A new Linux malware rootkit, Pumakit, has recently surfaced that manages to surreptitiously hide on affected systems. For now, this rootkit, which consists of multiple components, only affects Linux versions older than 5.7.
In recent months, a new wave of Linux malware seems to have emerged. For example, the first UEFI bootkit for the open-source operating system, BootKitty, was recently discovered. Now it is the turn of Pumakit, which poses a new threat to Linux systems.
Pumakit was identified by Elastic in September after a suspicious upload to VirusTotal. This upload, a modified binary from cron, contained the rootkit. However, it remains unknown who is behind the malware and what specific targets were chosen.
Pumakit’s goal is clear: use advanced hiding methods and privilege escalation to disguise its presence on systems. Such techniques are often employed by attackers targeting critical infrastructures or business networks. They aim at spying, stealing financial data or disrupting processes.
Pumakit consists of multiple components, including a dropper, memory-resistant executables, a kernel module rootkit and a shared object (SO) userland rootkit.
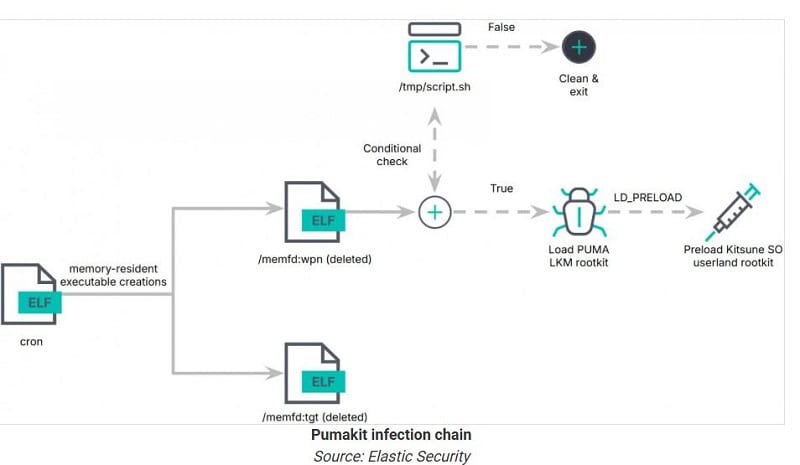
Attack path
The infection proceeds through a multi-step process, starting with a dropper called cron. This runs built-in malicious payloads such as ‘/memfd:tgt’ and ‘/memfd:wpn’ entirely from memory.
In the second stage, a payload runs in a so-called child process that performs system checks and manipulates kernel images. Finally, this stage loads an LKM rootkit module called puma.ko into the system kernel.
The kernel module contains a Kitsune SO component, a “userland” rootkit that injects itself into processes that use LD_PRELOAD. This allows the rootkit to intercept user-level system calls.
Hidden privilege escalation
At a later stage, Pumakit performs hidden privilege escalation. This is done via conditional activation, where the rootkit checks for specific kernel functions, secure boot status and other requirements before fully activating itself.
The userland rootkit Kitsune SO further extends hiding and control mechanisms to user levels. It intercepts system calls, hides files, processes and network connections associated with the rootkit, and can dynamically hide other files based on preset criteria. This makes malicious files completely invisible to end users and system administrators.
In addition, Kitsune SO handles communication with the C2 server. It receives commands, forwards them to the LKM rootkit and sends system information and configurations back to the attackers.
Only for older Linux versions
Pumakit uses the function kallsyms_lookup_name(), which can manipulate system behavior. This indicates that the rootkit specifically targets Linux versions older than 5.7. Newer Linux versions have removed this feature, preventing kernel modules from using it.
No fix is currently available for Pumakit. However, Elastic Security Labs did release a YARA rule that allows system administrators to detect the rootkit.
Also read: First UEFI bootkit ever built for Linux