ESET has discovered the first proof-of-concept UEFI bootkit malware for Linux: Bootkitty. This is the first time a type of UEFI bootkit malware has been developed for operating systems other than Windows and may pose a great danger.
Since 2012, UEFI bootkit malware has been persistent and often unremovable. It nests in the boot cycle and thus takes control of the operating system. This malware is often spread via firmware updates. Until now, so-called UEFI boot kits have targeted Windows without exception. A notorious example of this was BlackLotus from 2023.
Bootkitty Features
Bootkitty is a still rudimentary UEFI bootkit. It still contains numerous bugs and lacks important functionalities. The researchers state that it can only attack the Linux distribution Ubuntu. This is a proof-of-concept that has not yet been actively used for UEFI malware attacks.
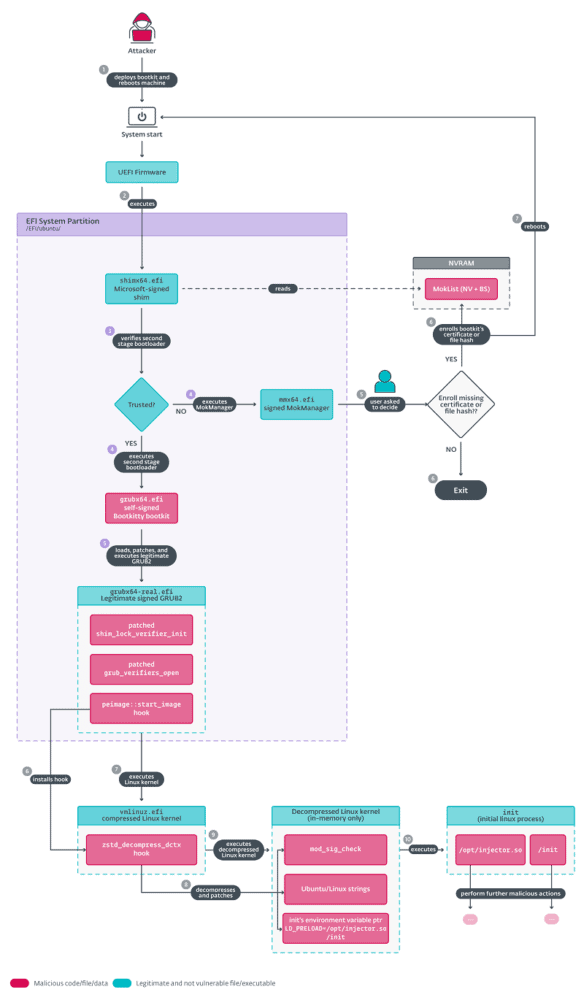
The UEFI malware aims to disable the Linux kernel’s signature authentication and load two unknown ELF binaries via the open-source operating system’s “init” process. This is the first process the Linux kernel executes while booting the affected system.
The bootkit is further designed to boot the Linux kernel seamlessly. Here, it does not matter whether UEFI Secure Boot protection is enabled or not. This is because the malware patches necessary functions in memory for integrity verification. This even before the so-called GRUB bootloader is booted.
During their analyses, ESET researchers discovered a possibly related unsigned kernel module from the same developer. This particular module loads a yet another unknown kernel module.
Big implications, but also good news
When hackers install the UEFI bootkit on a system, they can gain full control over it. The system is taken over during the boot process, and the malware can be executed before the operating system boots.
While Bootkitty is a very problematic development, there are also some positive comments. First, the malware cannot bypass the UEFI Secure Boot security mentioned earlier.
This security uses cryptographic signatures to ensure that the computer manufacturer trusts every piece of software booted during system booting. This prevents legitimate bootup software from being replaced by malware. If Secure Boot is not recognized, the system cannot boot.
A second advantage is that Bootkitty, although working for Ubuntu, still has many bugs and limitations that allow large-scale Linux infections. These bugs and imperfections, including in the way the bootkit modifies the decompressed Linux kernel, have caused systems to crash frequently so far, ESET specialists indicate.
ESET does warn that this new dangerous malware can quickly evolve into more stable versions that could be dangerous for all Linux distributions. There is still limited evidence of UEFI software for Linux being infected, so vigilance is advised.
ESET also expects security software for this particular malware to take off in the next few years.
Read also: CISA concerned about bootloader malware that makes your PC garbage