The recently discovered BingoMod malware for on-device fraud is very dangerous. This malware takes over Android devices and can not only plunder victims’ bank accounts but also remove all traces by wiping the affected devices.
The Android malware discovered by Cleafy specialists is currently being actively distributed and poses as a legitimate mobile security tool. Victims are persuaded to install the malware through phishing text messages.
Common “security tools” include APP Protection, Antivirus Cleanup, Chrome Update, InfoWeb, SicurezzaWeb, WebSecurity, WebsInfo, WebInfo and APKAppScudo. The logo of the free AVG AntiVirus & Security tool available in Google Play has also been misused.
The malware is said to be the work of a Romanian developer, but hackers from other countries may also be involved.
Operation BingoMod
During installation, the malware asks for access to the so-called Accessibility Services on Android devices. This service provides additional control over the affected device.
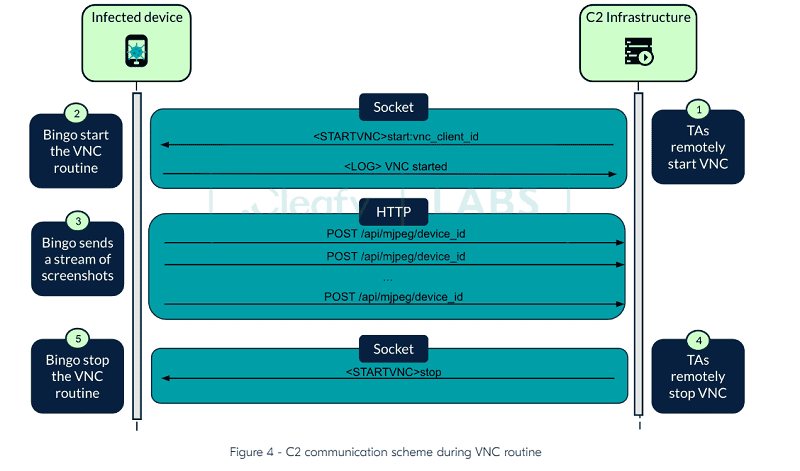
Once active, the malware creates a socket-based channel for executing the on-device fraud (ODF). This channel receives the commands from the hackers. In addition, an HTTP channel is set up to send a feed of active screenshots and intercept text messages, allowing near real-time attacks.
This allows the hackers to send arbitrary commands to the affected device, such as clicking on a particular spot, requesting login and other access credentials, entering text in a specific input element and launching an application.
This makes it possible to attack banking apps, stealing up to 15,000 euros per transaction.
Manual overlay attacks are also possible via fake notifications sent by the hackers. A device infected with BingoMod can also be used to spread the malware via text message further.
Obfuscation and erasure
The malware also allows users to go undetected, disable installed security apps, delete them, or block their activity. This is done by code flattening and obfuscating strings, among other methods.
The BingoMod malware can also erase all activity on affected devices to hide its activities. This may happen after a successful (banking) transaction and only affects remote storage.
Finally, a remote command can also perform a full device wipe and reset settings on the affected Android device.
Also read: How Apple’s location API gives away Wi-Fi network data worldwide