had not been manipulated. Furthermore, not using all apps that provide unsigned updates over insecure connections would have been a possible solution.
Other rogue method
StormBamboo also uses another method for “poisoning” DNS answers, Volexity further discovered. This method has also been used to hijack the Microsoft domain www.msftconnecttest.com. The tech giant uses this domain, among other things, to determine whether Windows devices are actively connected to the Internet.
By replacing the legitimate DNS for this purpose with an IP address pointing to a malicious site, the hackers were able to intercept HTTP requests intended for each host.