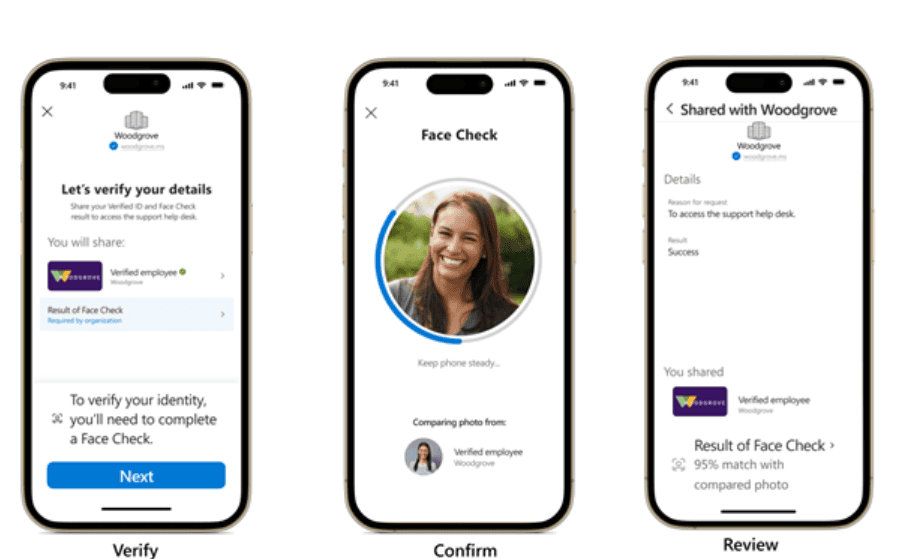
Microsoft’s Entra Verified ID will now offer facial recognition as a login method. This becomes possible now that the company makes Face Check technology generally available to business users. It can also be purchased as a separate solution.
Face Check should offer businesses a secure and simple login method. The authentication capability has recently been available as a separate solution and as part of the Microsoft Entra Suite.
The technology compares an employee’s uploaded photo in Verified ID with the person sitting behind the work laptop. Verification costs companies $0.25 per verification. It is also part of the Verified ID suite for premium users.
Source: Microsoft
Companies know who is logging in
Facial recognition is a solution to hacks that occur with stolen login credentials. According to Microsoft, this is a common problem: “Attackers use insecure login credentials in 66% of attack paths.” Most recently, Ticketmaster fell victim to a data breach in this manner.
Also read: Ticketmaster incident shows: attackers no longer break in, but log in
It also gives more security to companies that remotely onboard employees. For this method of work, deepfakes are a growing challenge. This is because it is increasingly difficult to verify through digital channels whether a person is who he or she claims to be. Even for tech companies, this is not always clear, as the North Korean infiltration at KnowBe4 showed.
